In this blog post, I will explore the concept of Windows 365 Boot, a unique feature that complements Windows 365 Frontline well. Windows 365 Boot became generally available (GA) in September 2023 and is revolutionizing the way users can access their Cloud PCs.
Source: Microsoft Designer
So, buckle up for my next venture, and let’s look at what this relatively new feature is all about and which use cases it covers. Also, let me show you how to configure Windows 365 Boot and how we can restrict user access on the physical Windows 365 Boot device.
In this post, I’ll cover the following topics.
- Prerequisites and Requirements
- What is Windows 365 Boot?
- The Use Cases of Windows 365 Boot
- How to Configure Windows 365 Boot
- Test and Verification
- Restrict User Access
- Summary
Prerequisites and Requirements
- Windows 11-based devices (Pro & Enterprise).
- The physical device (and Cloud PCs) must be running Windows 11 version (22621.2361 or later).
- You must have a valid and working Microsoft Entra and Intune tenant.
- You must have a Windows 365 Cloud PC license to access the Windows 365 Boot guided scenario.
- You must use Microsoft Intune to manage your Windows 365 Boot devices and policies.
- Microsoft Intune Administrator rights.
What is Windows 365 Boot?
Windows 365 Boot lets IT admins configure Windows 11 physical devices so that users can sign in directly to their Cloud PC from the physical device’s Windows 11 login screen, making it the primary Windows experience on the device with no additional steps. Signing out of the Cloud PC will return the physical device to the Windows 11 login screen – ready for the next user. This makes the Windows 365 Boot a great feature, especially when combined with Windows 365 Frontline, and for users who work shifts and share physical devices.
– So, we are basically turning the physical device into some sort of a thin client based on Windows 11.
What’s New for Windows 365 Boot
Microsoft announced these new features when Windows 365 Boot was made generally available:
Bluetooth
Now, users can seamlessly fine-tune their Bluetooth settings straight from their Windows 11 device with Windows 365 Boot.
Bluetooth Support
To connect to Bluetooth devices from your Windows 365 Boot Cloud PC:
1. Open Quick Settings | Bluetooth.
2. In the Settings window, pair and connect to Bluetooth devices.
Multiple Cloud PCs
End users have the power to handpick their Cloud PC of choice, making personalization a breeze.
Multiple Cloud PCs
To set a default Cloud PC to use each time you sign in:
1. Navigate to https://windows365.microsoft.com
2. In the card for the Cloud PC you want to set as default, select the ellipses (…) | Settings.
3. In the Integrated experiences tab, under Boot to this Cloud PC, select Connect while signed in to device.
4. Select Update.
Windows 365 Frontline Cloud PCs
IT admins can configure Windows 365 Boot with their Windows 365 Frontline licenses.
Max Connection Timeout Preferences
IT admins can now set the max connection timeout between 5 and 20 minutes based on their needs.
Security Baseline Profiles
IT admins can now configure their security baseline profile on the Boot device recommended by Microsoft as part of their Guided Scenario.
Source: Windows 365 Boot is now generally available!
Upcoming Features and Improvements for Windows 365 Boot
The following improvements are beginning to roll out for Windows 365 Boot:
Dedicated mode for Windows 365 Boot
We are now launching a new mode for Windows 365 Boot – dedicated mode. You can now boot to your Windows 365 Cloud PC from your designated company-owned device. You will be able to seamlessly login to your Windows 365 Cloud PC from Windows 11 login screen using password-less authentication methods like Windows Hello for Business. The new dedicated mode also comes with fast account switcher experience to effortlessly switch profiles to login in, personalized experience with your username and password, display picture on lock and login screen, remember your username, etc.
The feature will begin to get enabled for Windows 365 customers via a private preview in early 2024.
Customized company logo and name for Windows 365 Boot
In shared mode, organizations can now customize the login page to include their company branding from Intune.
The feature will begin to get enabled for Windows 365 customers via a private preview in early 2024.
Fail fast mechanism for Windows 365 Boot
You no longer need to wait for the sign in process to the Cloud PC to complete only to find out Windows 365 Boot failed due to network issues or incomplete setup. The smart logic proactively informs users to resolve network issues or complete app setup so users can experience a smooth login to their Cloud PC.
Manage local PC settings through Windows 365 Boot
With this feature, it is now easier for you to access and manage sound, display, and other device specific settings of their local PC directly from your Cloud PC in under Windows 365 Boot.
Source: Announcing Windows 11 Insider Preview Build 22635.2915 (Beta Channel)
The Use Cases of Windows 365 Boot
Who would benefit from the Windows 365 Boot feature? Well, I could definitely see this as an ideal solution for hospitals, retail stores, or call centers, especially when combined with Windows 365 Frontline.
Note: Want to learn more about Windows 365 Frontline? See The Concept of Windows 365 Frontline.
Why, you ask? – It’s because Windows 365 Boot targets the same type of workers, such as nurses, salespeople, and other professionals who share company physical devices. Such kinds of workers might frequently switch between physical tasks and computer-based interactions. Windows 365 Boot lets them bypass the lengthy startup process and boot directly into their Cloud PC to continue their work right where they left off.
How to Configure Windows 365 Boot
Now that you know the concept behind Windows 365 Boot let me show you how to set this up using the guided scenario in Microsoft Intune. We start by creating a security group for our Windows 365 Boot devices. Next, we’ll create the resources required for Windows 365 Boot to work via the guided scenario and prepare each physical device for the transition.
Windows 365 Boot Guided Scenario
Go to https://intune.microsoft.com
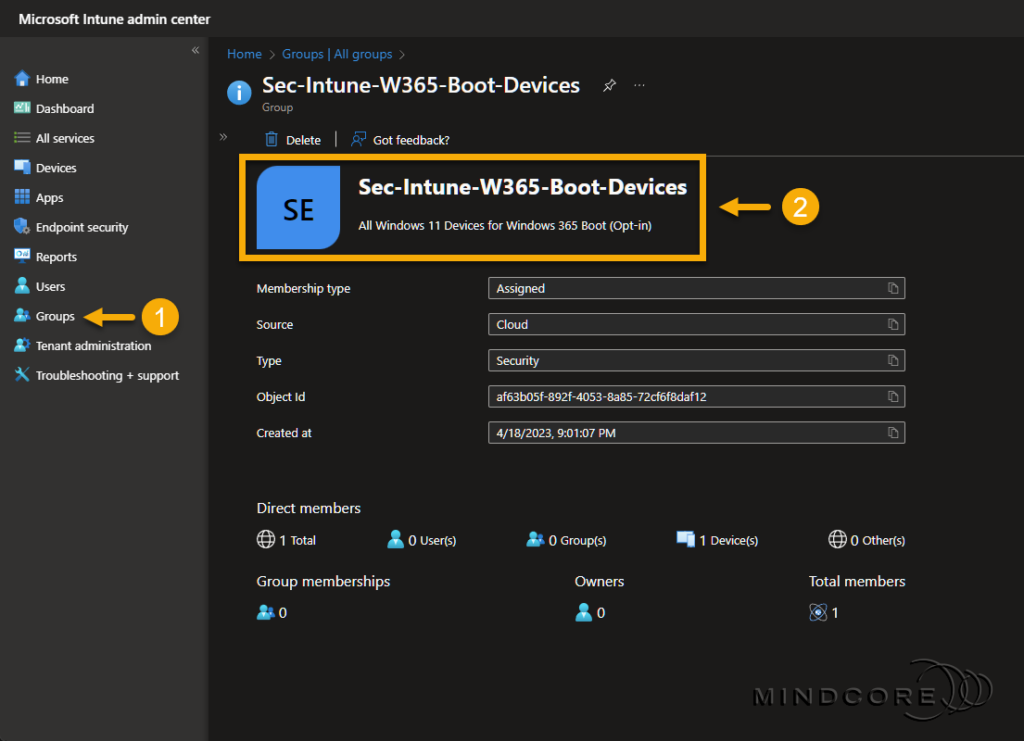
In the left pane, select Groups.
