Secure your Windows 365 Cloud PC(s) with Conditional Access and FIDO2 security keys.
Introduction
We have already written about FIDO2 security keys on several occasions (I will add the links below), which has inspired me to see how I could secure Windows 365 using Conditional Access and a FIDO2 security key.
The scenario is that I connect to my Windows 365 Cloud PC from personally owned devices at home and on the go. I want to embrace the future of passwordless authentication to achieve a higher level of security for my Windows 365 environment.
So, I will in this post walk you through how I secured my Windows 365 environment using Conditional Access and the FEITIAN AllinPass (K33) FIDO2 security key.
Our other blog posts about FIDO2 security keys.
– Passwordless using FIDO2 security key with HoloLens 2 by Mattias Melkersen
– Azure AD support for FIDO2 in hybrid environments by Lars Lohmann Blem
– Azure AD and password-less sign-in by Lars Lohmann Blem
As already mentioned, the security key used in this post is a FEITIAN AllinPass (K33) FIDO2 security key.

Source: FEITIAN Technologies
Prerequisites and Requirements
- Azure Active Directory (Azure AD)
- Azure AD Multi-Factor Authentication (MFA)
- Azure AD Conditional Access (CA)
- Enable Combined security information registration *
- Microsoft Endpoint Manager (MEM)
- Microsoft compatible FIDO2 security key
- For Azure AD joined devices, the best experience is on Windows 10 version 1903 or higher.
- Hybrid Azure AD joined devices must run Windows 10 version 2004 or higher.
- WebAuthN requires Windows 10 version 1903 or higher **
- To use Windows 365 Enterprise, each user needs a license for Windows 10 or 11 Enterprise, Microsoft Endpoint Manager (Intune), and Azure AD P1 (e.g., Microsoft 365 E3 + Windows 365 Enterprise 4 vCPU, 16 GB, 128 GB)
- Azure AD P1 license (Azure Active Directory Premium licensing)
- Microsoft Intune supported license (Microsoft Intune licensing)
- Windows 365 license (Microsoft Windows 365 licensing)
* Starting on August 15th of 2020, all new Azure AD tenants will be automatically enabled for combined registration. – More details about combined security information registration
** To use security keys for logging in to web apps and services, you must have a browser that supports the WebAuthN protocol. These include Microsoft Edge, Chrome, Firefox, and Safari.
Source: Microsoft
Supported FIDO2 security key providers
The following providers offer FIDO2 security keys that are known to be Microsoft compatible.

Source: Microsoft
Enable FIDO2 Authentication method in Azure AD
Let’s enable the FIDO2 security key as an authentication method in Azure AD.
Go to https://portal.azure.com
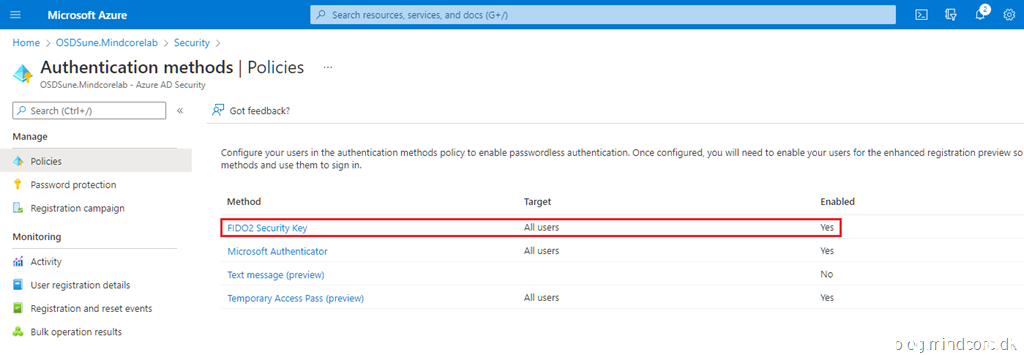
From Security in Azure AD, click Authentication methods.
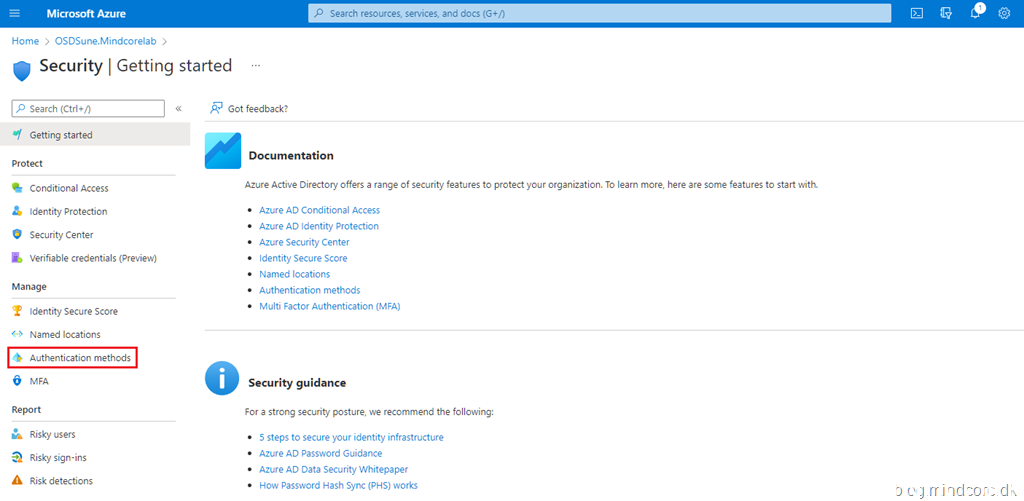
Click Policies and select FIDO2 Security Key.
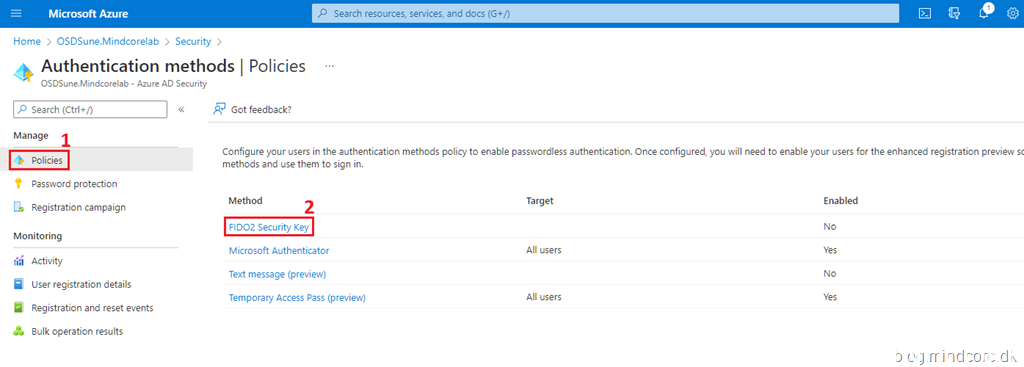
Set the settings as shown in the screenshot below.
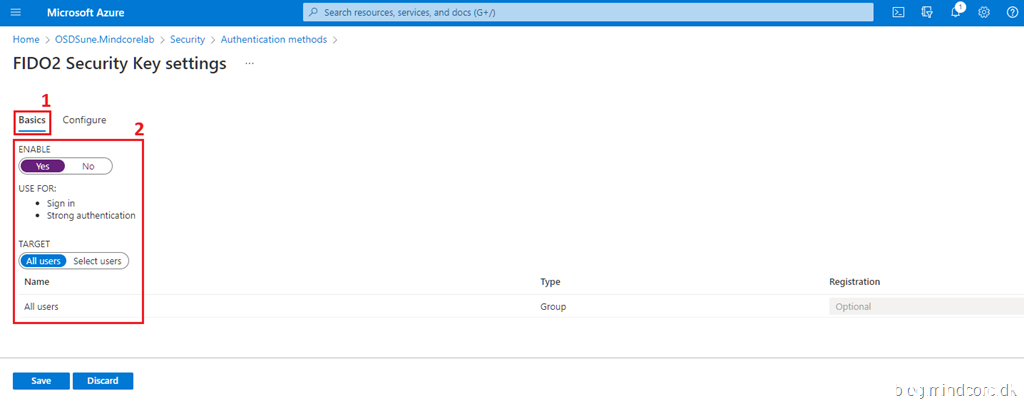
Go to the Configure tab, set the settings as shown in the screenshot below, and click Save.
