Securing cloud services against attacks requires a strong focus on identities. This is because cloud services, normally, is available from anywhere and access is often based on the login only.
To address this threat, it is possible to implement extra layers to the login process, like Multi Factor Authentication. This effectively raises security but unfortunately lowers usability, which again leads to users turning to 3rd party services – not under corporate control.
To accommodate this concern, Microsoft has implemented Azure Active Directory Conditional Access in their identity stack. With Conditional Access it is possible to reach a high level of security, with very little impact on users.
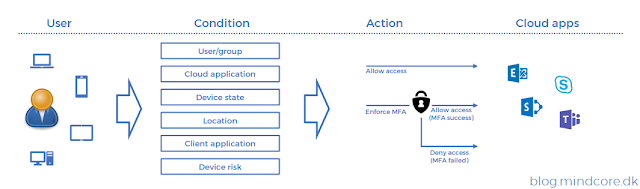
Conditional Access uses properties received from Azure AD during login and evaluates these against a set of conditions, to determine which access controls should be applied to a users login.
See flow in figure 1.
Figure 1 – Conditional Access flow
Policies
Conditional access is configured by creating policies and adding conditions to those policies. Policy creation is divided into two subcategories – assignments and access controls
Assignments
Assignments consists of users/groups, cloud apps and conditions.
Users/groups controls which user or groups the policy is assigned to, A policy can be assigned to users, groups or a combination of both and can include and exclude based on this. For instance, it is possible to include a group but exclude a single member of the group.
Cloud apps controls which cloud app the policy is applied to, so that it is possible to create policies for users accessing Exchange, SharePoint, Skype and so on. Cloud apps also contains a company’s own Azure apps.
Conditions consists of 5 subcategories:
- Sign-in risk – A condition based on info from Identity Protection. If Identity protection flags a login or a user’s credentials for high, medium or low risk, it can be taken into consideration.
- Device platforms – Controls if the login was done from an Android, iOS, Windows Phone, Windows or MacOS platform. It is possible to select all platforms.
- Locations – Controls if the login was done from a trusted IP or a location configured as company location (control is done by checking external IP the login comes from.)
- Client apps – Controls if the login comes from a browser, an app supporting modern authentication, exchange activesync or other clients. All of the Office suite supports modern authentication and is often used to ensure that company data only is held on applications where corporate restrictions can be enforced, like remote wipe.
- Device state – Controls if the device was done from a device that is Hybrid Azure AD Joined or marked as Compliant by intune.
Access controls
Access controls consists of grant and session.
Grant controls if the login should be blocked entirely or be granted access.
It is possible to require one or more controls before granting access. The available controls are multi-factor authentication, compliant device, hybrid azure ad joined device or login from an approved app.
As stated, it is possible to select one or more, so it is possible to create a policy that requires a device to be compliant AND require multi-factor authentication.
But it is also possible to select that only one of the controls should be performed, so that all compliant devices are granted access, but non-compliant devices are required to perform multi-factor authentication.
Session sends info to cloud applications that supports session controls, currently it is only Exchange online and Sharepoint Online that supports this. What it does is, it sends information to the cloud app informing if the client is compliant and/or hybrid azure ad joined, it is then possible to enable the cloud app to allow users a full or a limited experience based on that information.
Conclusion
Using conditional access enables corporations to achieve a high level of security by adding security layers when it is necessary, like logins from non-compliant devices, unknown locations or from unknown apps. But on the other hand, allows users from corporate controlled devices and company locations to login without any challenges.