Hi there. You might have heard of Microsoft Defender for Endpoints (MDE). It is a service that detects and responds on risk that has been discovered worldwide. I can wholeheartedly say the system works amazing and I am blown away of its reach and way to detect and respond immediately.
In this blog post I will cover a scenario of targeting servers and clients that are NOT enrolled in MDM with policies from Microsoft Intune. Why is that cool? For starters, servers are not supported to enroll into Intune, so if Intune is your only available management system, you now have a way to target security policies towards your servers without needing GPO, Configuration Manager, or other management tools.
In this blogpost I have setup an AD connector to sync my on-premises servers to the cloud for the server-objects to become hybrid Azure AD joined.
Before we dive into the post, we need to cover the necessary knowledge to get started using this cool feature!
INFO:
During this post I will refer to Microsoft Defender for Endpoint by using abbreviation MDE
Prerequisites
Active directory, Connectivity, and platform
Licensing and subscriptions
Device
- OS – Windows Server 2022 Datacenter
Azure AD group with a device assigned
- In this post I have added the server we will onboard later in the post, to MDE in a group called MEM-MDE-Wave0
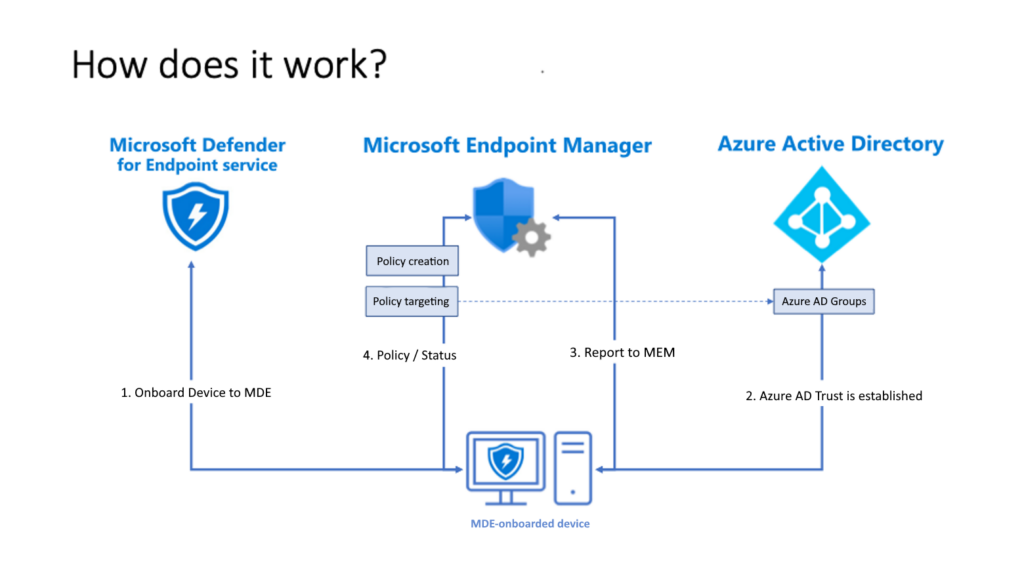
Setup connection between Intune and Microsoft Defender for Endpoint.
Go to endpoint.microsoft.com and click on tenant administration
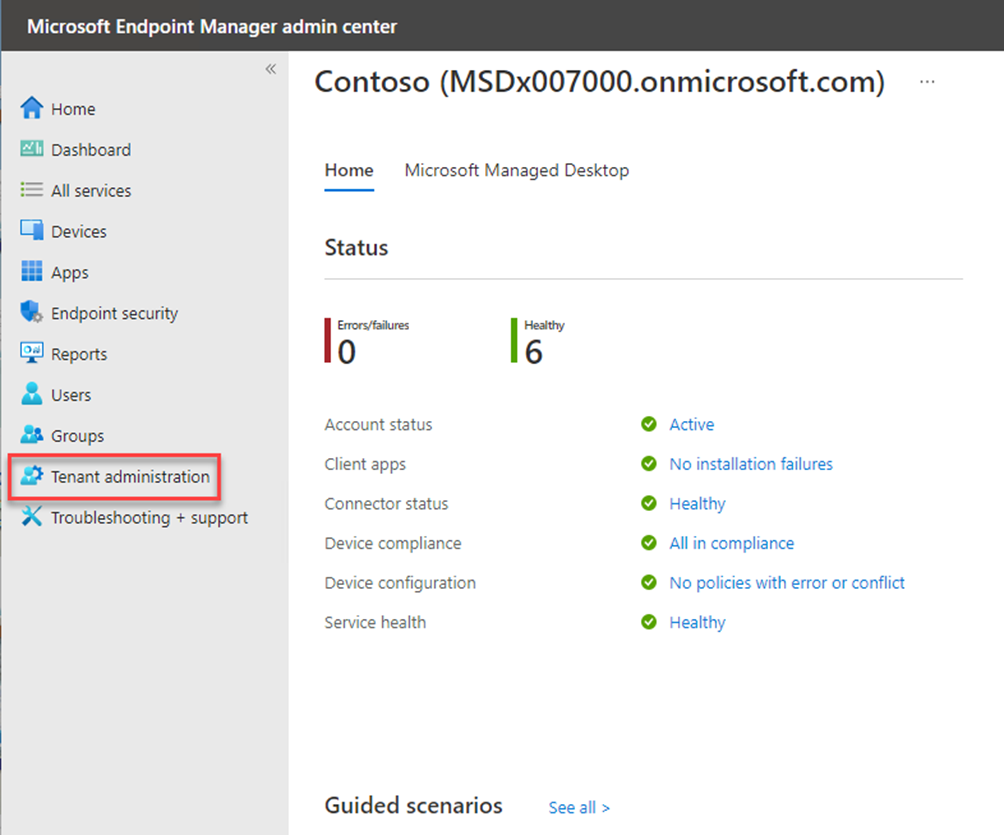
Click connectors and tokens
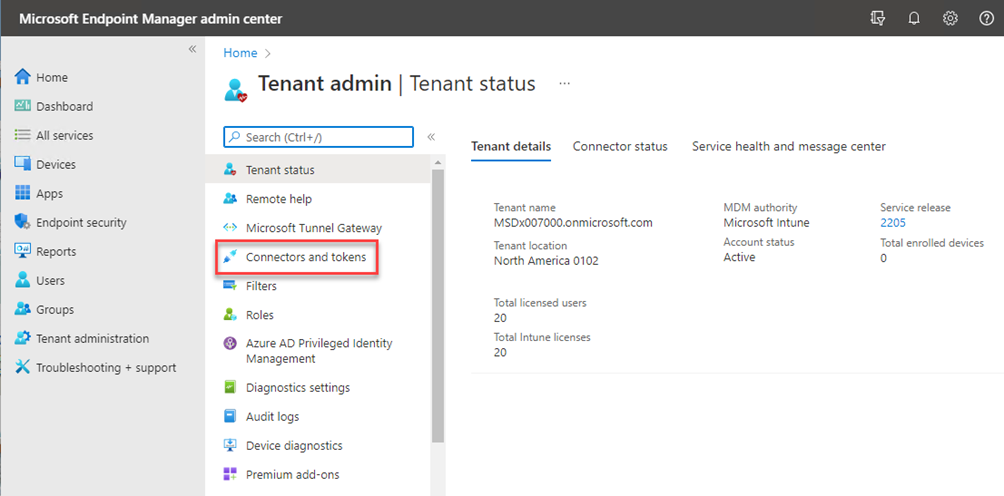
Click on the Microsoft Defender for Endpoint
TIP:
It is not needed to connect MDE with Intune to assign policies through the MDE channel, but in case you will onboard your MDM managed device to MDE, you can connect it when you are setting up MDE anyway. (You will see the toggle further down in this post)
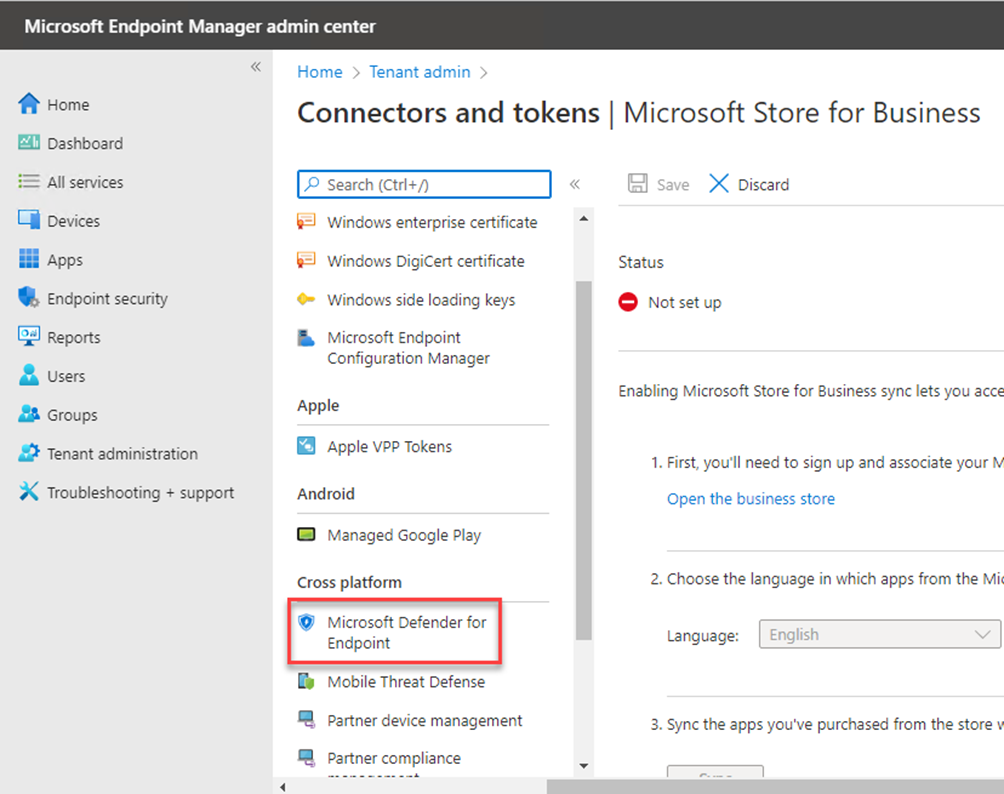
Click on the blue link that will send us to a new admin portal.
This is the first time we enter the Microsoft 365 Defender portal and therefore it must prepare the new space before we will be able to configure anything.
INFO
Give it 10 minutes to configure before going into settings.
Click on Settings
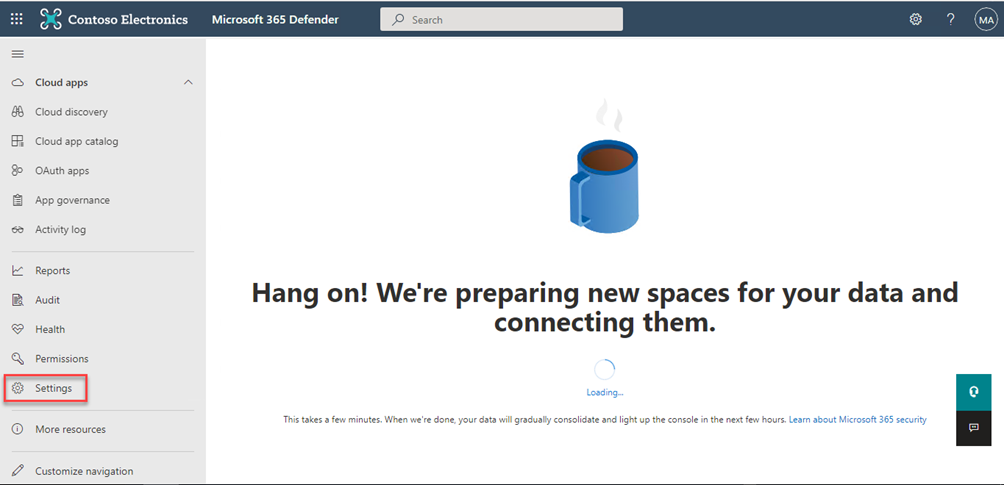
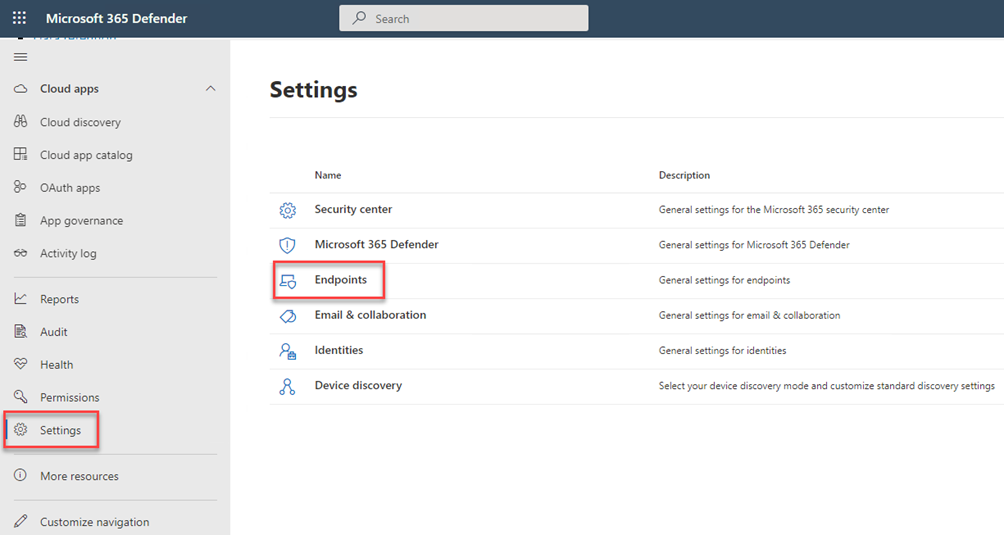
Click Endpoints
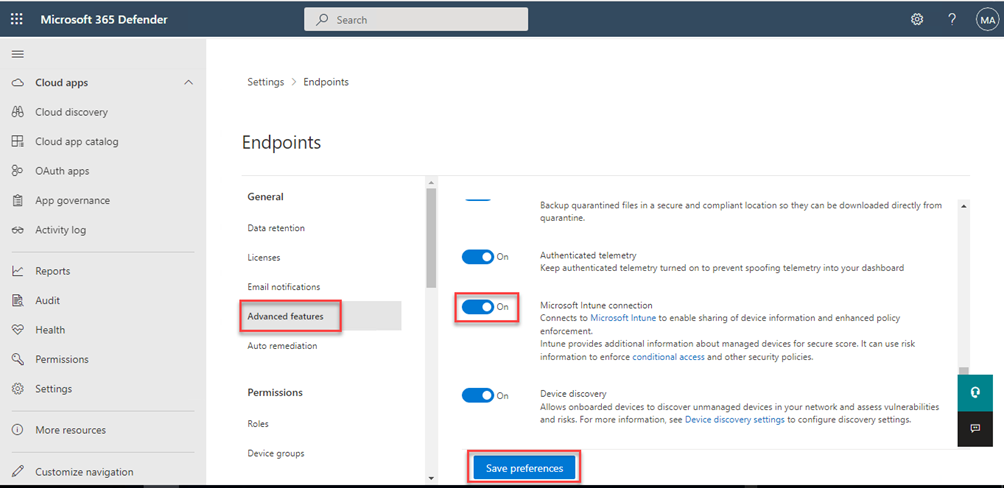
Under the Endpoints menu you will locate Advanced features and tick the radio button Microsoft Intune Connection and Save preferences.
