Microsofts latest addition to the Information Protection ecosystem, allows for total control over corporate data and could for some companies allow for critical data to flow through the Office365 platform. But there are some caveats and before immersing into the solution we recommend being very aware of these. From the end-user’s perspective there is no problem using Double Key Encryption, the user will be presented with labels as usual and the user will only have to choose between tagging data or encrypting data, the number of encryption keys involved is not a choice.
Encrypting with Double Key Encryption is recommended for data with the highest level of privacy required and based on this, only a small part of a companies users, with access to that type of data, will need labels based on DKE.
So what is it?
Double Key Encryption (DKE) could be compared to Bring Your Own Key (BYOK) and Hold Your Own Key (HYOK) but is in fact a solution that is designed like a merge between the two.
BYOK allows for a key created by the company to be used and the purpose is to remain in control of data even in the event that the company changes cloud provider
HYOK allows you to use a key that is not controlled by your cloud provider, it requires a key store to be available to users, for protecting data before it is uploaded to the cloud. This allows for encryption of data with a key out of control of your cloud provider and would suffice for compliance for most companies, even regarding the CJEU judgment of the Schrems II lawsuit and you could ask yourself why every company isn´t implementing this feature then.
The caveats of the BYOK and HYOK is that BYOK is not really protecting data from the cloud provider and in the case mentioned where US controlled companies are not considered safe, this will not satisfy the goal of protecting data in Office365. HYOK protects data but requires control of keys and has a huge impact on the business in terms of the maintenance, availability, and security of keys. Bad performance on these parameters could mean inaccessibility of and ultimately loss of data. The solution could be to use a key provided by a key provider, which would solve the problem with the business impact in terms of availability and so on, but again it would allow for the serviceprovider to be able to gain access to data and so the problem has only been moved between providers.
DKE on the other hand requires the use of two keys instead of one. It uses the keys provided from Microsoft Information Protection and a second key provided by the business and encrypts with both. Again, it is possible to use a key from a key-provider to reduce the workload on business. This solves the problem with a single providers access to the encryption keys and in fact solves any issues regarding containing data in Office365.
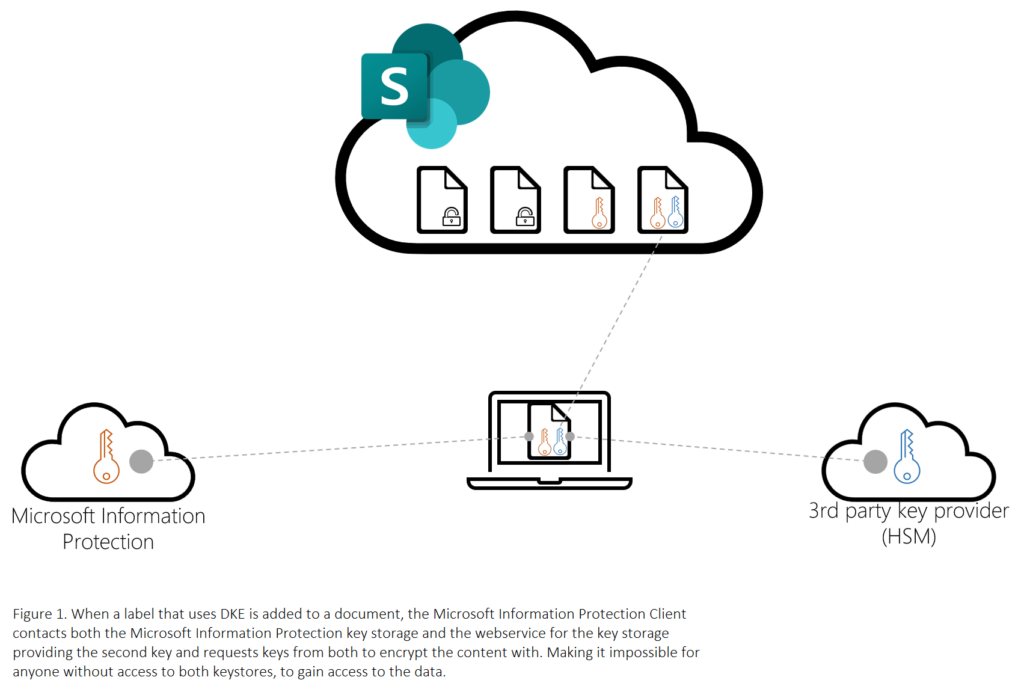
The caveats
So why not go ahead and encrypt all content using DKE. First of all, if the keys are to be provided by a key-provider or even if the company provides them, it comes with a significant cost. Also remember that one of the keys are not provided to Microsoft and therefore content encrypted with the 2 keys won’t be accessible by anyone but you. Which means that services like DLP, threat scan and so on won’t be able to scan the content. This in fact disables parts of the clouds security measures by letting these objects pass through without being scanned.