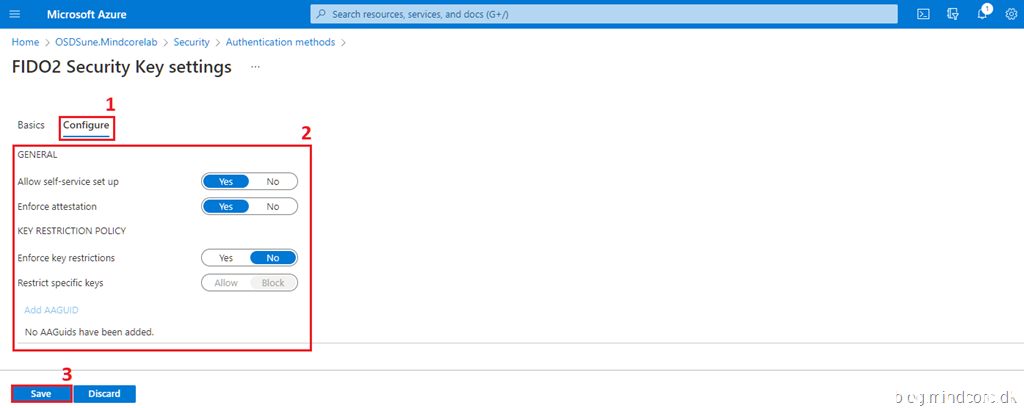
FIDO2 Security Key will now be available as an authentication method for all users.
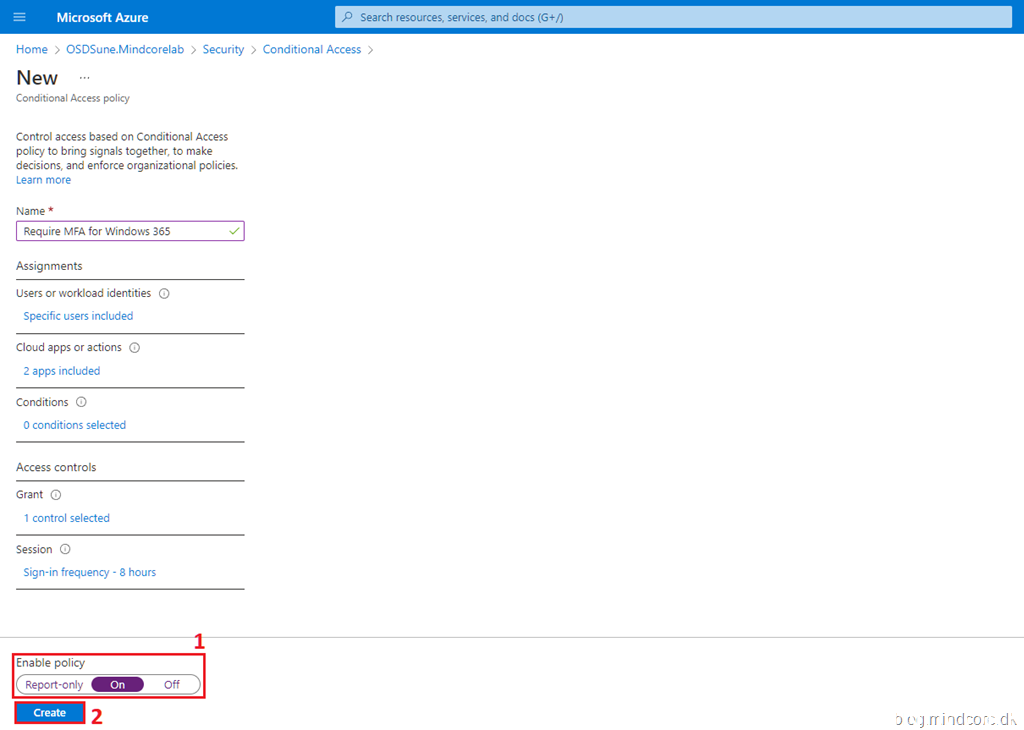
Create the Conditional Access policy in Azure AD
The end users can access their Windows 365 Cloud PC(s) in two different ways:
Let’s create a Conditional Access policy that will require MFA and set sign-in frequency for both cloud apps.
Go to https://portal.azure.com
From Security in Azure AD, click Conditional Access.
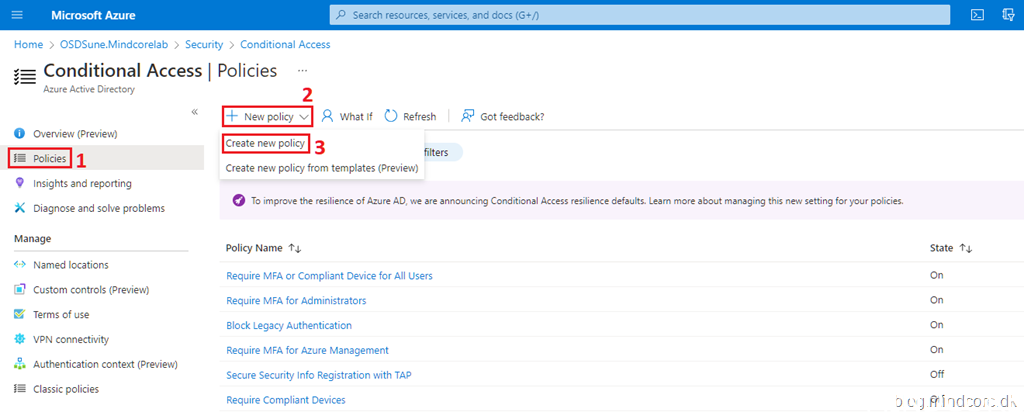
Click Policies | New Policy | Create new policy
Fill in the required Name field.
Click Users or workload identities and choose which users or groups to include in this policy. – For example, I selected an AAD group containing users eligible for a Windows 365 Cloud PC.