INFO:
This setting is not related to the goal we want to achieve by managing devices that is not enrolled to MDM, but rather to connect Intune with MDE.
Scroll further down to Enforcement scope and tick the radio button Use MDE to enforce security configuration settings from MEM.
Tick the OS platforms you need to be able to manage with security policies.
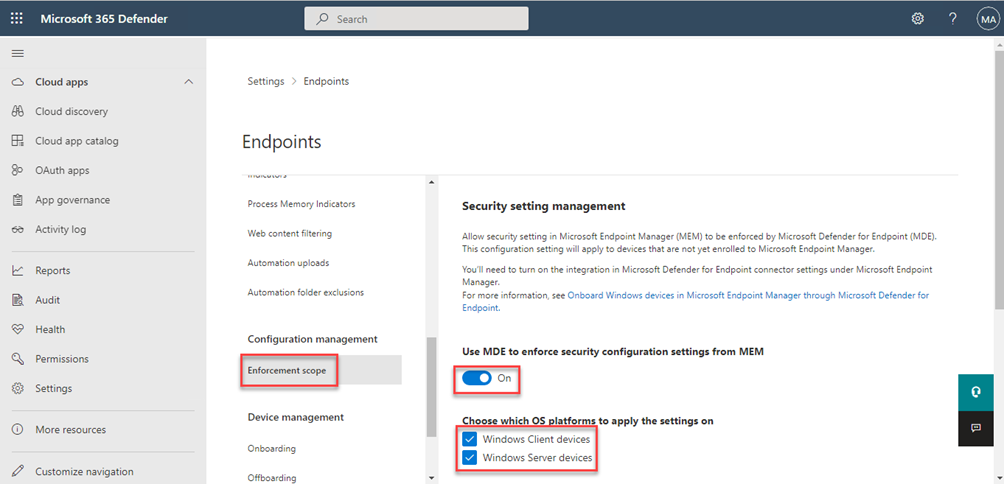
TIP:
If you are doing this in production and do not want all your unmanaged servers or clients to be seen in the Intune portal (admin center), you can start off by setting the Pilot Mode. If you use Pilot Mode, you should NOT tick Windows Client devices nor Windows Server devices as it would react on any condition. That will make sure only devices “tagged” with “MDE-Management” will enroll/added to your Intune portal (admin center). (Admins could be scared or surprised by having servers in the Intune portal all of a sudden 😉)
A view from the Azure portal we can see how your devices will be “added” or “enrolled” to the Intune portal, however a server cannot “enroll” it is just a matter of the server showing up in the portal. See below picture.
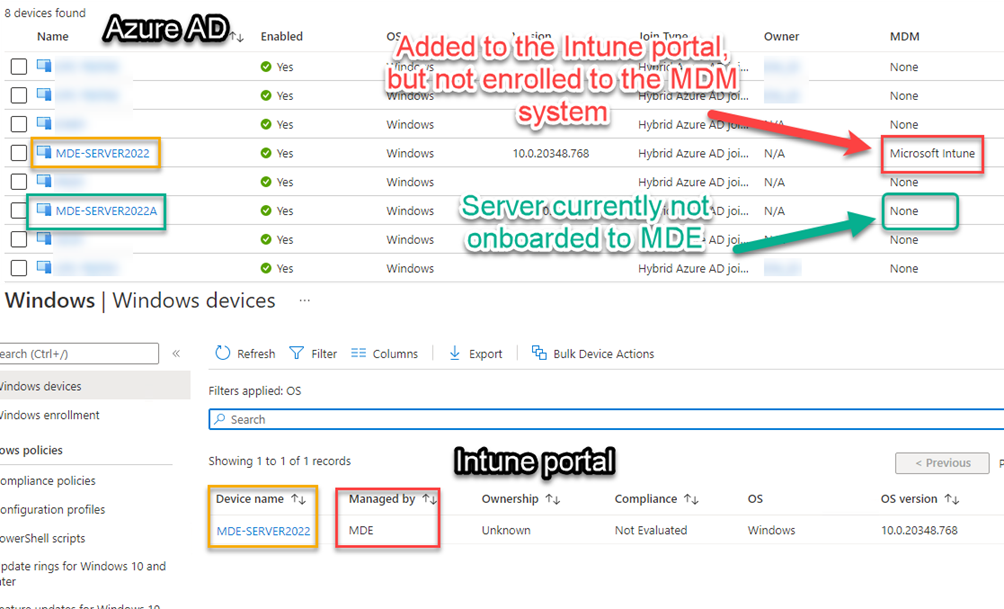
If we go back to the MDE portal, It is worth mentioning that if you have Configuration Manager client installed on your server or client OS, you need to choose which channel you will use to push these setting through. By channel I refer to through Configuration Manager or through the MDE Channel.
Click Save
INFO:
If the radio button Manage Security settings using Configuration Manager is ticked then
Configuration Manager is recognized as the single security management authority.
MDE will not manage security settings on machines that are already managed by Configuration manager.
If the setting is set to Off (as in the picture below), MDE will manage security settings on devices even if Configuration Manager is in place.