Create a new Microsoft Entra ID security group for the Windows 365 Boot devices. – The group can be based on direct or dynamic membership.
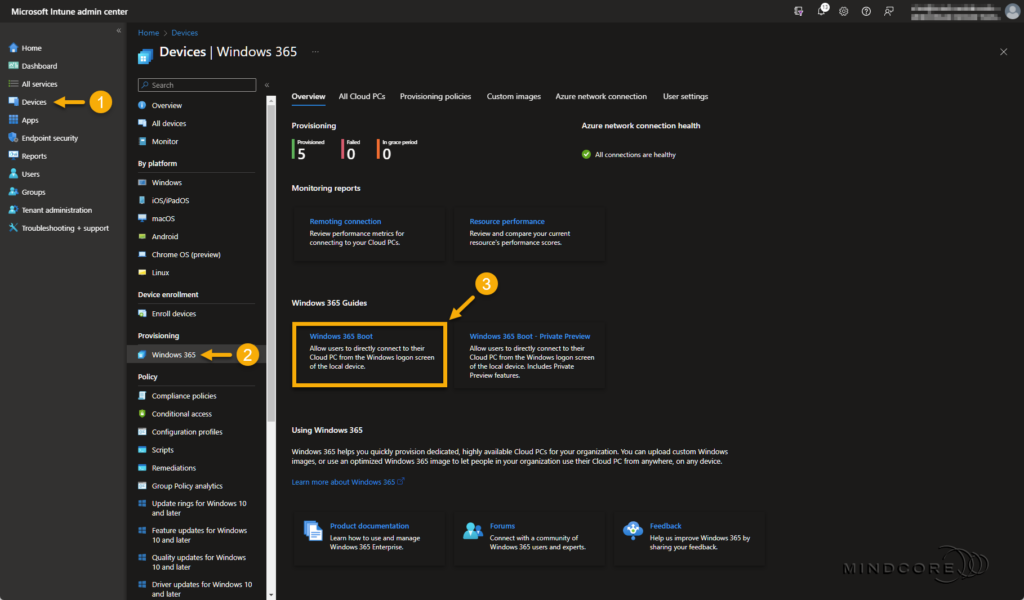
Next, select Devices | Windows 365 (under Provisioning) to start the Windows 365 Boot guided scenario.
Click Next to begin the guided scenario.
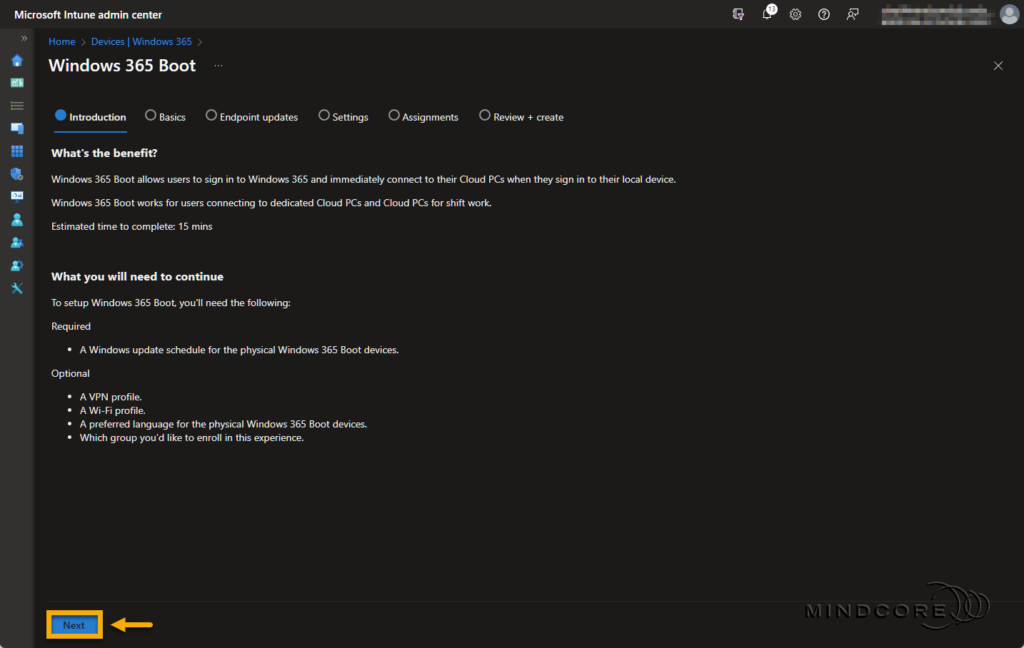
Fill in the required Device name and Resource prefix name field on the Basics page.
Click Next.
Tip: Although the Description field is optional, I recommend filling it out. Leaving some breadcrumbs is always a great idea, so others know precisely why someone created the configuration profile(s).
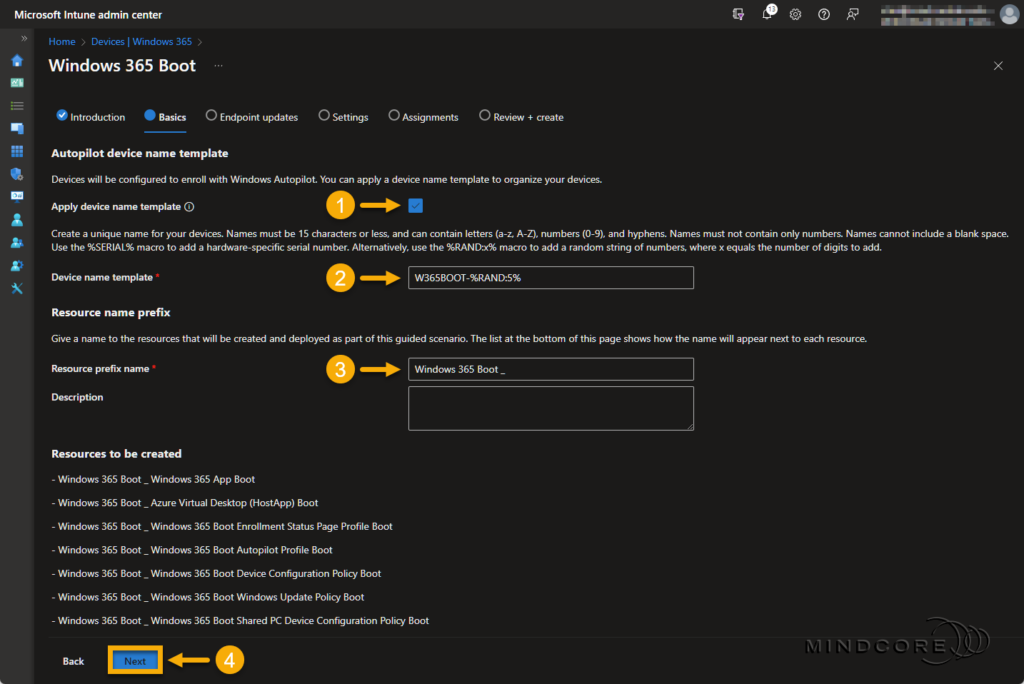
Keep the Windows update settings as is and click Next.