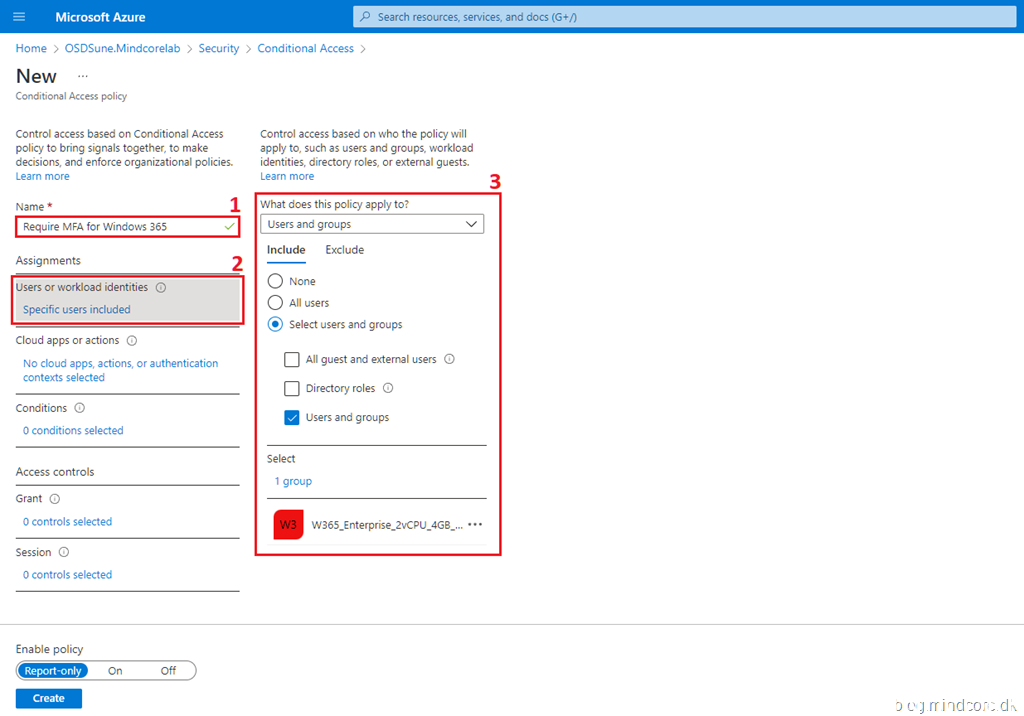
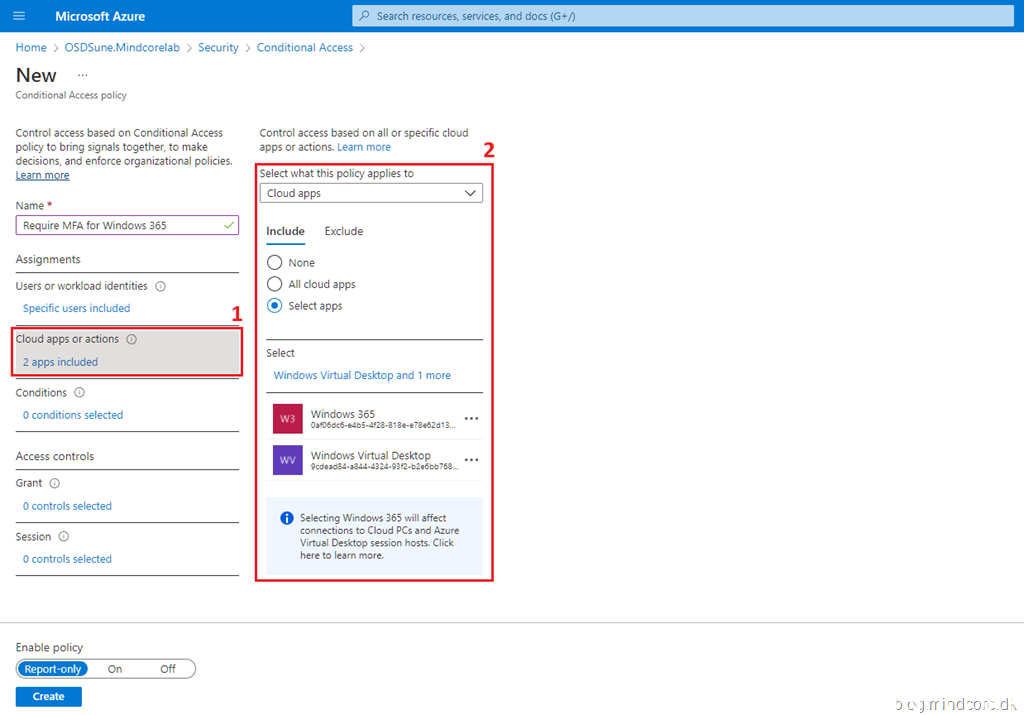
Click Cloud apps or actions and select the following two cloud apps:
- Windows 365 (Web Site)
- Windows Virtual Desktop (Remote Desktop App)
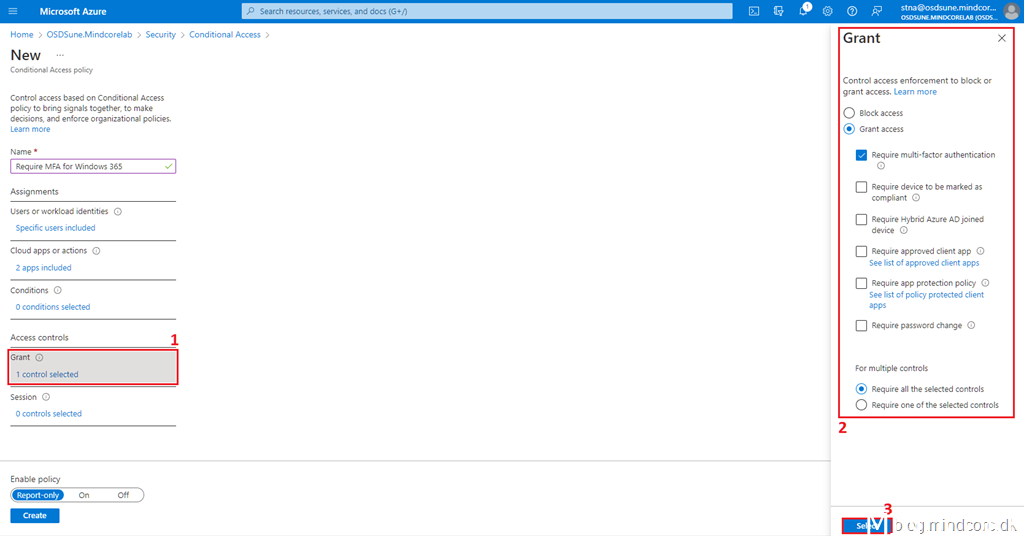
Click Grant, select Grant access, and tick the Require multi-factor authentication check box.
Click Select.
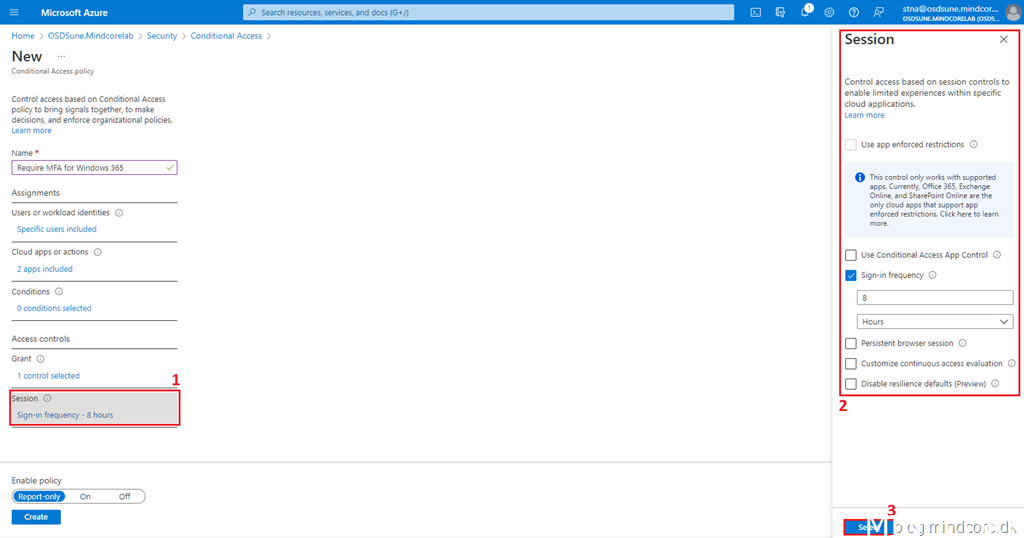
Click Session, and configure the Sign-in frequency. I chose 8 hours in my policy, which matches a typical working day.
Click Select.
Note. The Sign-in frequency is the period before a user needs to sign in again when attempting to access a resource. The default setting is a rolling window of 90 days.
Enable the policy and click Create.
Configuring the security key
Adding the security key (in this case, a FEITIAN AllinPass (K33) FIDO2 security key) to my physical device was straightforward and can be done with either USB-C, NFC, or Bluetooth. I chose to demo the Bluetooth option for this post, but I have also tested the USB-C option, and it works perfectly as well.
