It’s been almost a year since I published my original post about how to migrate BitLocker Recovery Key(s) to Azure AD (Microsoft Entra ID) using a remediation script. It didn’t take long before several companies started using it, and since then, I’ve received a few inquiries about support for multiple fixed drives.
Today, I’m excited to announce the release of an updated version of the remediation script, which supports multiple fixed drives and an improved script output in Microsoft Intune.
BEFORE YOU BEGIN
Read about the prerequisites and requirements for remediation scripts in Microsoft Intune and the script usage in the original blog post here ⤵️
In this post, I’ll cover the following topics.
- Migrate BitLocker key(s) from all fixed drives
- Remediation verification
- The improved script output in Microsoft Intune
- Summary
Migrate BitLocker key(s) from all fixed drives
Important
Please download the detection and remediation script from my GitHub repository before continuing.
In the variables section of both scripts, you will find a new global variable named $Global:CheckAllDrives with a default value set to $false (see the screenshot below)
- If set to $false (default) – the script will only check the system drive.
- If set to $true – the script will check all fixed drives.
So, if you want to check all fixed drives on your devices, change this new global variable to $true in both the detect and the remediation script and upload them to Microsoft Intune.
Note
As stated in my original blog post, you still need to change the “CompanyName” in the registry path to a name of your choice (such as your company name).
Tip
Although changing the event log time variable is optional, I suggest you change it to the date you plan to put the scripts into production.

Remediation verification
After uploading both scripts to Microsoft Intune, it’s time to verify that everything works as intended.
The first place I will check is in the IntuneProactiveRemediation log file.
C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\IntuneProactiveRemediation.log
As you can see in the example below, the script checks drive C:, E:, and F:

The second place I will check is in the Event Viewer.
Applications and Services Logs | Microsoft | Windows | BitLocker-API | Management
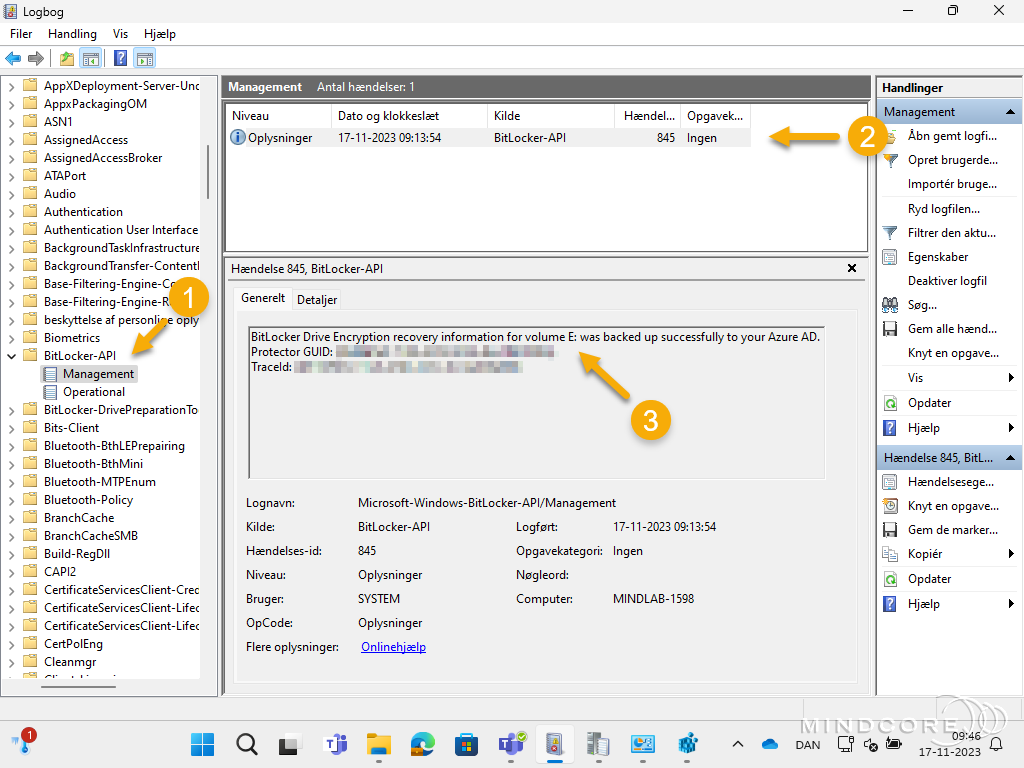
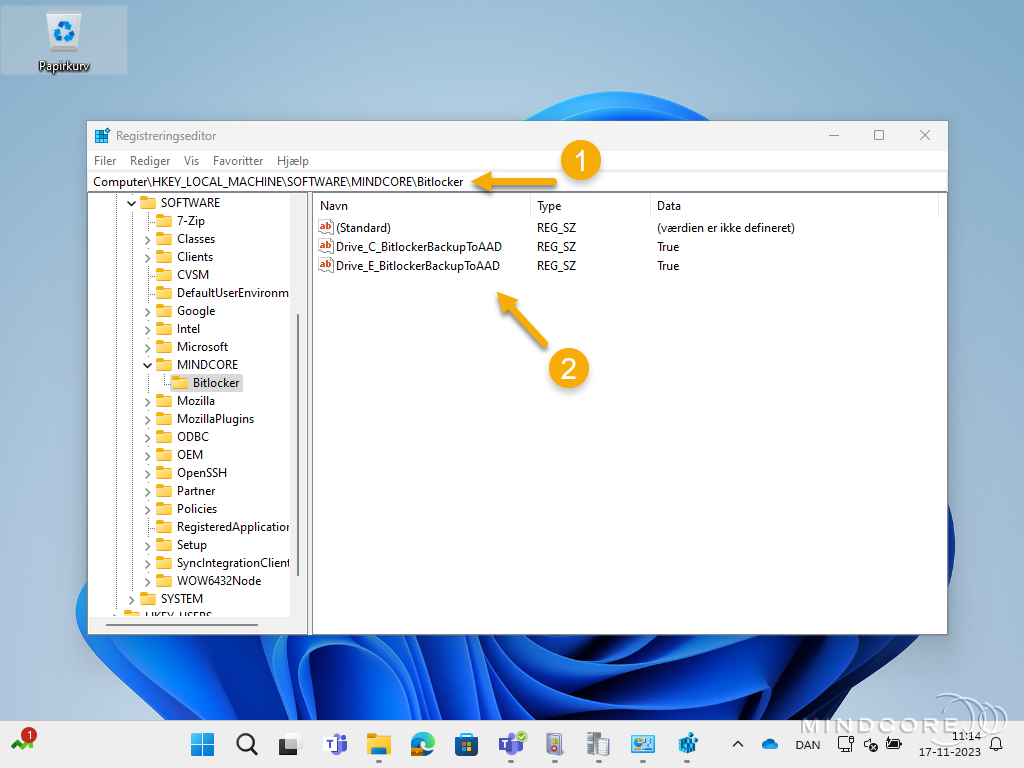
The third and final place I would check is in the Registry Editor.
HKEY_LOCAL_MACHINE\SOFTWARE\CompanyName\BitLocker
The improved script output in Microsoft Intune
Let’s have a look at the improved script output in Microsoft Intune.
Go to https://intune.microsoft.com
Next, go to Devices | Remediations (under Policy) and select your script package from the overview.
Choose Device status (under Monitor) in the script package.
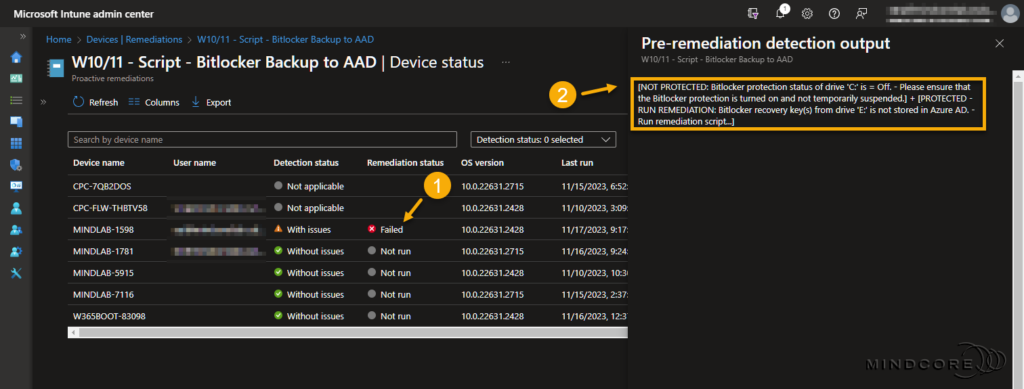
The Device status overview provides visibility into the detection and remediation status. The following example shows that the detection process finished with issues, and the remediation failed.