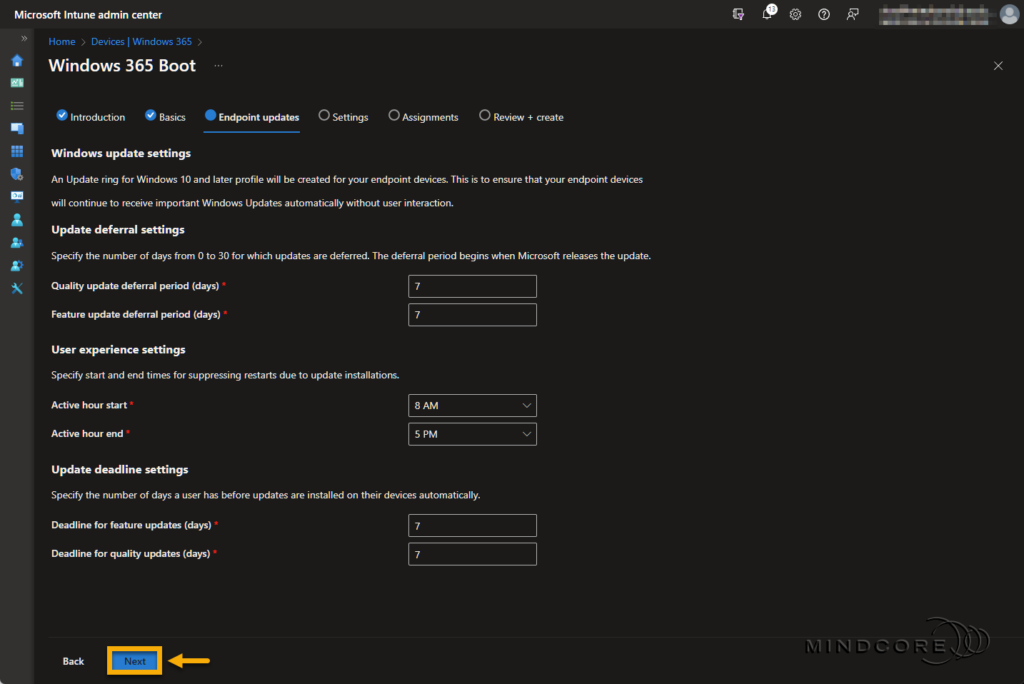
Select your preferred Language (Region) for the Windows Autopilot deployment profile.
Set the Max Connection Timeout to a value of your choice.
Click Next.
Note: Besides Language (Region) and Max Connection Timeout, you also have the option to select a VPN profile, a Wi-Fi profile, and a Security Baseline profile.
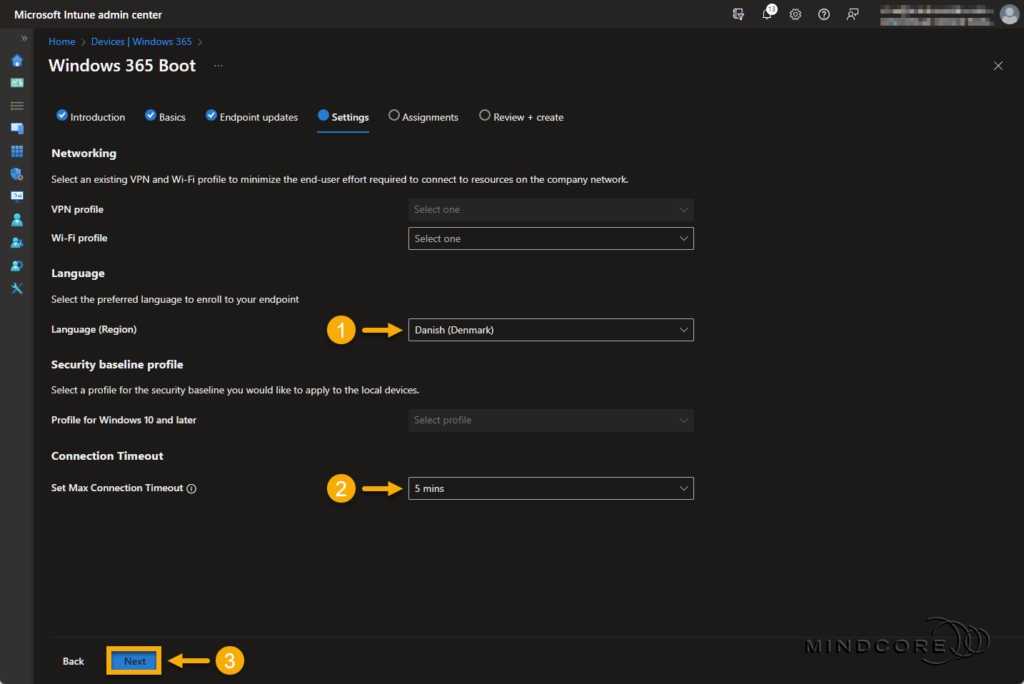
Next, we’ll assign my newly created Windows 365 Boot security group to these resources.
Click Next.
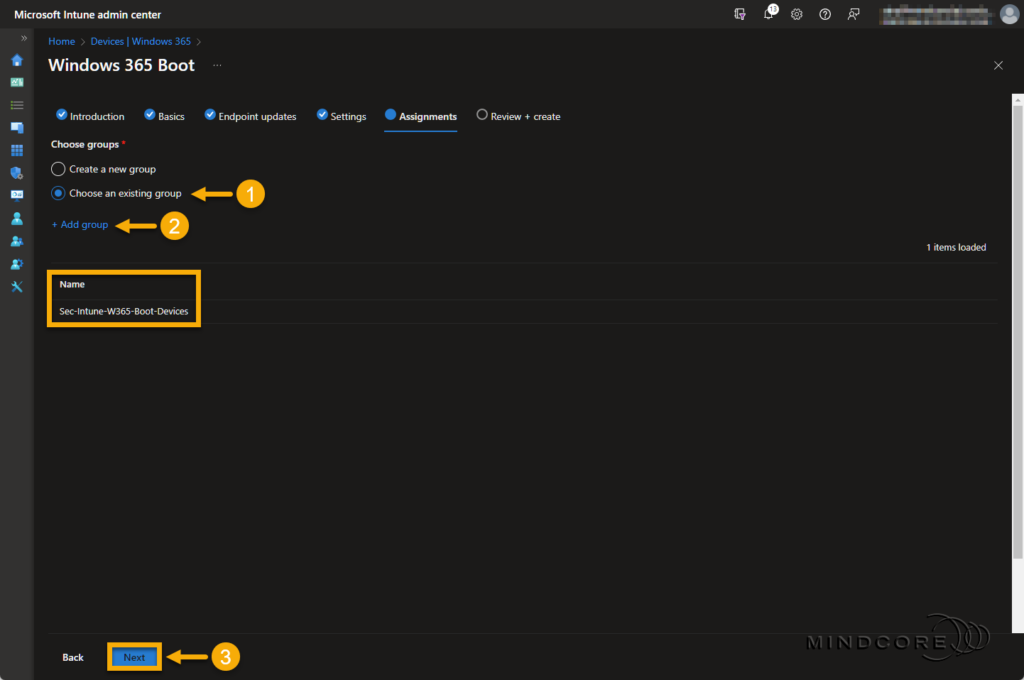
Review that everything is correct and click Save.