Important note. Before using the security key, you need to set up a PIN and enroll a fingerprint onto the security key. See also the security key manufacturer’s user manual for additional guidance. For example, to find out how to turn on the Bluetooth and pair it with your device.
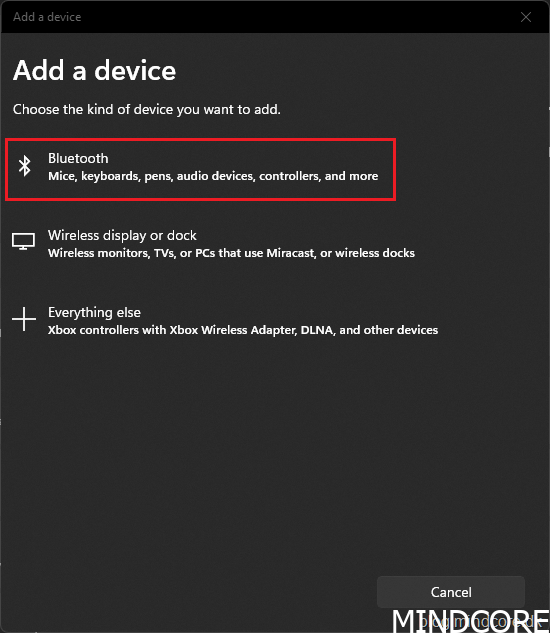
Windows 10 – Go to Windows Settings | Devices | Bluetooth & other devices and click Add Bluetooth or other device
Windows 11 – Go to Windows Settings | Bluetooth & devices and click Add device
Select Bluetooth and prepare the security key for pairing.
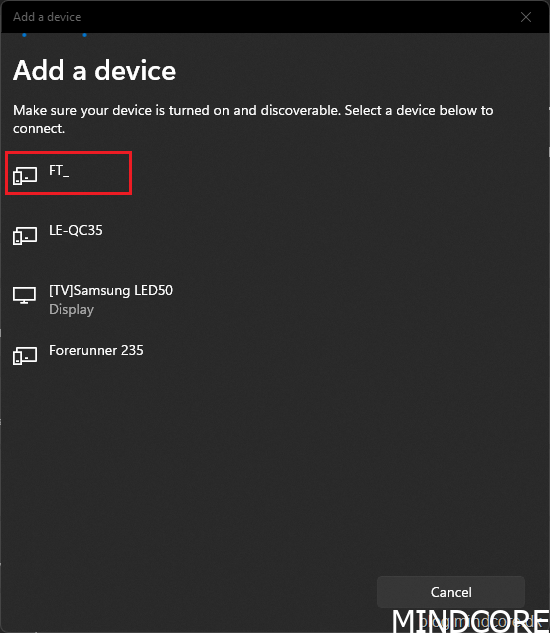
Select the security key when it appears in the list. (in this case, the device pairing name is FT_XXXXXX)
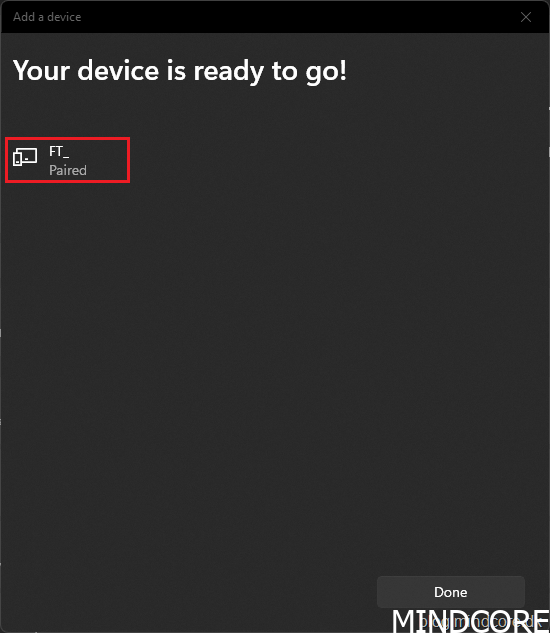
Once paired, click Done.
Go to Windows Settings | Accounts | Sign-in options | expand Security key and click Manage.
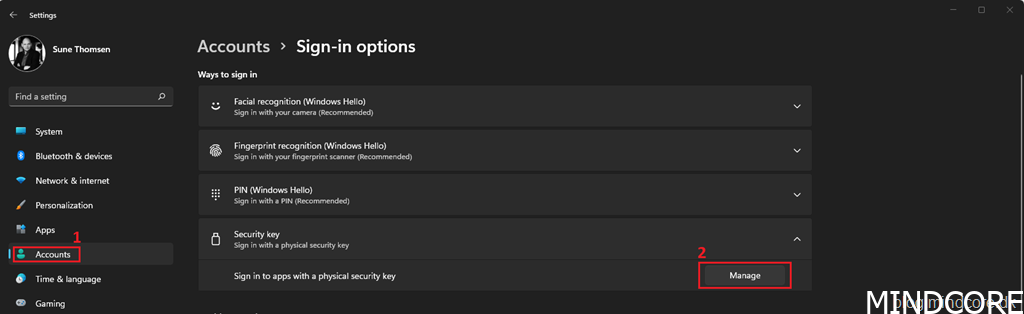
Turn on your Bluetooth security key or insert it into the USB port.
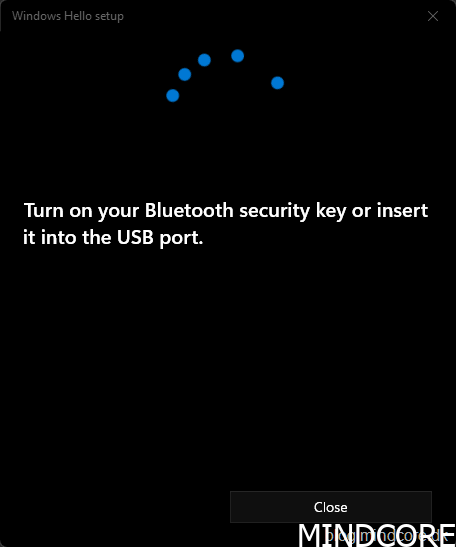
Tap the security key.
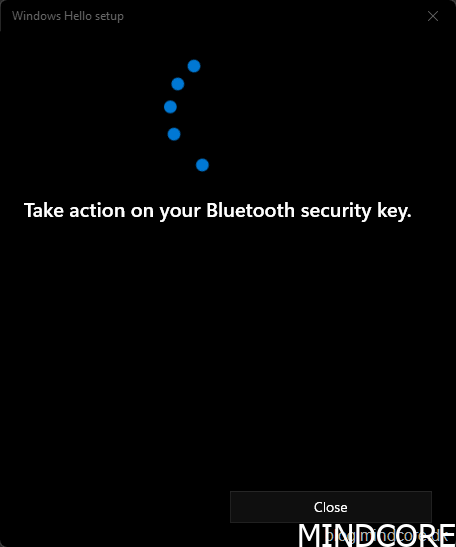
Click Add to create a PIN.
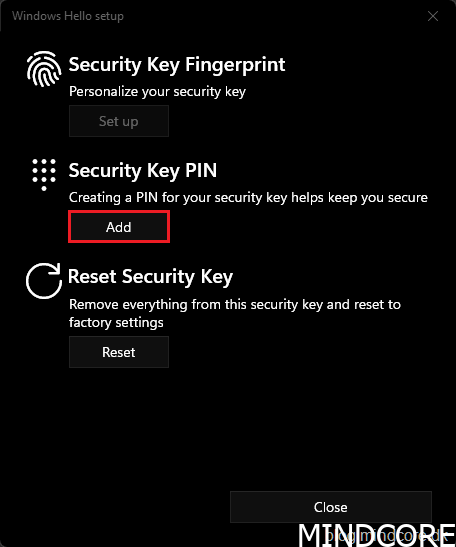
Set up a PIN and click OK.