Let’s look at what information the output can provide us. In the below example, we can see that the improved script output now supports multiple outputs!
- Output 1 – BitLocker protection status of drive ‘C:’ is = Off. – Please ensure that the BitLocker protection is turned on and not temporarily suspended.
- Output 2 – BitLocker recovery key(s) from drive ‘E:’ is not stored in Azure AD. – Run remediation script…
Note
The script output(s) are separated with [Output 1] + [Output 2] + [Output 3]…
Why did the remediation fail? – Because I’d temporarily suspended the BitLocker protection on drive C:
Summary
In this blog post, you learned about the new capabilities of my remediation script used for migrating BitLocker key(s) to Microsoft Entra ID. You should now be able to upload BitLocker key(s) for all fixed drives to Microsoft Entra ID and check the improved script output in Microsoft Intune.
That’s it, folks. Happy testing, and have fun exploring 🤓
If you have any questions regarding this topic, please feel free to reach out to us.
Sune Thomsen is based in Denmark, and he is a dedicated IT Consultant at Mindcore with over 19 years of experience in the IT industry. He has spent at least a decade specializing in client management via Microsoft Configuration Manager and Intune.
His key areas:
- Microsoft Intune (i.e., Autopilot, Windows 365, Endpoint Security, etc.)
- Client Management in general
- Application Management
- Cloud transitioning and building solutions toward the cloud
He's a Windows 365 and Windows MVP, an Official Contributor in a LinkedIn group with 41.500 members, and a Microsoft 365 Enterprise Administrator Expert.
Sune is passionate about community work and enjoys sharing his knowledge and experience and inspiring others via our blog. Besides blogging, he also writes newsletters on behalf of the Windows 365 community, does technical reviews for book publishers, and speaks at tech events.
Official Contributor here "Modern Endpoint Management":
https://www.linkedin.com/groups/8761296/














