Microsoft Sentinel is a powerful security information and event management (SIEM) system that provides real-time threat detection and response (you can read more about Sentinel in part 1 of this series). It allows security teams to collect, analyze, and act on security data from multiple sources, including Azure, Office 365, and third-party products (read more about data-ingesting in part 2 of this series). Microsoft Teams is a collaboration platform that allows teams to work together and share information.
In this blog post, we will discuss how Microsoft Sentinel can be integrated into Microsoft Teams using playbooks, enabling security teams to collaborate and respond to security incidents more effectively.
Below you’ll find all parts of this blog series.
- The Sentinel Awakens: Microsoft Sentinel Introduction
- Feeding the Beast: Data Ingestion with Microsoft Sentinel
- Sentinel Teams Up: Integrations with Microsoft Teams
What are Playbooks?
Playbooks are a feature of Microsoft Sentinel that allows security teams to automate and orchestrate incident response activities. They are a set of automated workflows that can be triggered by security events, allowing security teams to respond to incidents quickly and efficiently. Playbooks can be customized to meet the specific needs of an organization and can integrate with various systems, including Microsoft Teams.
Integrating Microsoft Sentinel into Teams using Playbooks
Sentinel can be integrated into Microsoft Teams using playbooks. This integration allows security teams to collaborate and respond to security incidents more effectively.
Prerequisites:
Before getting started ensure the following prerequisites have been met:
- A Microsoft Sentinel Workspace has been set up as described in earlier blog posts including the Azure Active Directory Identity Protection Data connector.
- An Azure AD P2 license to take advantage of Identity Protection in order to generate the alert required to trigger the playbook.
If these prerequisites have been met you can proceed with the below outlined steps:
- The first step is to import (or create from scratch but that is a blog post by itself) a playbook in Microsoft Sentinel that will be triggered by a security incident.
For this blog post, we’ll configure an integration into Teams that will post an adaptive card into a specified Teams channel based on incidents created by suspicious AAD Identities. Luckily, a playbook has already been created for us to use and can be easily imported directly from GitHub.
Scroll to the bottom of the linked GitHub page and press the ‘Deploy to Azure‘ button. - Once authenticated the following custom deployment can be further configured by assigning the appropriate subscription and resource group in which the Microsoft Sentinel Workspace resides in.
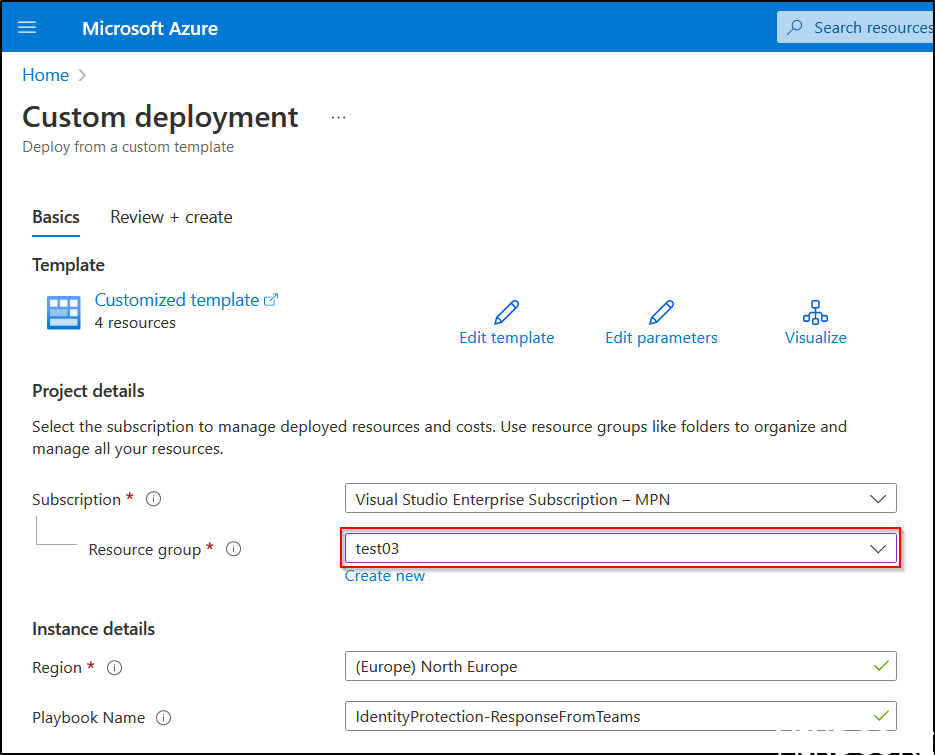
If ready to deploy hit ‘Review + create‘ and wait for the deployment to finish.
3. When successfully deployed, the playbook should now be listed within Sentinel under Configuration > Automation > Active Playbooks.

4. Some further configuration within the playbook is required in order for it to authenticate to Teams. Open the newly created playbook and click on the ‘Edit‘ tab. This opens the Logic Apps Designer. Next, expand Connections and Entities – Get Accounts and ‘Add new‘ to both by signing in a user with appropriate permissions (most notably Sentinel Contributor in order for the Teams card to be able to update the incident information). Also important to note is that the specific Teams channel can be specified within the ‘For each‘ loop. Be sure to save the Logic App before moving on!

5. Next, an Analytics rule needs to be created in order for incidents to be created and have the playbook be triggered. For this blog post we’ll use a rule template as a starting point. This can be done under Configuration > Analytics > Rule template where I’ve filtered for ‘Azure Directory Identity Protection Alerts’ and we’ll hit ‘Create Rule‘.

The rule requires further configuration where on the ‘General‘ page nothing requires changes (apart from the name if desired.

Next, under the ‘Automated response‘ tab we’ll create a new automation rule that will trigger the previously created playbook to run when an incident is created:

Finally, save the rule and ensure it is listed as an enabled rule under Configuration > Analytics > Active rules.

6. For the last step its time to test the rule. For this rule to trigger we need to generate an AAD Identity Protection alert which can be done by attempting to sign-in from a unknown location – assuming that an appropriate sign-in risk policy is configured within Identity Protection. Details on how to simulate risk detections can be found on Microsoft’s website.
If successful the alert should trigger within about 10-15 minutes and a Teams card should be posted to the specified Teams channel as shown below:

Now a security analyst can choose to update the Sentinel incident information immediately from within Teams using the provided options.
Benefits of Integrating Microsoft Sentinel into Teams
- Faster incident response: Integrating Microsoft Sentinel into Teams enables security teams to respond to security incidents more quickly and efficiently.
- Collaboration: Teams allows security teams to collaborate and share information, enabling faster and more effective incident response.
- Customization: Can be customized to meet the specific needs of an organization, providing a tailored incident response process.
- Automation: Automate incident response tasks, reducing the time and effort required to respond to security incidents.
Conclusion
Integrating Microsoft Sentinel into Teams is a powerful way to enhance incident response capabilities. It enables security teams to collaborate and respond to security incidents more effectively, reducing the time and effort required to do so. Customizable playbooks allow organizations to tailor their incident response process to their specific needs, ensuring that incident response tasks are performed quickly and accurately. Organizations looking to enhance their incident response capabilities should consider some level of integration of Microsoft Sentinel into Teams.
Security consultant with focus on cloud and Azure.