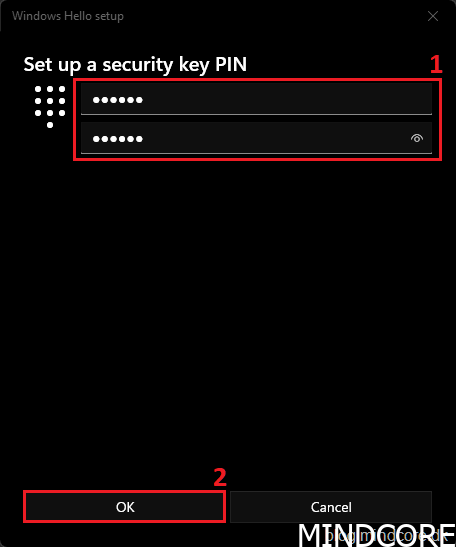
Click Set up to enroll your fingerprint(s).
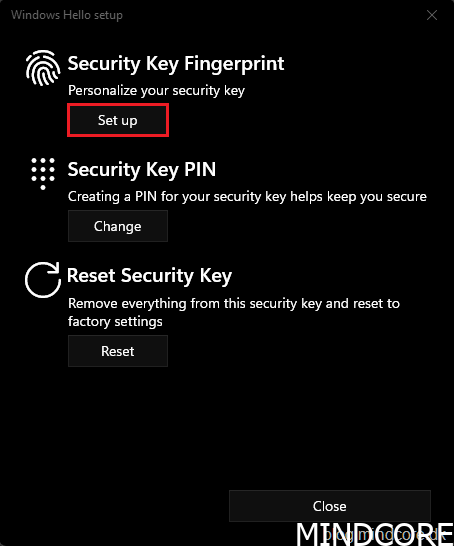
Enter the newly created PIN and click OK.
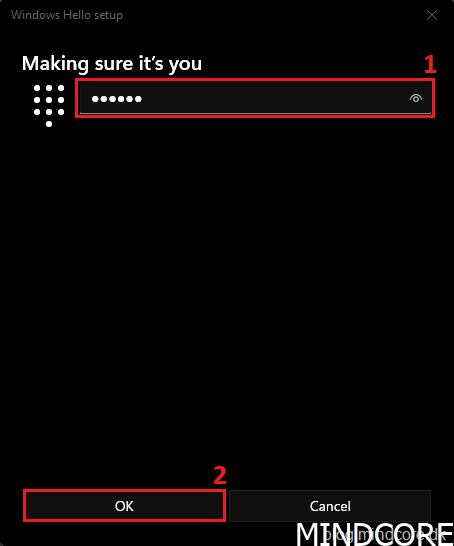
Enroll your fingerprint(s).
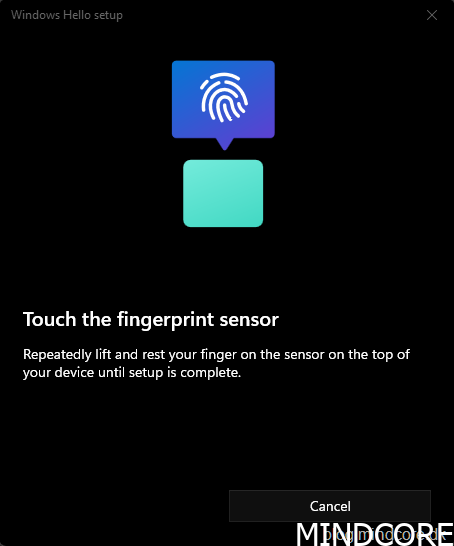
Click Done.
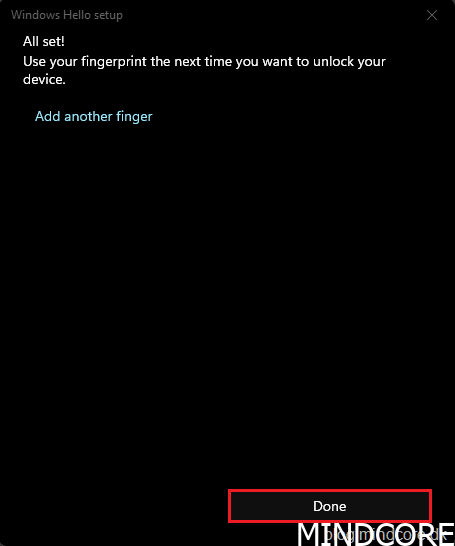
Click Close.
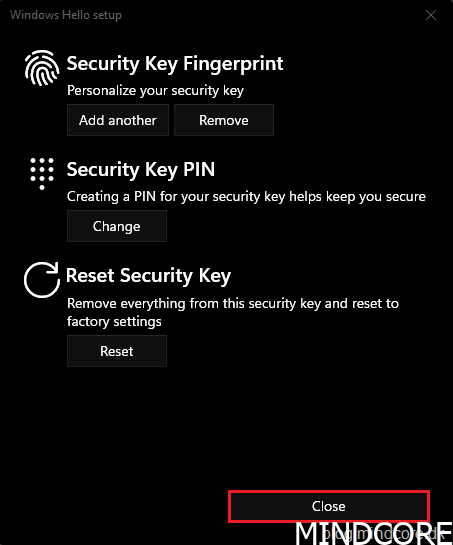
Register the security key to your Azure AD account
Once we have configured the security key, we can register it to our Azure AD account.
Go to https://aka.ms/mysecurityinfo or https://mysignins.microsoft.com
Click Security info | Add method | Choose a method and select Security key.
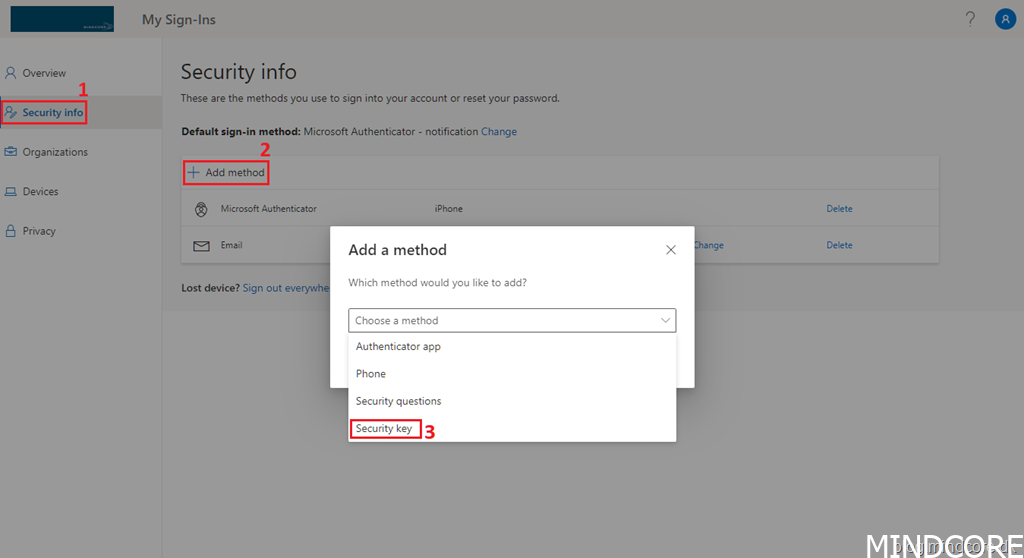
Click Add.
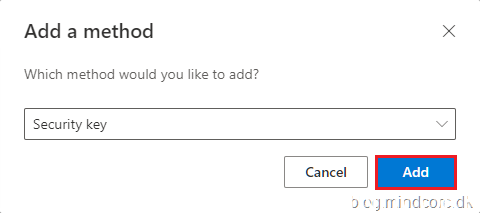
Select USB device.