Microsoft docs recommends that for devices managed by Configuration Manager that you use that channel to distribute security settings. However, you can allow MDE to enforce security configurations on these endpoints if desired by configuring this toggle
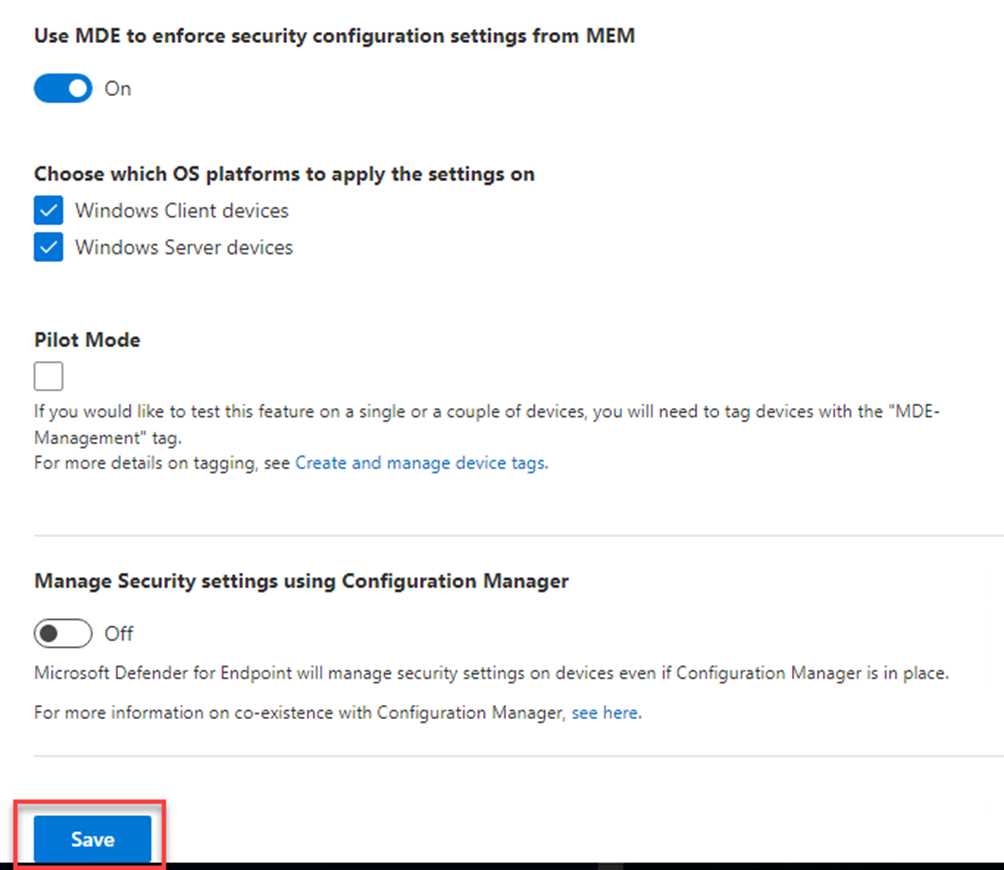
Congratulation you have configured everything we need in MDE!
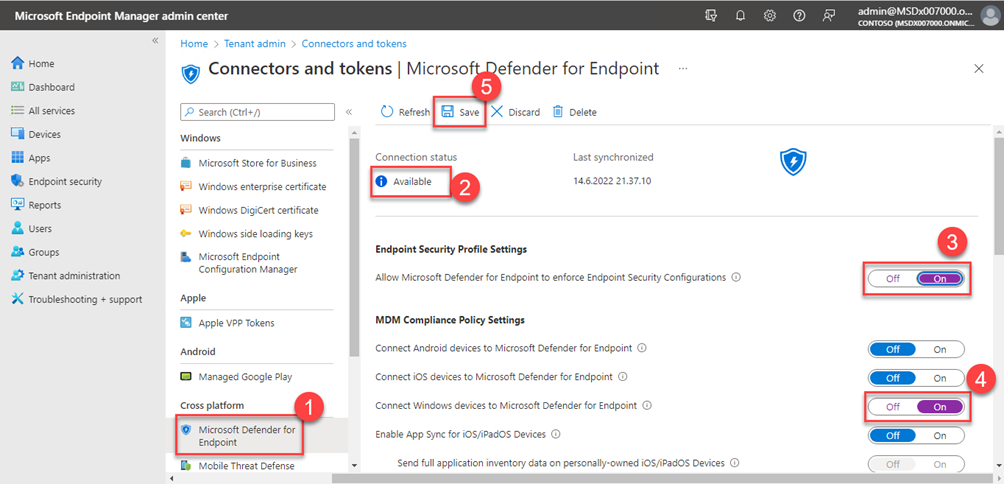
Let us shift back to the Intune portal where we left it in the MDE connector page.
- Microsoft Defender for Endpoint
- Connection status: Available
- Endpoint Security Profile Settings: ON (This is what allows MDE to enforce policies without MDM enrollment)
- Connect Windows devices to Microsoft Defender for Endpoint: ON (This will allow us to onboard MDM managed devices to MDE )
- Save
Onboard device to MDE and verify it works
There are several ways to onboard devices to MDE. In this blog post we will use the manual way, but you could as well use one of following ways to do this:
- Azure Defender