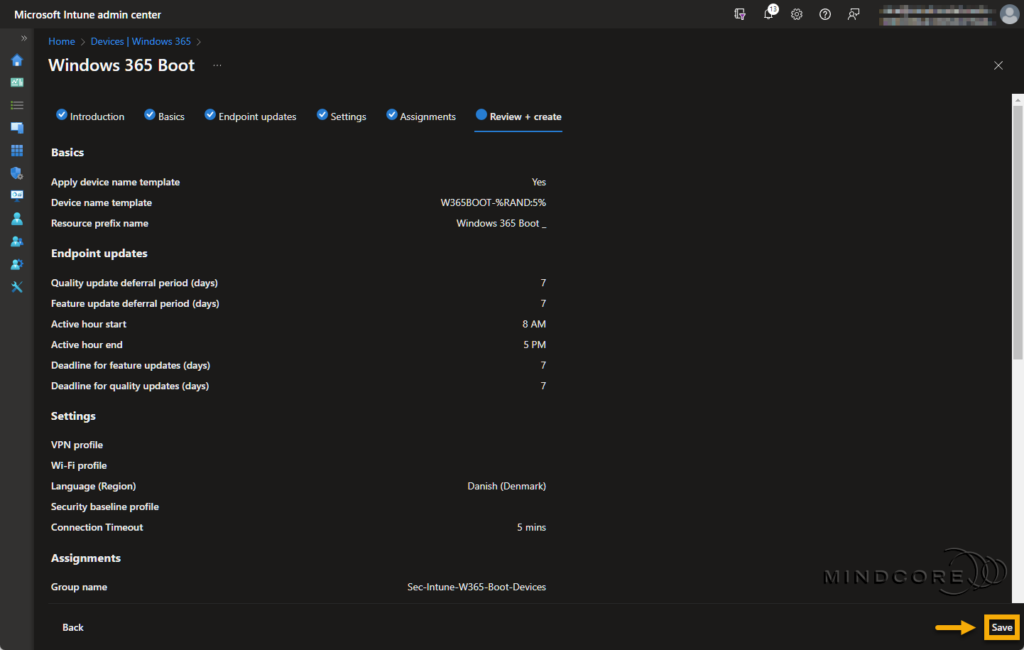
Once ready, we can move our attention to the preparation of the physical device.
The Windows 365 Boot Physical Device Setup
Let’s move on to preparing the physical devices, which requires adding them to our security group, a device wipe from Microsoft Intune, and Windows Autopilot registration.
Go to https://intune.microsoft.com
In the left pane, select Groups.
Select the newly created Windows 365 Boot security group.
Click + Add members, choose a device, and click Select.

Next, select Devices | Windows (under By platform), choose the device you added to the Windows 365 Boot security group, and select Wipe. – Don’t select any of the boxes in the wipe confirmation box!
Click Wipe.
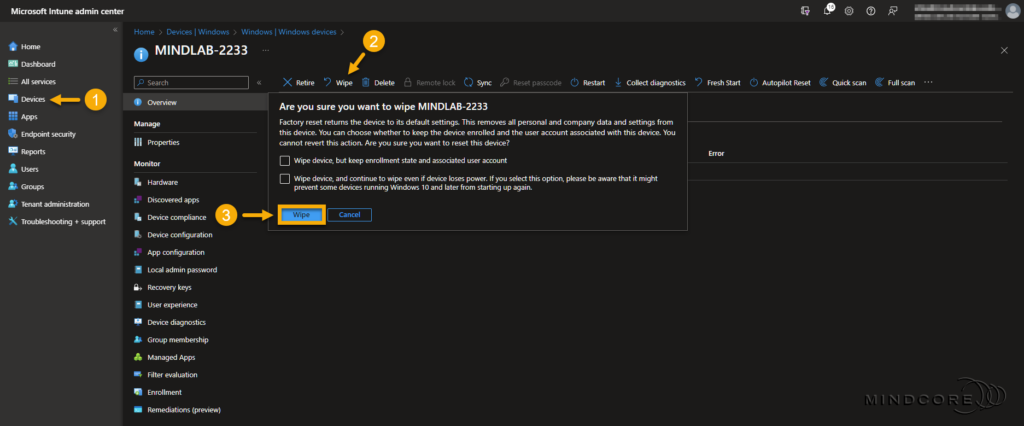
Note: Skip this section if the device is already registered with Windows Autopilot.
From the Out-of-Box-Experience (OOBE) stage, use Shift+F10 to open a command prompt.
Run the following commands:
PowerShell.exe
Set-ExecutionPolicy Bypass
Install-Script -Name Get-WindowsAutopilotInfo -Force
Get-WindowsAutopilotInfo.ps1 -Online
Restart-ComputerWhen prompted, sign in with a user that has the Intune Administrator role. After sign-in, the device is automatically enrolled in Microsoft Intune. – Wait a few minutes and then reboot the device.
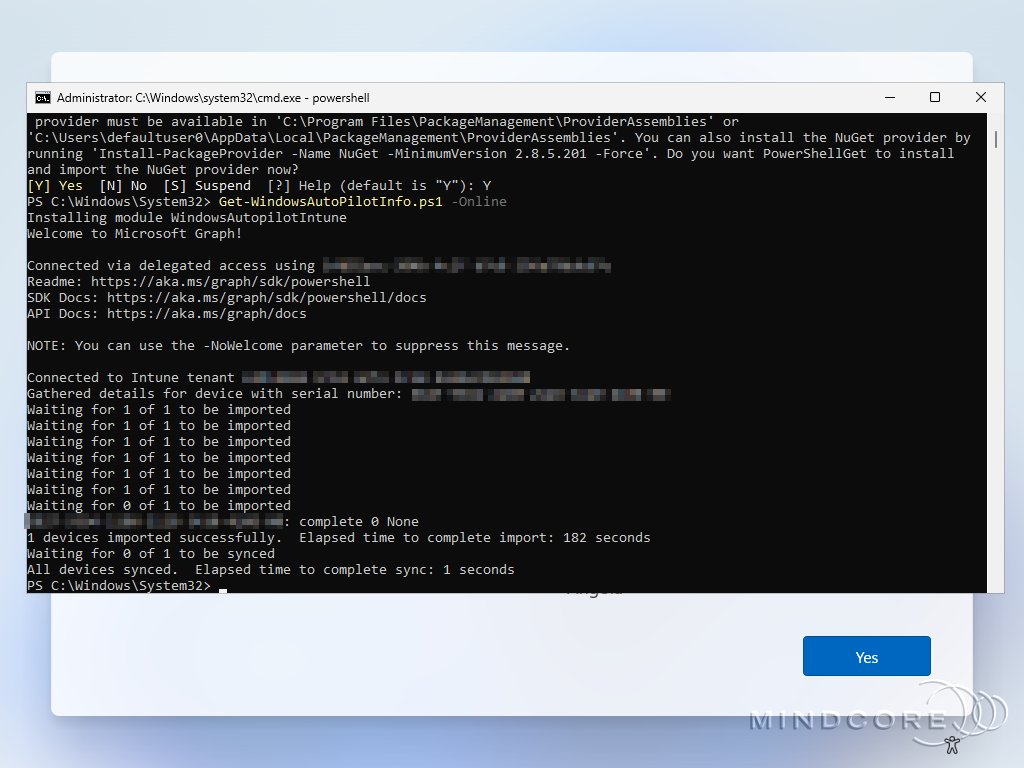
Now, complete the Out-of-Box-Experience (OOBE) as you would with any user.
