So, for the ones who thought that MFA was the holy grail, bad news has arrived. Microsoft is seeing a rise in attacks based on AiTM – Adversary in The Middle. Unfortunately, these attacks have proven that MFA is not enough to protect users against credential theft, because they leverage a mechanism where users session cookies are used.
The attack
The attack requires the user to login to a server that proxies the user’s login to a Microsoft endpoint. The proxied login is through a server that saves the session cookie and enables the attacker to re-use the session cookie to login to company ressources.
This type of attack allows an attacker to obtain a session cookie that can be used to circumvent MFA AuthN. The attack steps are illustrated in the figure below.
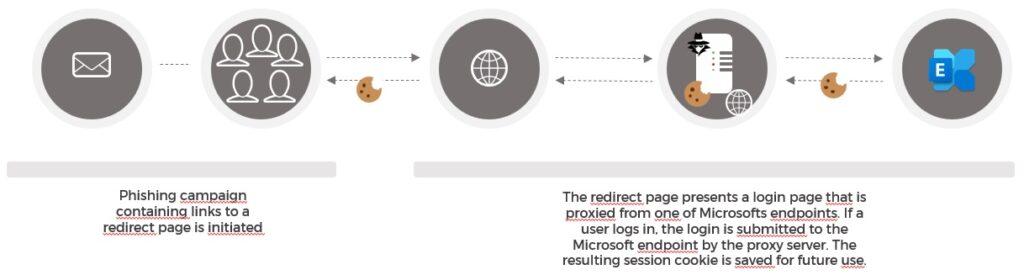
How to prevent these types of attacks
The easiest way to protect against these types of attacks are by leveraging Conditional Access policies that only allows logins from trusted IP addresses or devices that are trusted/compliant. This will solve the issue but will also reduce users access to services, so it is recommended to test before implementing these policies.
Another way to protect against these types of attacks is to enable certificate-based sign-in or use Fido security keys for sign-in, but this requires a lot of planning and testing.
As always reach out if you want us to assist.