- Azure ARC
- Configuration Manager
- Intune (not unmanaged devices which we have in this blog post)
- Group Policy
- Local Script (what we use in this blog)
- VDI onboarding
- Unified down-level client
Let us get back to the Microsoft 365 Defender portal https://security.microsoft.com/preferences2/onboarding
Select Windows Server 1803, 2019 and 2022 and deployment method Local Script (for up to 10 devices)
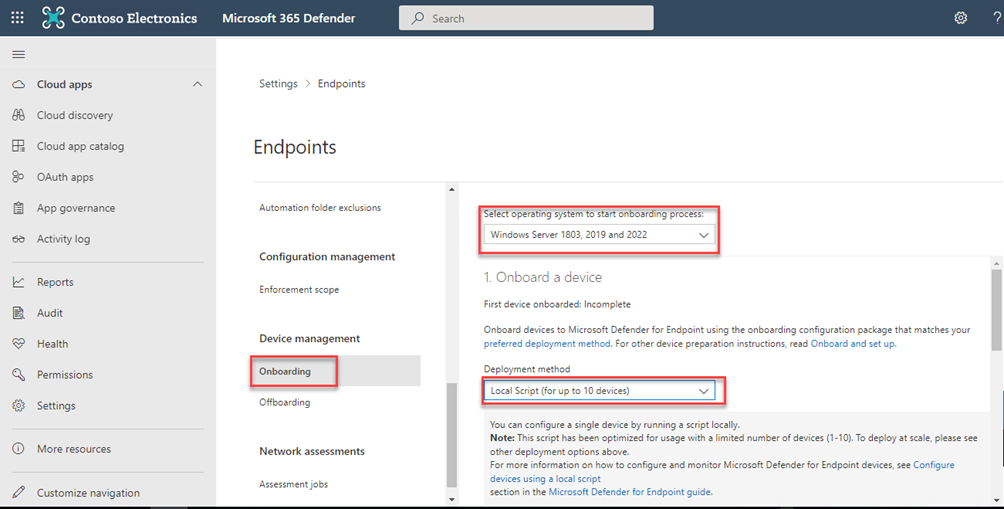
Press Download onboarding package
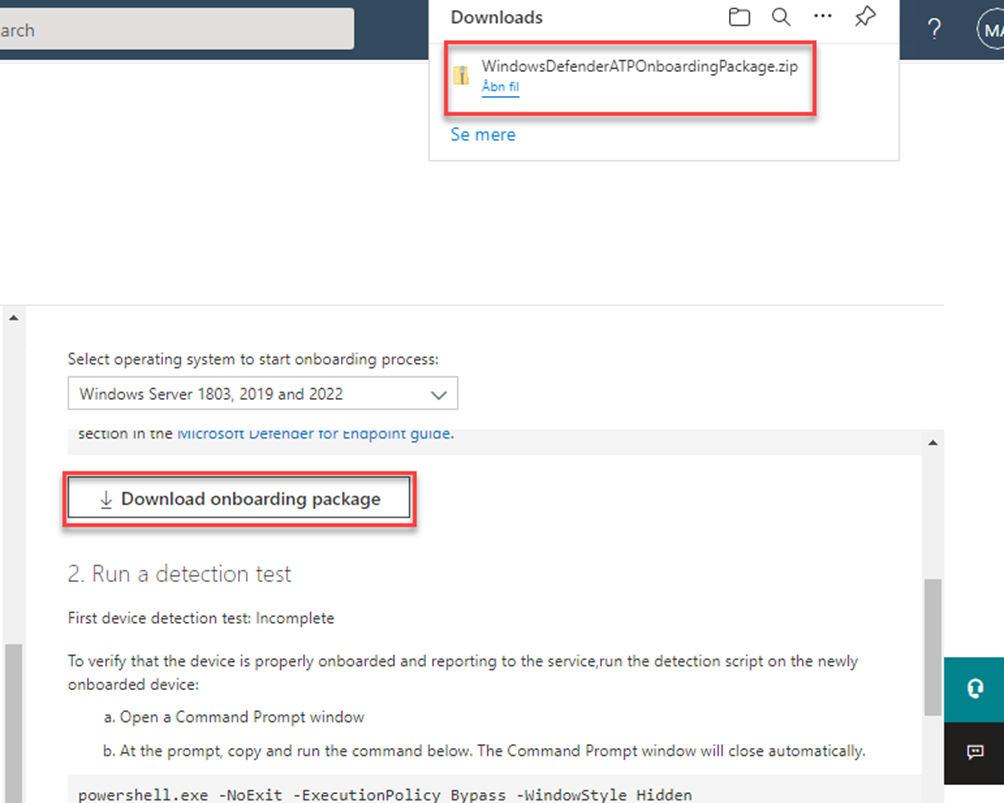
Unpack the zip file and copy the content to the device we will onboard
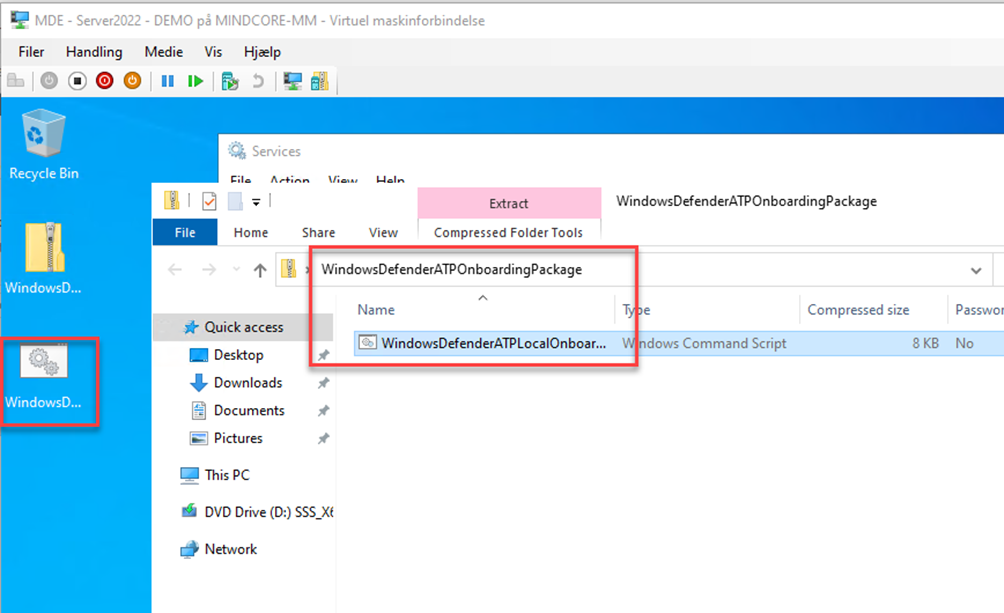
Right click the script and Run as administrator
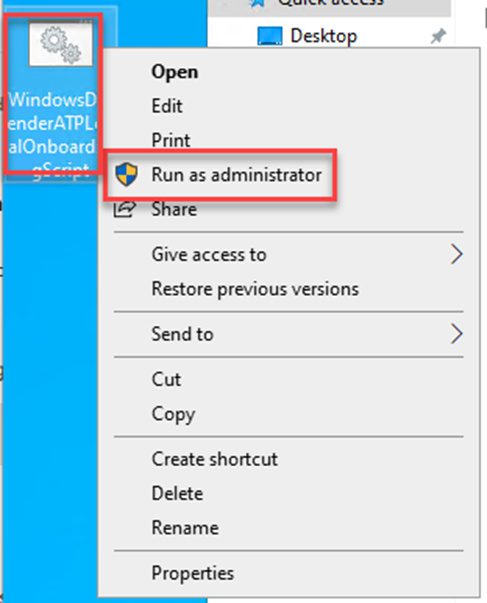
Press Y to confirm and continue
Once the command prompt says it is successfully onboarded, you can quit it.
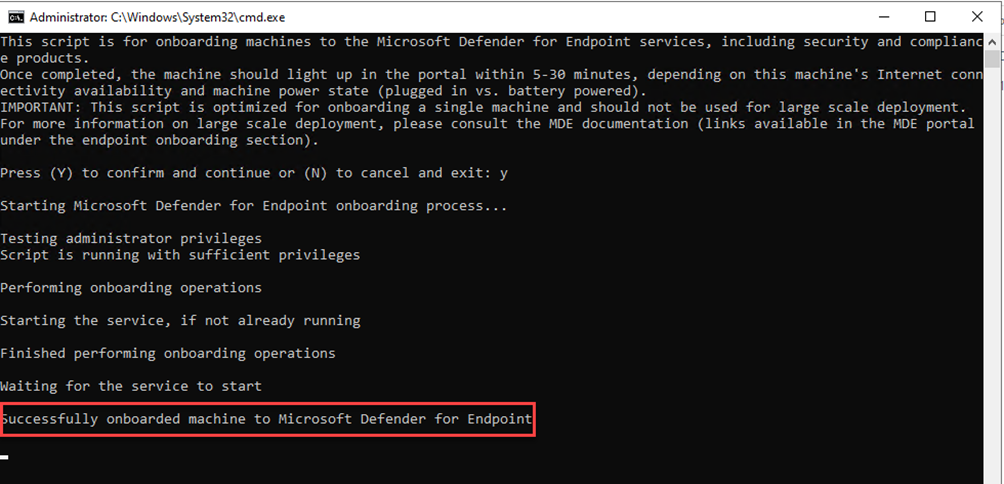
TIP:
Verify the needed services are running by typing these commands in a command prompt:
SC.EXE query windefend