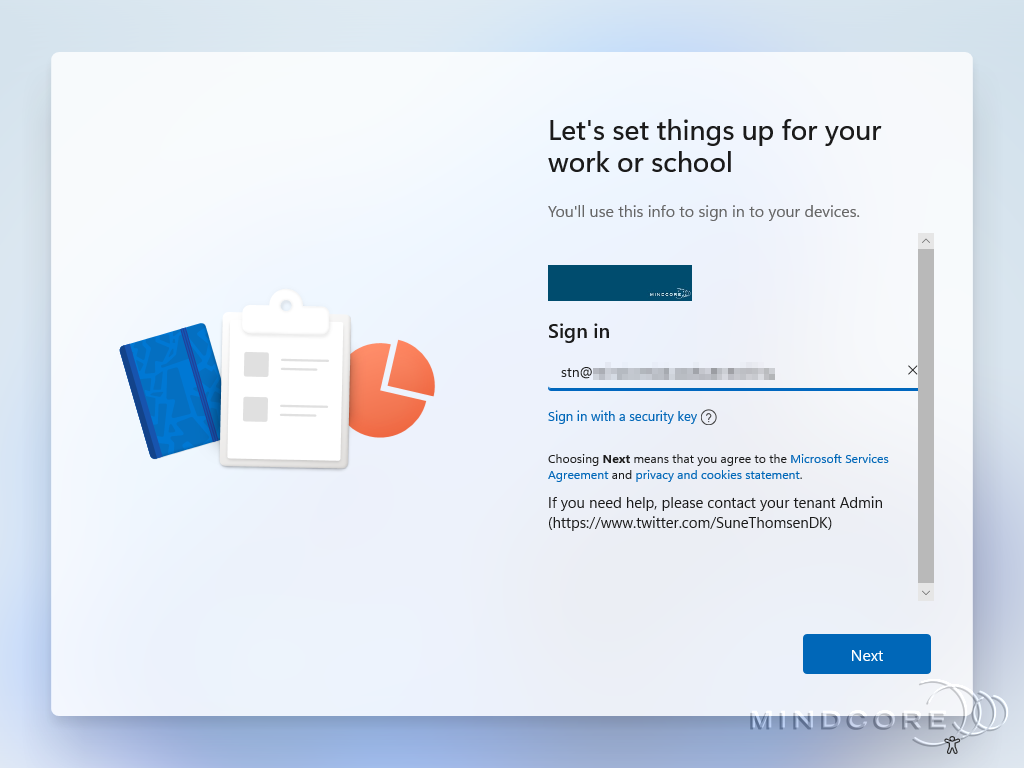
It runs through the Enrollment Status Page (ESP)
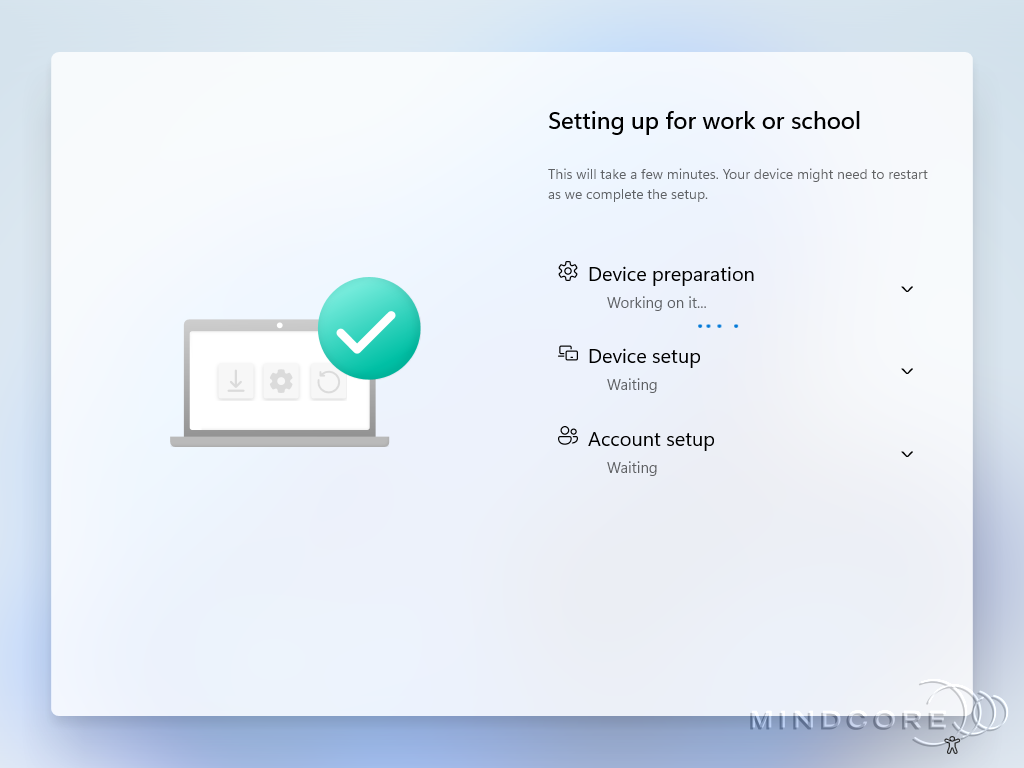
The Windows Autopilot provisioning is complete when you see the Windows 11 login screen.

Test and Verification
The user signs in with their Microsoft account on the Windows 11 login screen.

Once the credentials are validated, the user seamlessly connects to their Windows 365 Cloud PC.