So one of the challenges is to recognize the data that could require this type of encryption and for most companies it will be a very small subset of data.
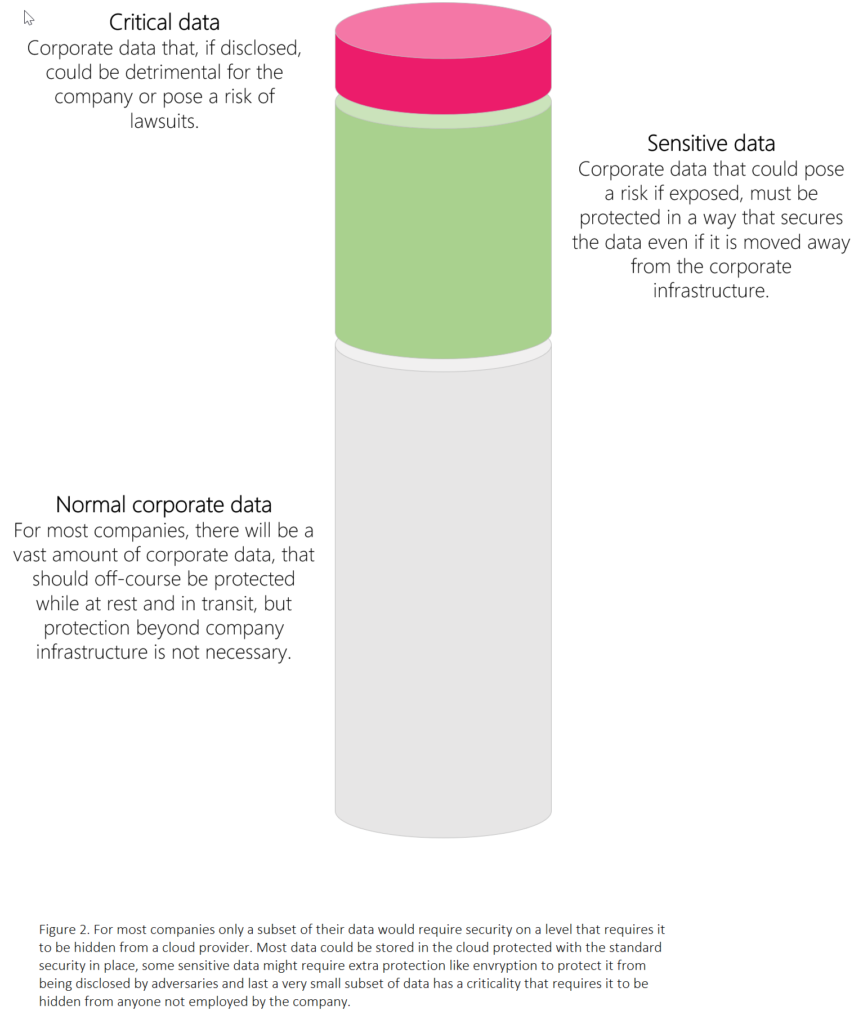
The above should make it clear that this is not a solution that fits all data, for most it will be a solution that can protect a very little amount of data, that otherwise couldn´t leave company controlled storage. So the big question is: Does any of your data require this level of security? If the answer is yes, then DKE is for you.
If you have any questions regarding DKE or any of the other data protection features of Microsoft365, please do no hesitate to reach out to us.













