We can now enforce a Naming Policy for Office 365 Groups, lets give it a test drive.
With the Naming Policy feature we can define prefix or suffix that can be automatically added to group names and at the same time we can define words that are blocked from use in group names.
Note that Azure AD P1 license is required for the group creator, the group members, and the Naming Policy admin.
Setup is done by PowerShell and you need the Public Preview release of Azure Active Directory V2 PowerShell Module to be at least on version 2.0.0.137.
You can verify your current version with the commands:
Install-Module -Name AzureADPreview
Get-Module -Name AzureADPreview
You can just uninstall and reinstall the module to be sure you got the latest version. (elevated)
Uninstall-Module -Name AzureADPreview
Install-Module -Name AzureADPreview
Now login to the Azure AD tenant with the command.
Connect-AzureAD

And enter credentials (admin).
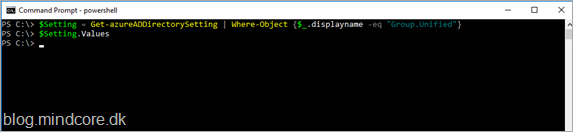
Start by getting the current group settings.
$Setting = Get-azureADDirectorySetting | Where-Object {$_.displayname -eq “Group.Unified”}
$Setting.Values
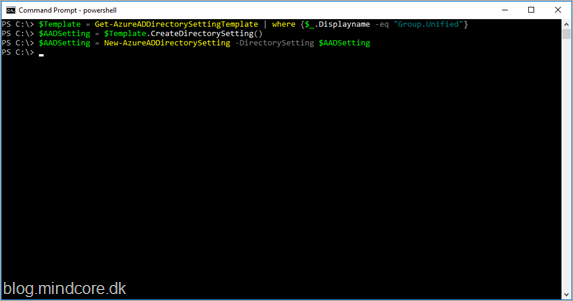
If nothing is returned like in the above screenshot, then we need to create the object before we can continue.
$Template = Get-AzureADDirectorySettingTemplate | where {$_.Displayname -eq “Group.Unified”}
$AADSetting = $Template.CreateDirectorySetting()
New-AzureADDirectorySetting -DirectorySetting $AADSetting
Lets get the current settings again and now we get data back, and as shown we don’t yet have a naming policy set.
$Setting = Get-AzureADDirectorySetting -Id (Get-AzureADDirectorySetting | where -Property DisplayName -Value “Group.Unified” -EQ).id
$Setting.Values
Now we can set the naming policy and custom blocked words.
$Setting[“PrefixSuffixNamingRequirement”] =”GRP_[CountryOrRegion]_[GroupName]_[Office]”
$Setting[“CustomBlockedWordsList”]=”Mindcore”
Set-AzureADDirectorySetting -Id (Get-AzureADDirectorySetting | where -Property DisplayName -Value “Group.Unified ” -EQ).id -DirectorySetting $Setting
The word Mindcore will not be allowed in the name, and the group name will be based of the users attribute values.
Supported Azure AD attributes are [Department], [Company], [Office], [StateOrProvince], [CountryOrRegion], [Title].
Lets again get the current settings and now we can see the policies.
$Setting = Get-AzureADDirectorySetting -Id (Get-AzureADDirectorySetting | where -Property DisplayName -Value “Group.Unified” -EQ).id
$Setting.Values
Final thing to do is to test the rules in teams.
We will create a new team.
Build a team from scratch.
I will create a private team.
I will call the team MyTeam, and in the preview below the name we can see what the final name will be based on our naming policy.
Team created with name as expected.
If we try with the blocked word Mindcore you will see the following warning.
Now test yourself.