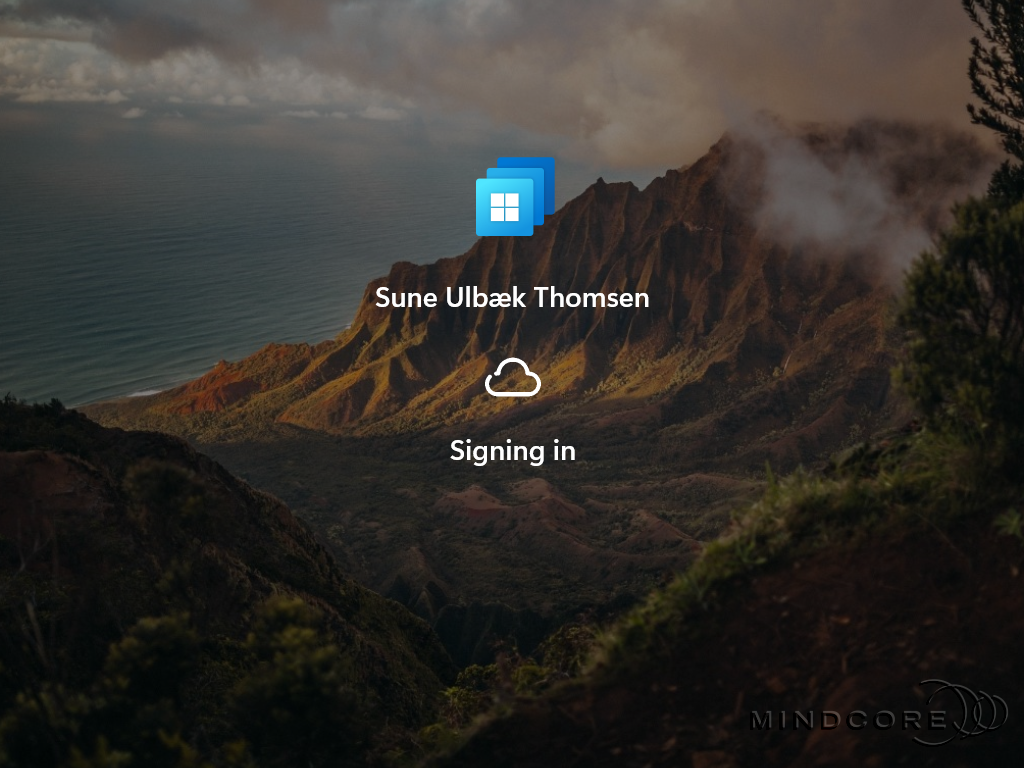
I’m often asked if signing in locally to the physical device is possible, and the answer is NO! However, users are not completely restricted in accessing specific resources on the physical device. – In the next section, I will show you how to restrict access to specific resources with a few additional policies from Microsoft Intune.
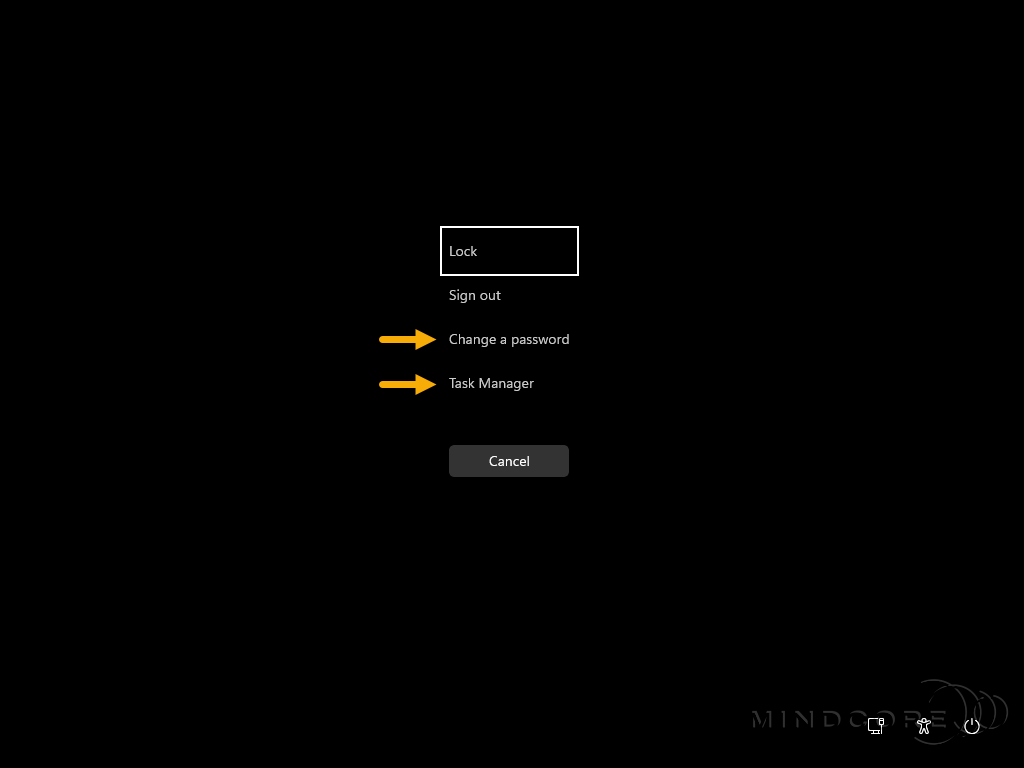
Restrict User Access
The purpose of Windows 365 Boot physical devices is to let users interact directly with their Windows 365 Cloud PCs without the ability to access specific resources on the physical device. – However, IT admins must configure a few additional policies to achieve this goal.
Note: Windows 365 Boot doesn’t fully restrict end users from accessing specific resources on the physical device. You should review the configuration policies you can apply to your Windows 365 Boot devices to meet your organization’s security needs for preventing access to the physical device.
For more information, see Restrict user access to Windows 365 Boot physical device.
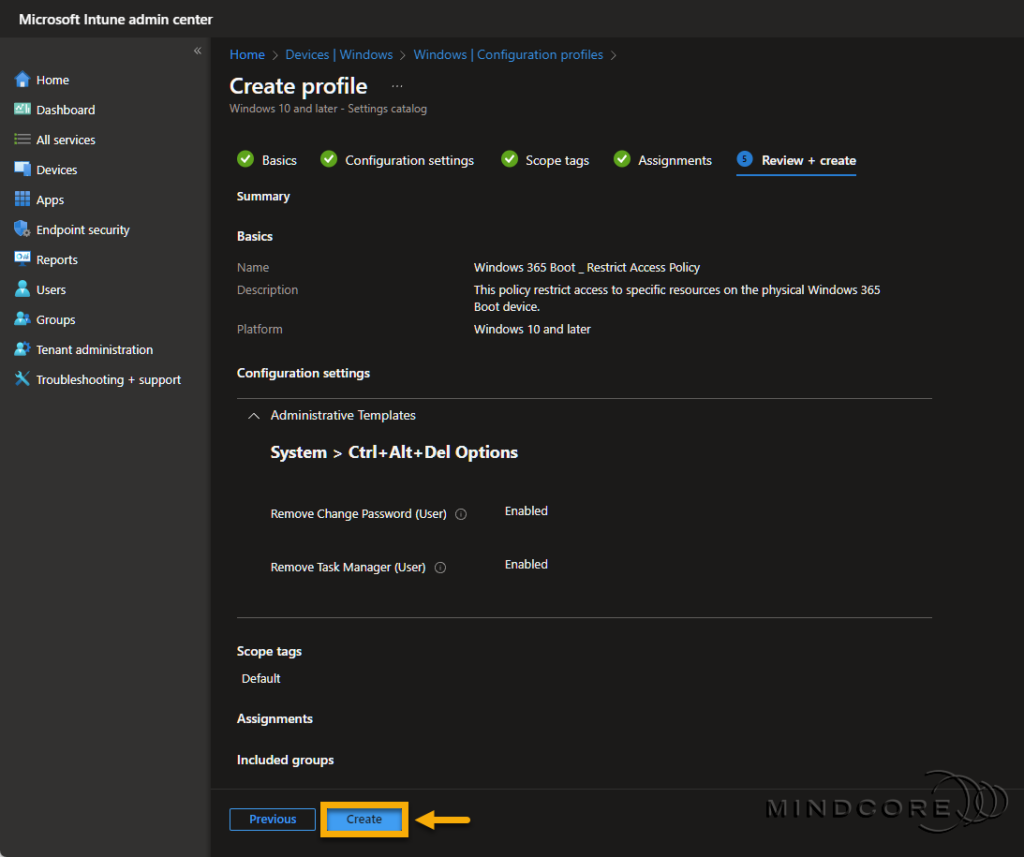
Let’s remove the ability to access the Task Manager and Change a password.