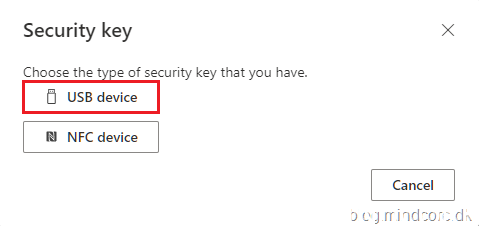
Click Next.
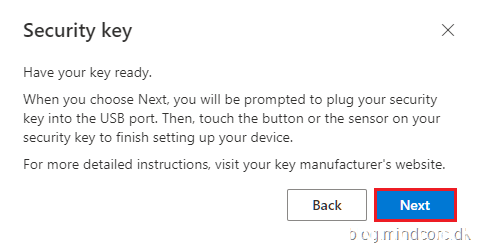
Click OK.
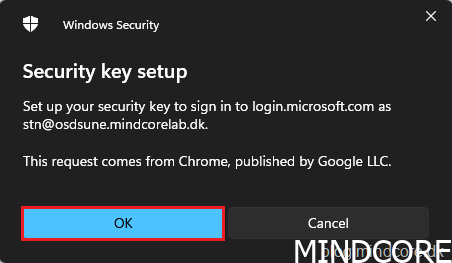
Click OK.
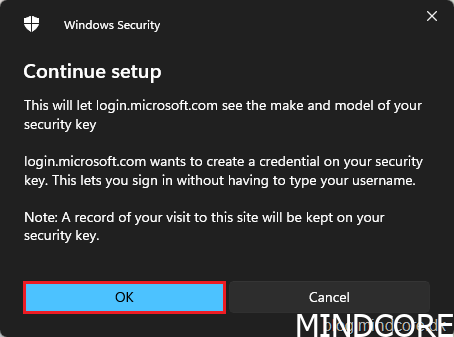
Turn on your Bluetooth security key or insert it into the USB port.
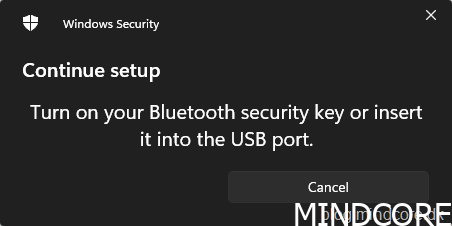
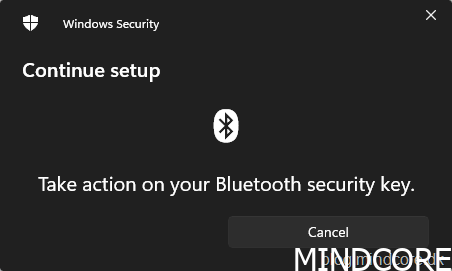
Rest your enrolled fingerprint on the security key sensor.
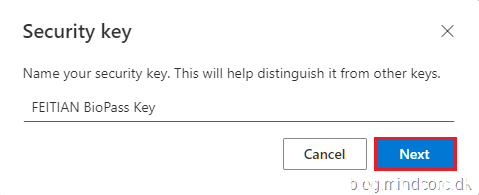
Name your security key and click Next.
Click Done.
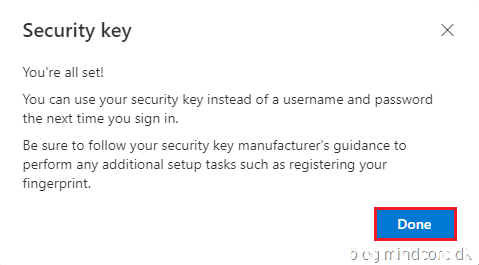
And the security key is now registered to your account as a sign-in method.
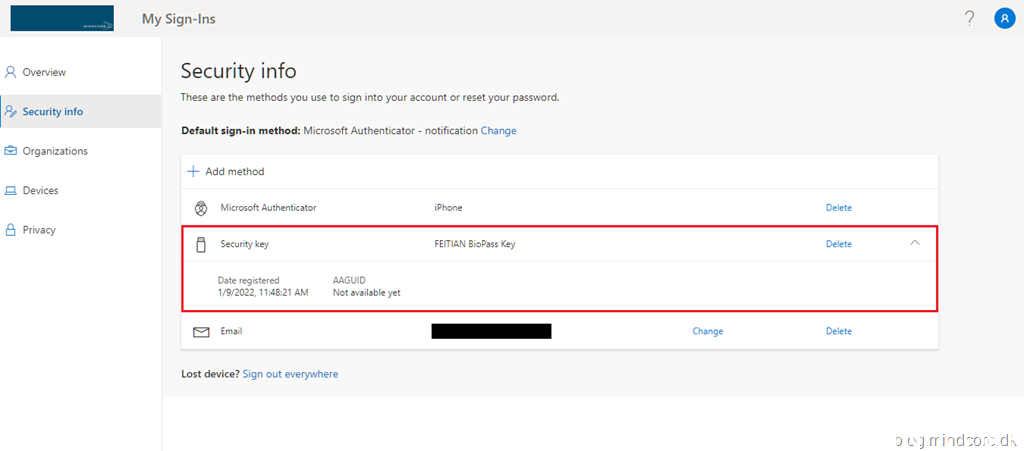
Security key sign-in experience
Once we have configured the Conditional Access policy and set up the security key, we are ready to test the Windows 365 Cloud PC sign-in experience.
Windows 365 Web Site
First, let’s try and sign in to the Windows 365 Web Site.
Go to https://windows365.microsoft.com
Click Sign-in options.
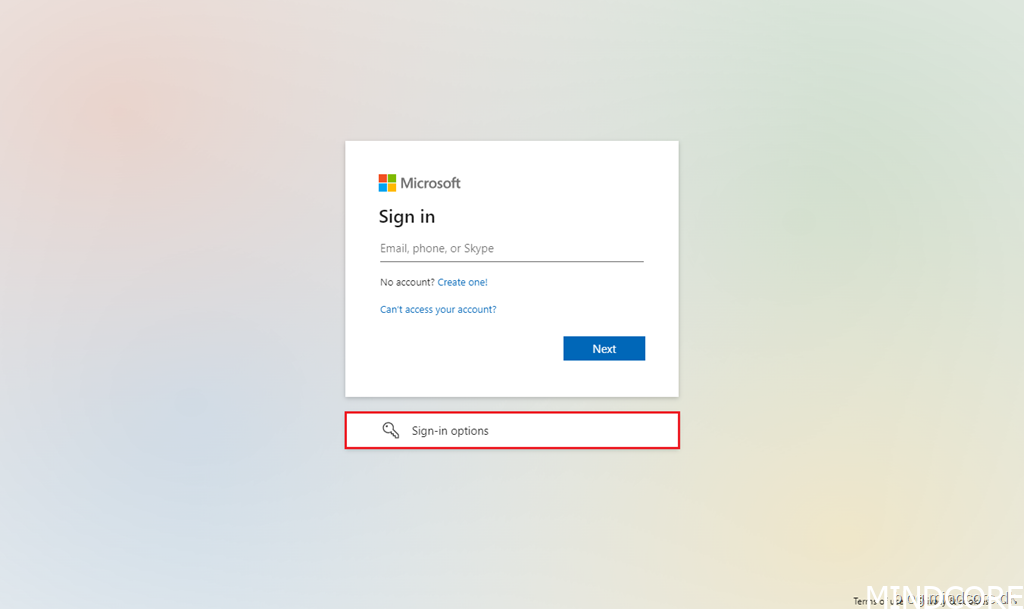
Select Sign in with a security key.
