Mandatory MFA enforcements is coming
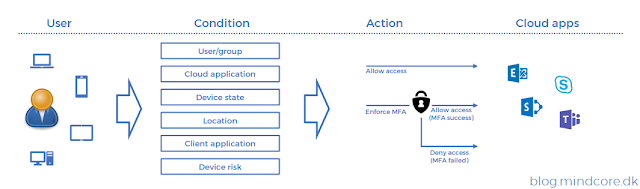
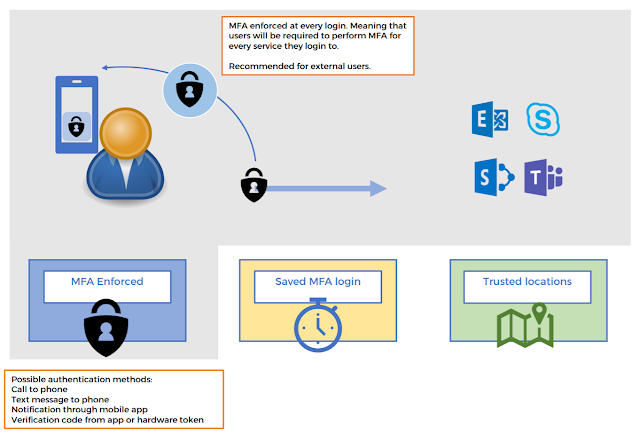
Introduction In case you missed the update about the new announcement Microsoft is tightening security around Azure and Microsoft admin portals, by enforcing multifactor authentication (MFA) for all interactive sign-ins. This change has sparked a lot of questions across social medias, and in this post, I aim to address these