Introduction
I do see a lot of environments transitioning from On-prem towards the cloud. One of the tasks in this journey is Group Policies which normally will have a huge workload on the business when starting to analyze and transforming the needed policies. Not saying that you should move anything, but you don’t know before you have gone through the stack of policies applied to the current environment. Better be prepared than sorry.
What is this blog post about? When you have a hybrid setup, which most larger customers do have at the moment, you will see a period of time where you transition from GPO’s to cloud policies where you have policies coming from 2 authorities. If a certain policy is not behaving, as you think it should, it can be hard to know where to look.
I’ll walk you through how to debug with a tool made by Andrew
Requirements
- Intune managed device (either co-managed or Intune only)
- Permission to add an app registration
Create app registration to fetch data from Intune
Before we do anything, we need to register an application in Azure, so the user running the Intune diagnostic tool, does not need to have permission to Intune or any other Azure related sources.
Go to https://portal.azure.com/#home -> Azure Active Directory -> App registrations

Give it a name like: Get-ClientIntunePolicyResult or whatever you like to call it. Doesn’t really matter, just that you will be able to identify what the app registration does later on.
Press Register

Write down the client ID and save it for later.

Press Certificates & secrets

Press new client secret

You can set it to never expire but I think it is good to have some kind of governance around this to not forget what you have given access to. If it is still in use after 24 month you will have to revisit the client secret and renew it.
Press add

Write down the value as we will need that for later.

Go to API permissions and press “Add a permission”

Press Microsoft Graph

Press Application permissions

Add
DeviceManagementApps.Read.All
DeviceManagementConfiguration.Read.All
DeviceManagementManagedDevices.Read.All
User.Read.all

Grad admin consent for xxxxxxx

Press Yes

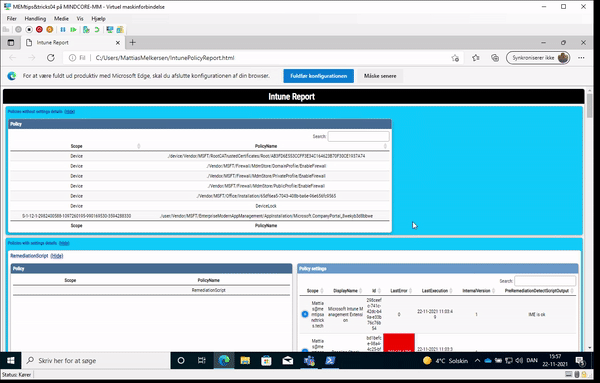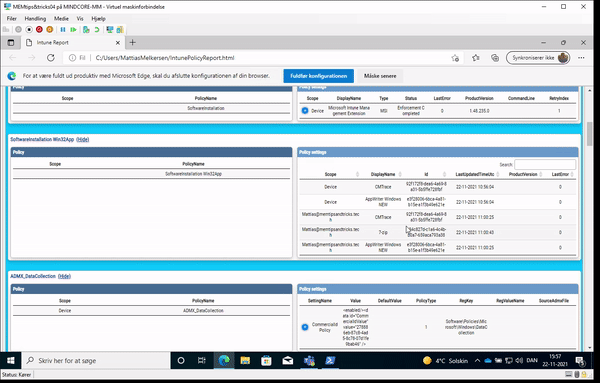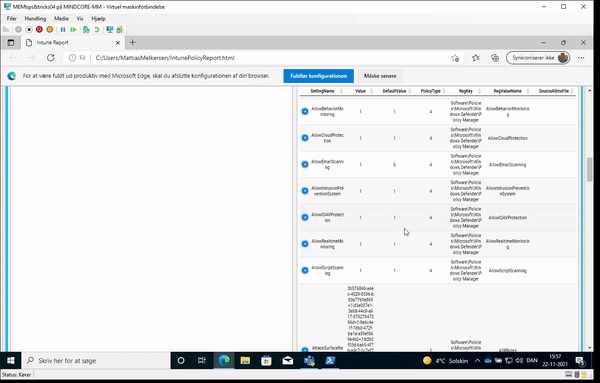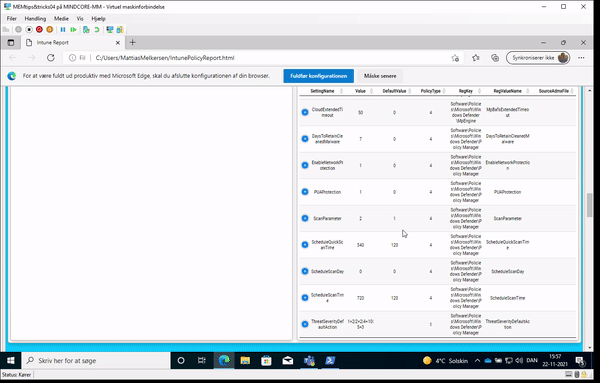
RSOP for Intune managed devices
Finally, to the interesting part of the blog
Go to a client where you like to debug.
Open PowerShell with admin credentials

Install-module PSWriteHtml -force
install-module Microsoft.Graph.Intune -force
install-module WindowsAutopilotIntune -force
install-script get-clientintunepolicyresult -force

And to the part where we will use the module to get our report of what policy target our device/user and who the winning provider is:
Get-ClientIntunePolicyResult -asHTML -getDataFromIntune -credential $intuneREADAppCred -tenantID xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxx -showEnrollmentIDs

Enter the AppID and the AppSecret that we saved earlier in this guide.
Press OK

Watch the magic happen.

What do we see here?





MDM policy wins over GPO
Now that we see the “WinningProvider” very clear we can help our environment to MDM policy that is set and has an equivalent GP policy will result in the GP service blocking the setting of the policy by GP MMC. This is how it is done.
Go to https://endpoint.microsoft.com/ and navigate to Devices -> Windows -> Configuration profiles
Create Profile





Assign it to all devices

Finalize the profile creation default values.
Summary
Using this tool will make your debugging options even more visual.
Could I have used the build-in diagnostic report?

Sure, you could, but does it provide the same amount of visibility?

versus

You be the judge of that.
Happy debugging!
See more information on the topic from Andrew
Convert Intune MDMDiagReport.html to PowerShell object (doitpsway.com)
Get a better Intune policy report part 2. (doitpsway.com)
Get a better Intune policy report part 3. (doitpsway.com)
Mattias Melkersen is a community driven and passionate modern workplace consultant with 20 years’ experience in automating software, driving adoption and technology change within the Enterprise. He lives in Denmark and works at Mindcore.
He is an Enterprise Mobility Intune MVP, Official Contributor in a LinkedIn group with 41.000 members and Microsoft 365 Enterprise Administrator Expert.
Mattias blogs, gives interview and creates a YouTube content on the channel "MSEndpointMgr" where he creates helpful content in the MEM area and interview MVP’s who showcase certain technology or topic.
Official Contributor here "Modern Endpoint Management":
https://www.linkedin.com/groups/8761296/