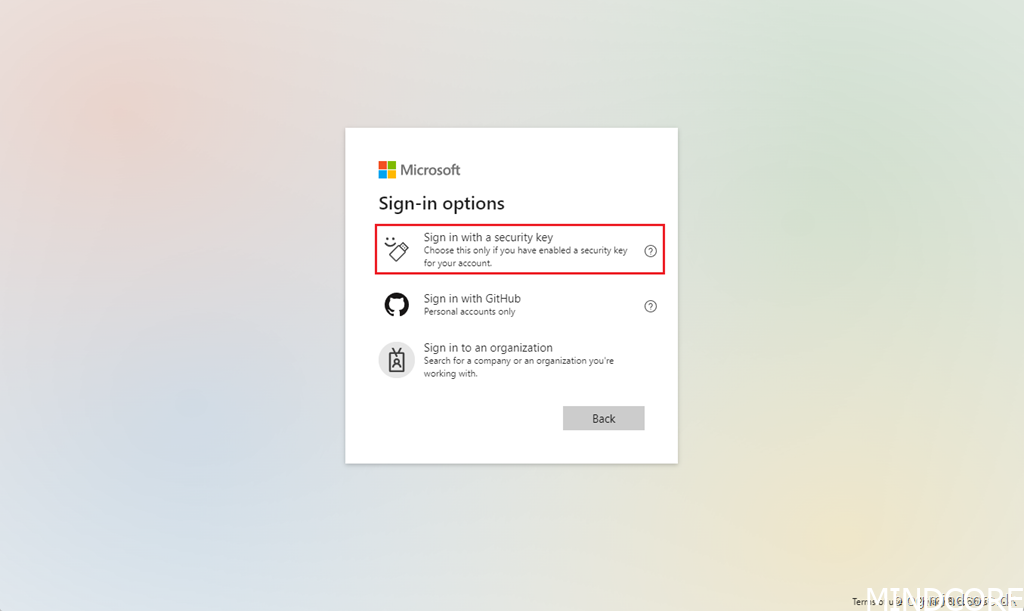
Turn on your Bluetooth security key or insert it into the USB port.
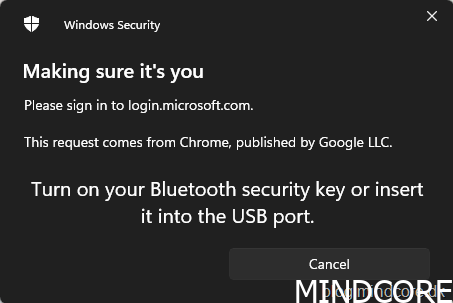
Rest your enrolled fingerprint on the security key sensor.
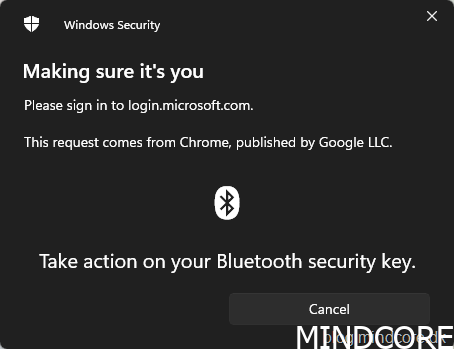
Click Open in browser.
We now see the usual sign-in prompt for the Windows 365 Cloud PC.
Enter your password and click Sign In.
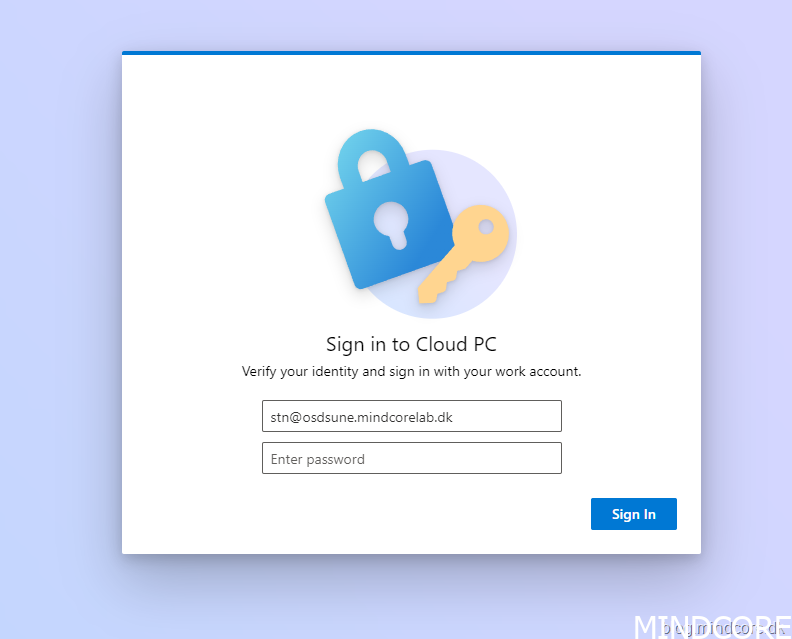
And we are signed in.
Microsoft Remote Desktop App
Next, let’s try and sign in to our Windows 365 Cloud PC using the Remote Desktop App.
Open Remote Desktop App.
Let’s look at my Windows 365 Cloud PC details. – Note the following status message “We need your sign in information to refresh this feed” that’s because the previous session has timed out due to the configuration I made in my Conditional Access policy, where I configured the sign-in frequency to be 8 hours.
Double-click on your Windows 365 Cloud PC or click Refresh in the details.
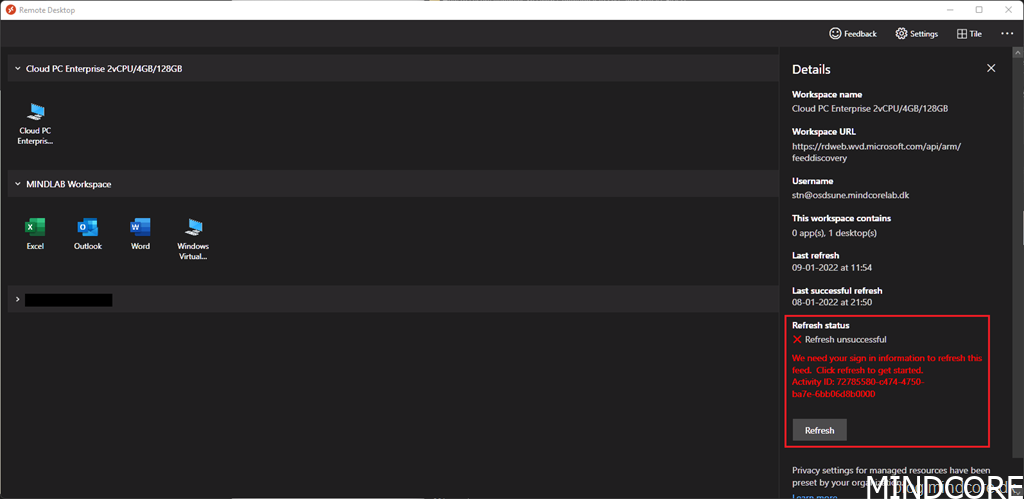
Select your account in the list.
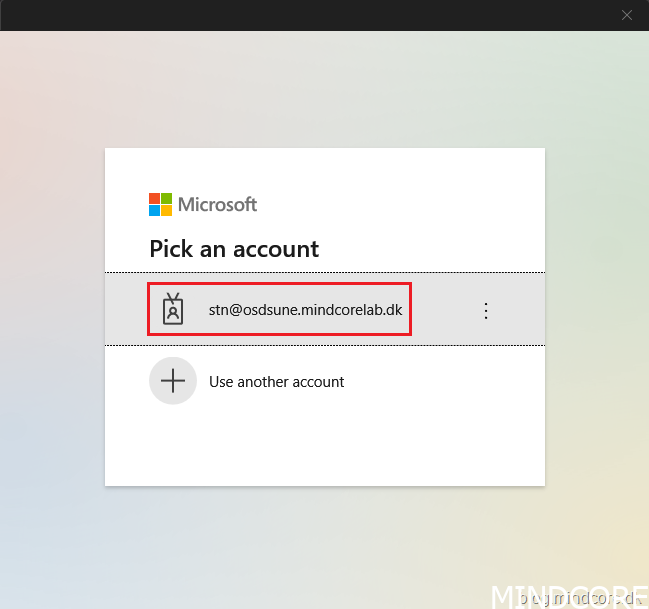
Turn on your Bluetooth security key or insert it into the USB port.