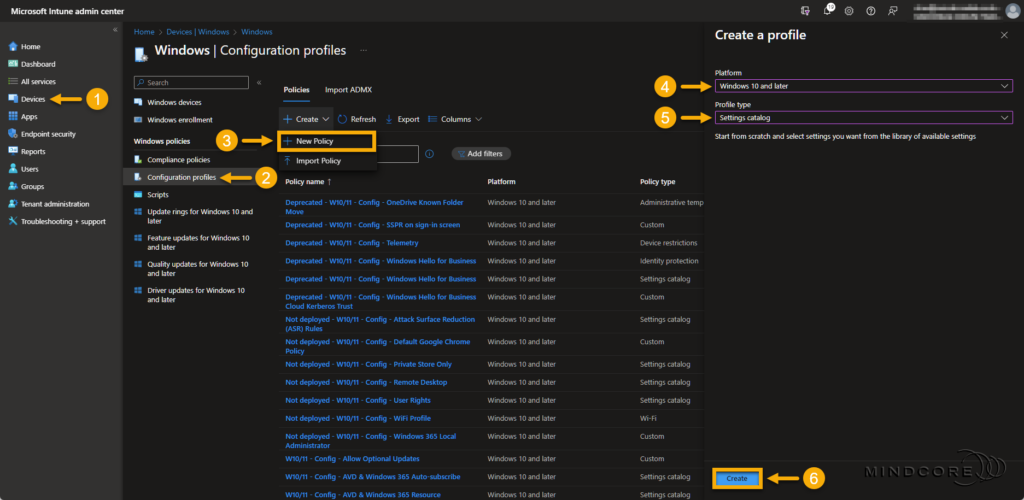
Go to https://intune.microsoft.com
Select Devices | Windows (under By platform) | Configuration profiles
Click + New Policy, choose Windows 10 and later, and the Settings catalog, and click Create.
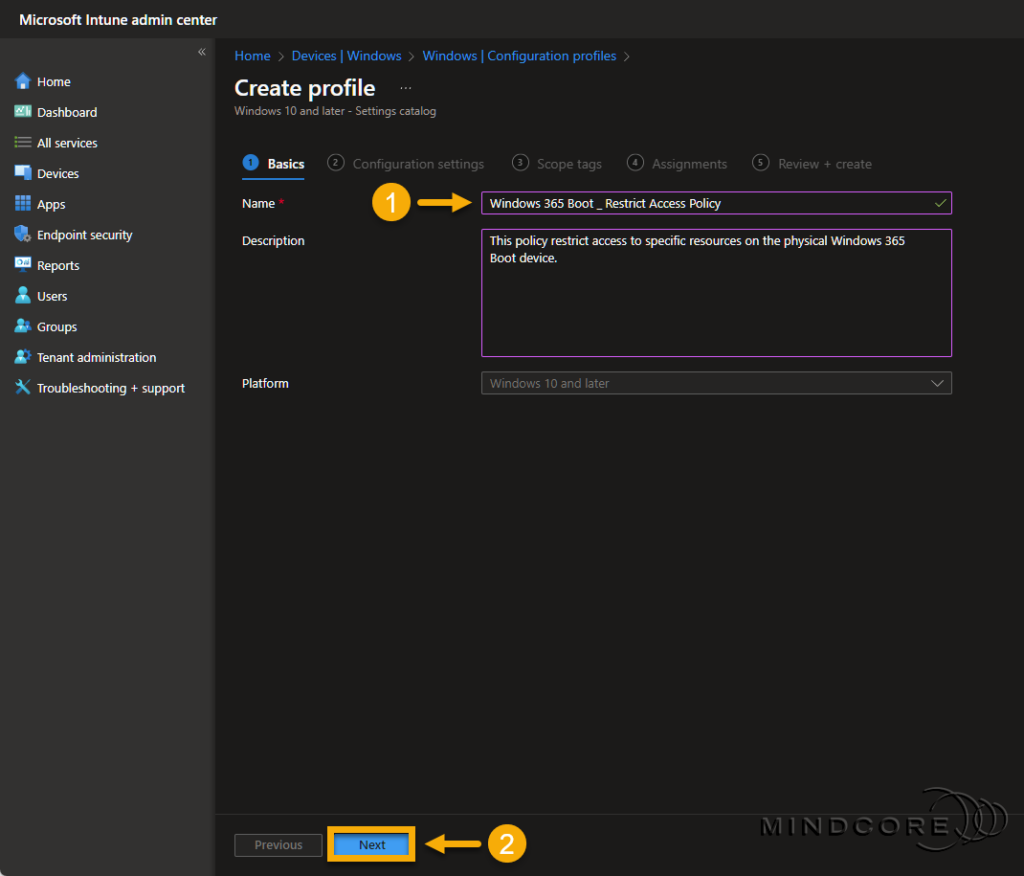
Fill in the required Name field on the Basics page.
Tip: Although the Description field is optional, I recommend filling it out. Leaving some breadcrumbs is always a great idea, so others know precisely why someone created the configuration profile(s).
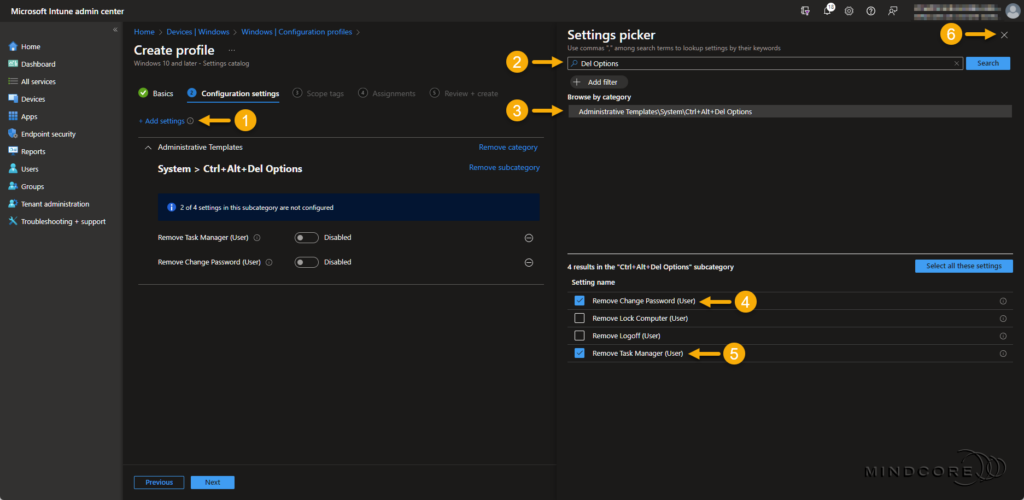
Click + Add settings on the Configuration settings page. In the Settings picker, search for Del Options.