SC.EXE query sense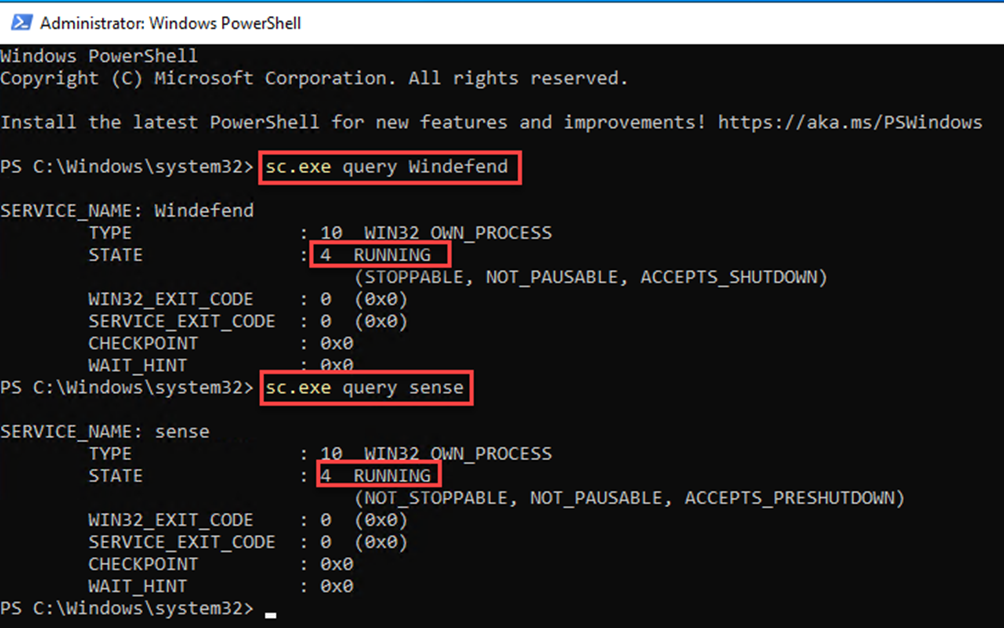
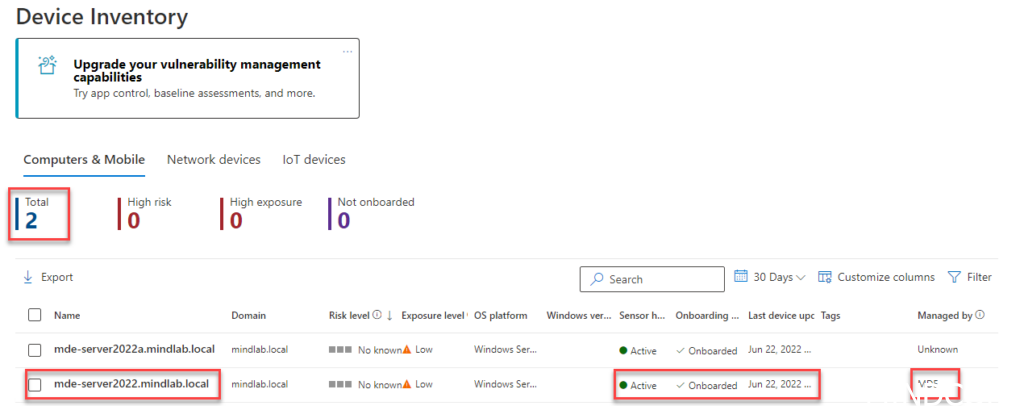
5-30 minutes after the onboarding script took place, you will be able to see your device in the MDE portal
https://security.microsoft.com/machines?category=endpoints
As we can see in my picture the device was onboarded, and the sensor is active on the device and it says managed by MDE.
As a test if our device was onboarded correct, we will run a script that will trigger an alert
Go to Settings and Endpoints
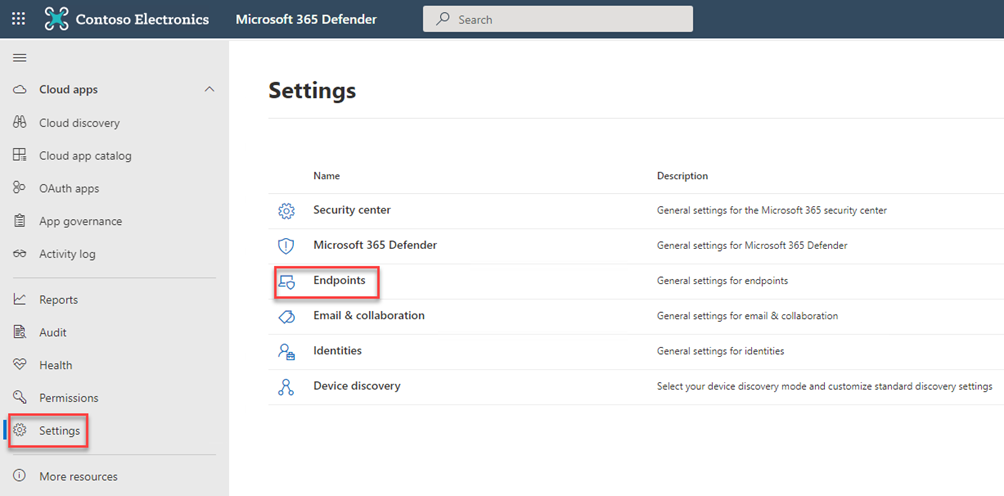
Find Onboarding and scroll down to the Run a detection test. Copy the script
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference= 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('http://127.0.0.1/1.exe', 'C:\\test-WDATP-test\\invoice.exe');Start-Process 'C:\\test-WDATP-test\\invoice.exe'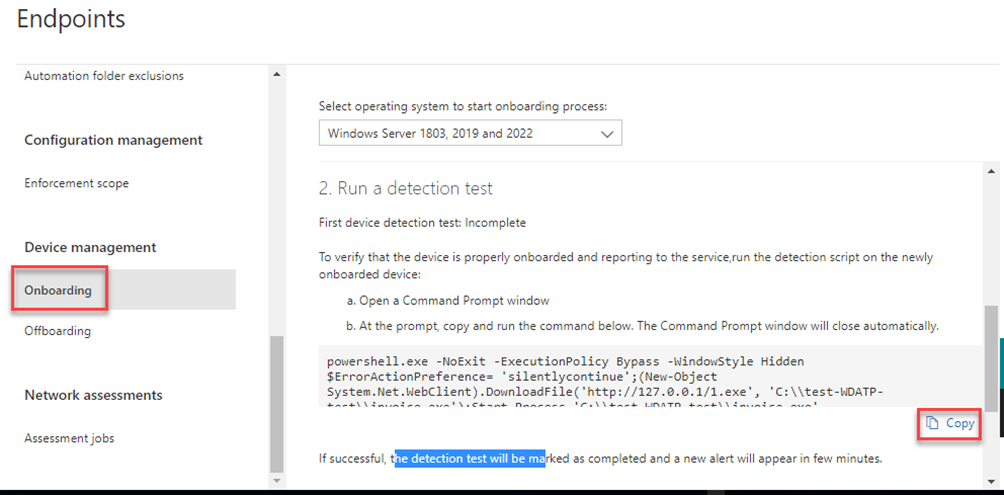
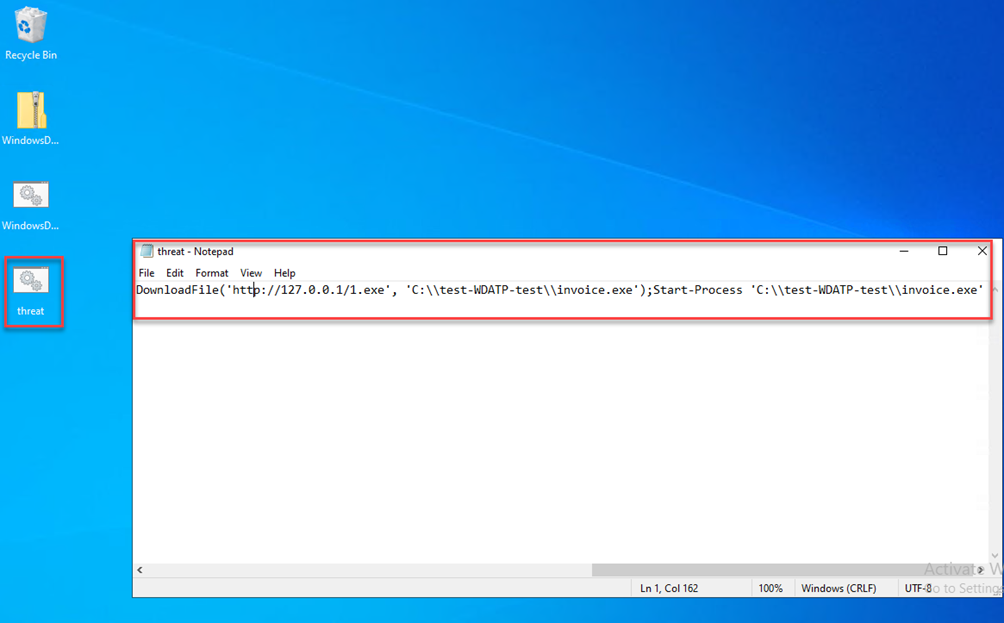
Create a bat file on your onboarded client and paste in the code here:
Then run the bat file.