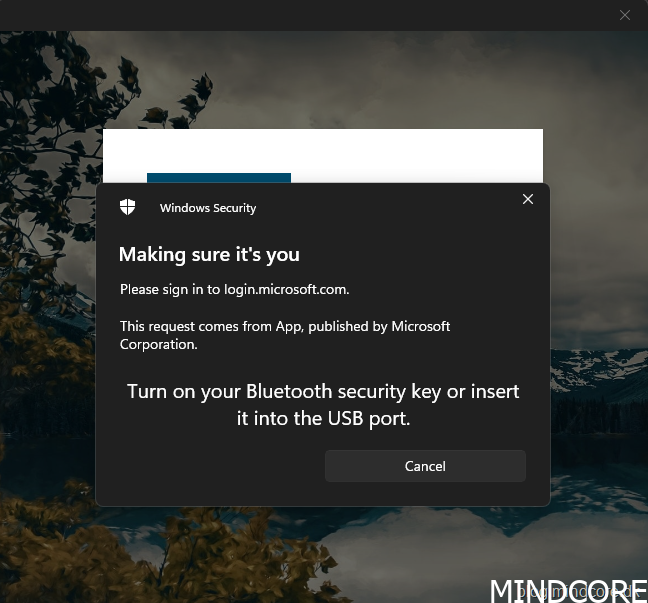
Rest your enrolled fingerprint on the security key sensor.
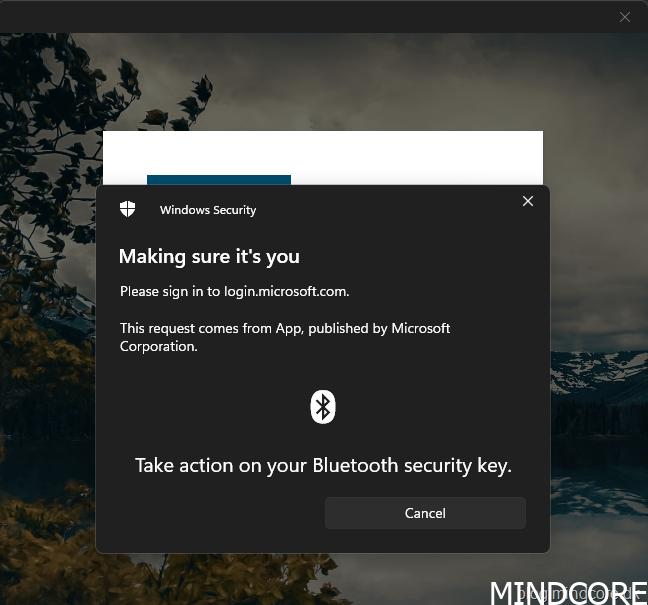
Once again, we see the usual Windows security prompt for the Windows 365 Cloud PC.
Enter your password and click OK.
And we are once again signed in. Awesome!
Sign-in details in Azure AD
Once we have completed the configuration, you probably want to know which authentication methods are used in your environment, right? You can find this information in the end user’s sign-in details and the authentication methods activity dashboard in Azure AD.
Go to Users in Azure AD and select a user.
Click Sign-in logs in the Activity section and choose an activity from the list.
Select the Authentication Details tab.
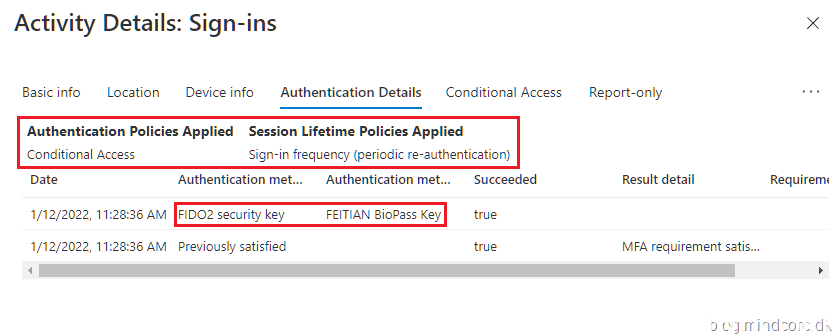
Go to Security in Azure AD and select Authentication methods.
Click Activity in the Monitoring section and choose the Usage tab.
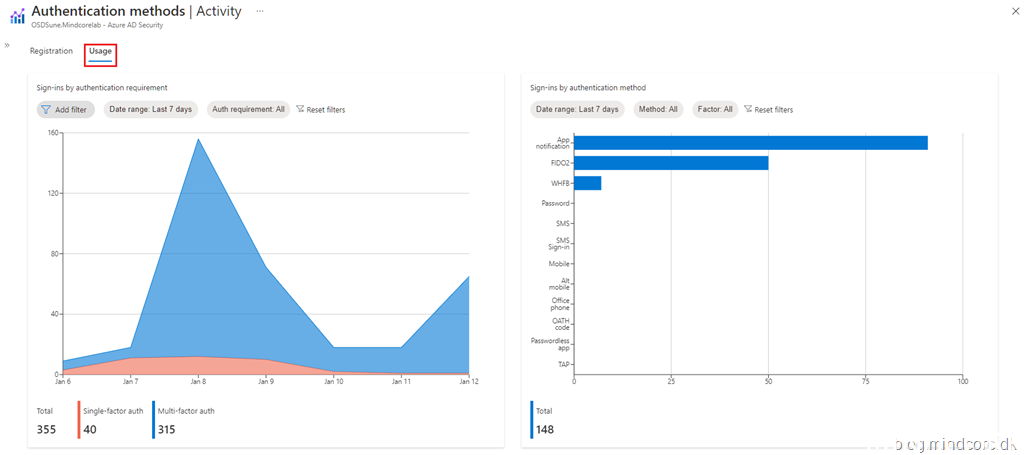
Summary
In this post, you learned how to secure your Windows 365 environment using Conditional Access and FIDO2 security keys. – Thanks to Della Han and FEITIAN Technologies for providing me with the security key used in this post.
Not only did I achieve a higher level of security for my Windows 365 environment by going passwordless. But it is also more convenient than Password + Two Factor Authentication, and I can access my applications and services much faster now (win-win).
The future is passwordless! – More details about passwordless
That’s all, folks. Happy testing!
As always, if you have any questions regarding this topic, feel free to reach out to us.
Sune Thomsen is based in Denmark, and he is a dedicated IT Consultant at Mindcore with over 19 years of experience in the IT industry. He has spent at least a decade specializing in client management via Microsoft Configuration Manager and Intune.
His key areas:
- Microsoft Intune (i.e., Autopilot, Windows 365, Endpoint Security, etc.)
- Client Management in general
- Application Management
- Cloud transitioning and building solutions toward the cloud
He's a Windows 365 and Windows MVP, an Official Contributor in a LinkedIn group with 41.500 members, and a Microsoft 365 Enterprise Administrator Expert.
Sune is passionate about community work and enjoys sharing his knowledge and experience and inspiring others via our blog. Besides blogging, he also writes newsletters on behalf of the Windows 365 community, does technical reviews for book publishers, and speaks at tech events.
Official Contributor here "Modern Endpoint Management":
https://www.linkedin.com/groups/8761296/