Choose Administrative Templates\System\Ctrl+Alt+Del Options and select the following two settings:
- Remove Change Password (User)
- Remove Task Manager (User)
Close the Settings picker.
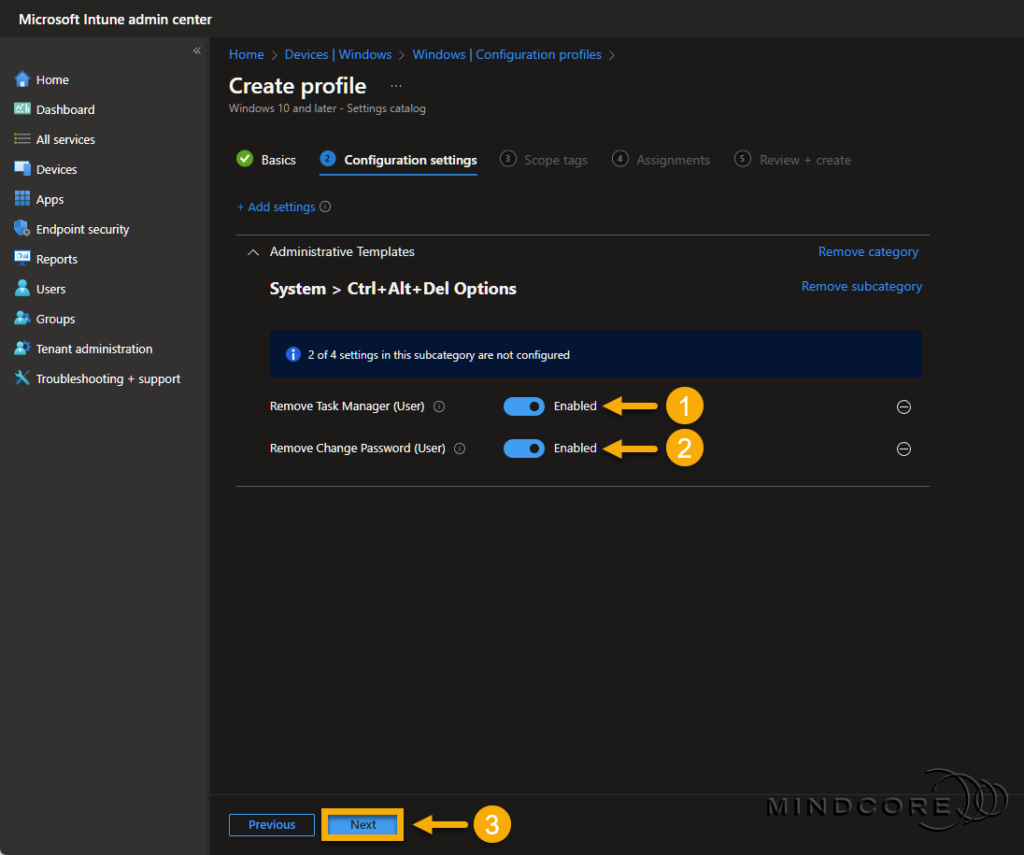
Enable both settings and click Next.
Select Scope tags if needed and click Next.
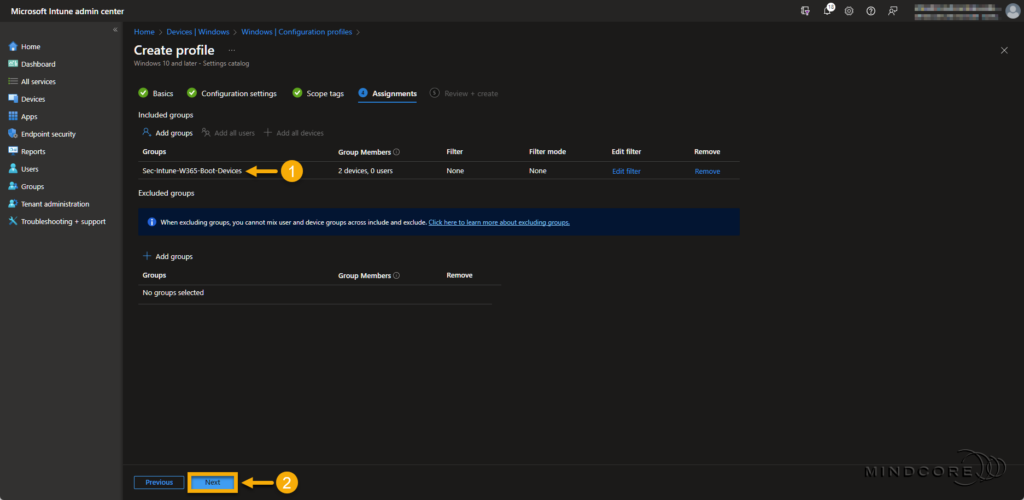
On the Assignments page, assign the Windows 365 Boot security group to this policy and click Next.
Review that everything is correct and click Create.
Verification
End users will no longer be able to access the Task Manager or Change a password on the physical device.

Summary
In this blog post, you learned about the concept of Windows 365 Boot and why it complements Windows 365 Frontline so well. I shared my view on use cases and took you through the guided scenario in Microsoft Intune.
In addition, you also learned that Windows 365 Boot doesn’t fully restrict end users from accessing specific resources on the physical device and what you can do to restrict access to those resources.
I hope you enjoyed this post and that you found it helpful. – To learn more about Windows 365, please visit our Windows 365 category.
That’s it, folks. Happy testing, and Merry Christmas!🎄🎅
If you have any questions regarding this topic, please feel free to reach out to us.
Sune Thomsen is based in Denmark, and he is a dedicated IT Consultant at Mindcore with over 19 years of experience in the IT industry. He has spent at least a decade specializing in client management via Microsoft Configuration Manager and Intune.
His key areas:
- Microsoft Intune (i.e., Autopilot, Windows 365, Endpoint Security, etc.)
- Client Management in general
- Application Management
- Cloud transitioning and building solutions toward the cloud
He's a Windows 365 and Windows MVP, an Official Contributor in a LinkedIn group with 41.500 members, and a Microsoft 365 Enterprise Administrator Expert.
Sune is passionate about community work and enjoys sharing his knowledge and experience and inspiring others via our blog. Besides blogging, he also writes newsletters on behalf of the Windows 365 community, does technical reviews for book publishers, and speaks at tech events.
Official Contributor here "Modern Endpoint Management":
https://www.linkedin.com/groups/8761296/