Back in the MDE portal choose the onboarded client
https://security.microsoft.com/machines?category=endpoints
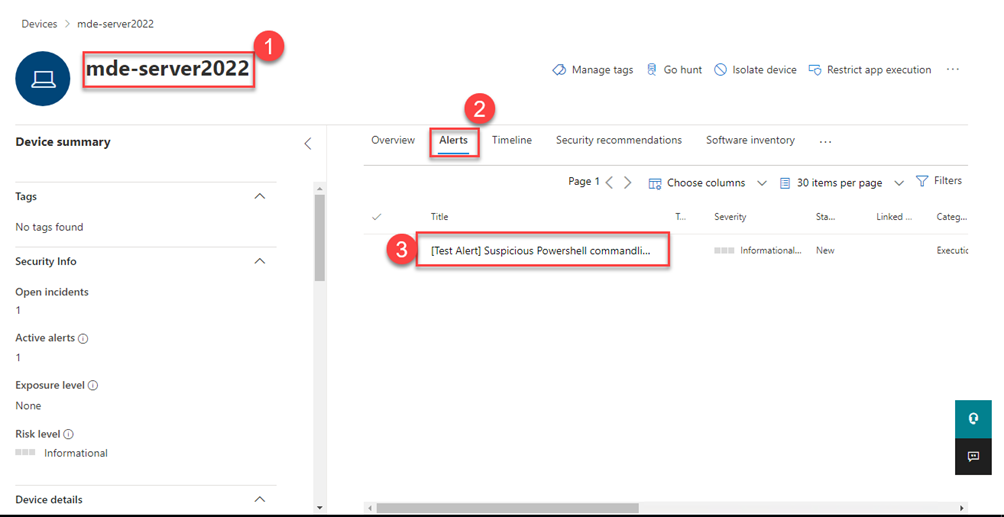
If you see a triggered alert, you know the connection is working and we have identified that we successfully onboarded our device to MDE.
Well Done!
Target policies to MDE managed device through Intune
Now it is time for us to target the MDE managed devices through Microsoft Intune. Go to the portal
Windows – Microsoft Endpoint Manager admin center
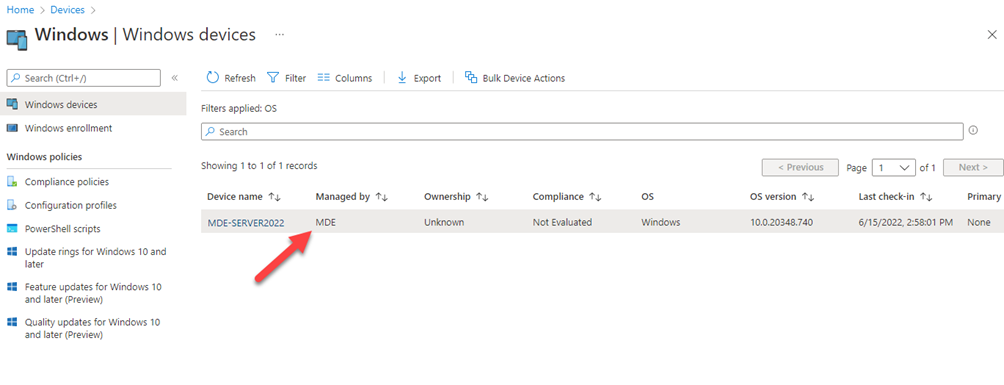
INFO:
MDE devices will receive only security management policy from Intune. Devices that need more functionality from Endpoint Manager should utilize the full endpoint manager stack.
Let us add some policies to the device
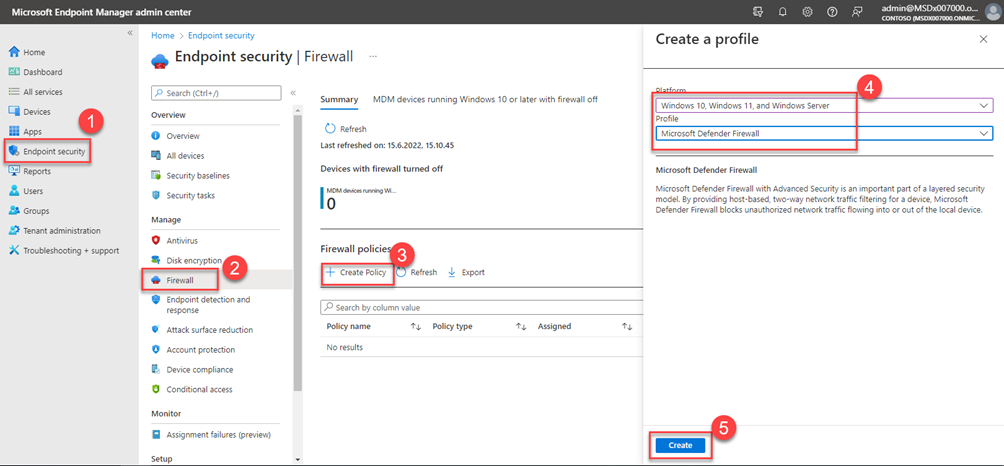
Click on
- Endpoint Security
- Firewall
- Create Policy
- Windows 10, Windows 11, and Windows Server + Microsoft Defender Firewall
- Create
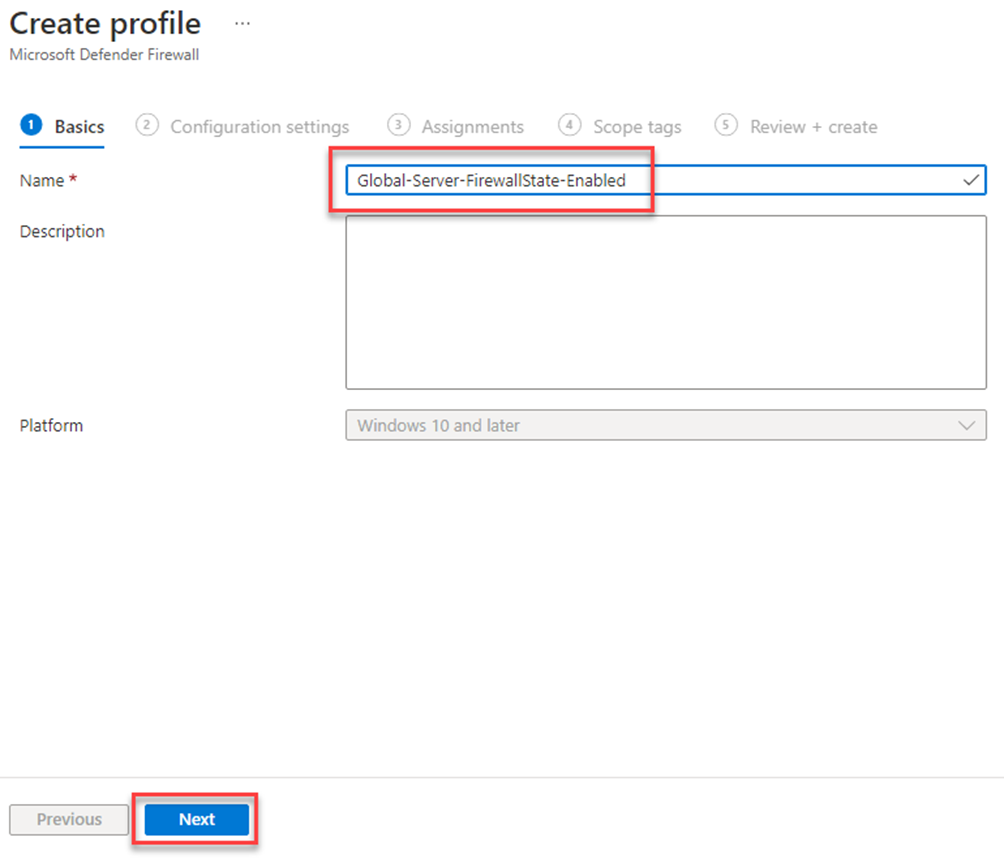
Let us practice a good naming standard
Click Next
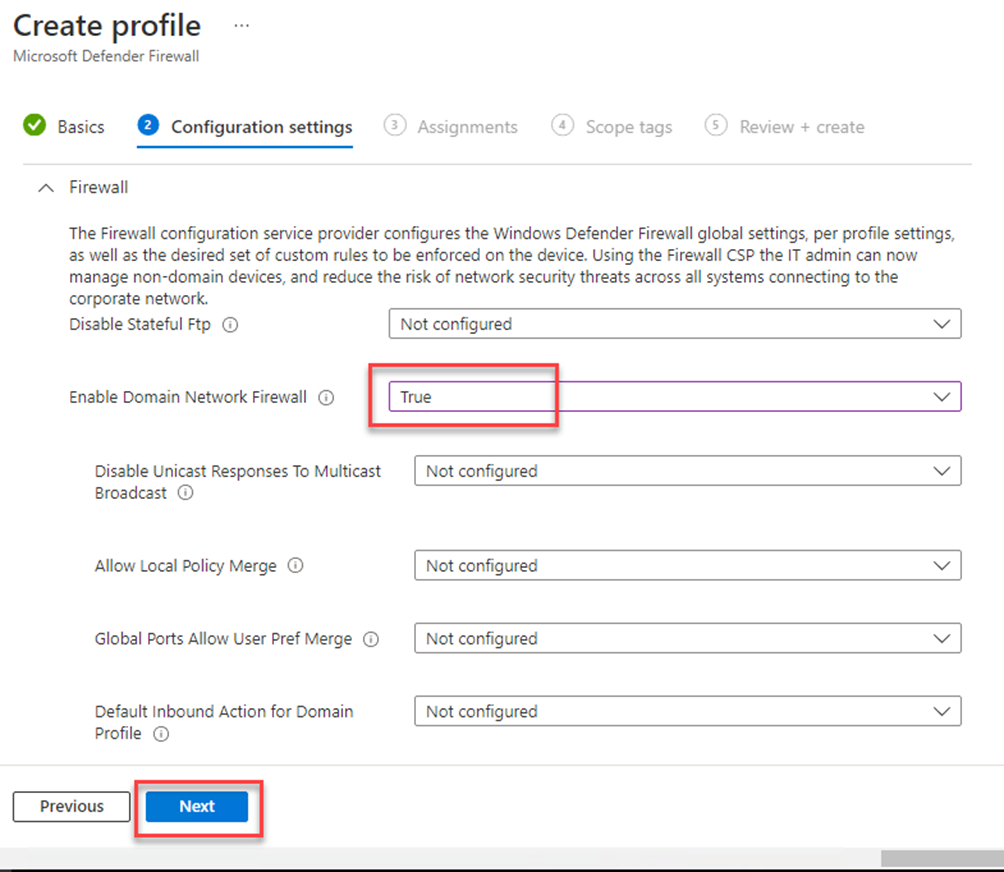
Configure the Enable Domain Network Firewall to True and click Next
Click Add groups choose MEM-MDE-Wave0 and click Select and then Next
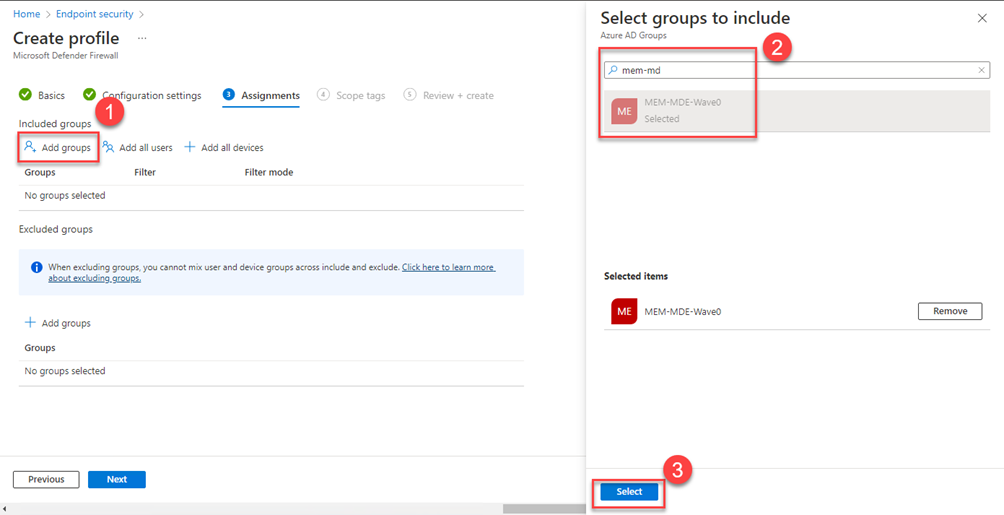
Click Next
Review the configuration and click Create
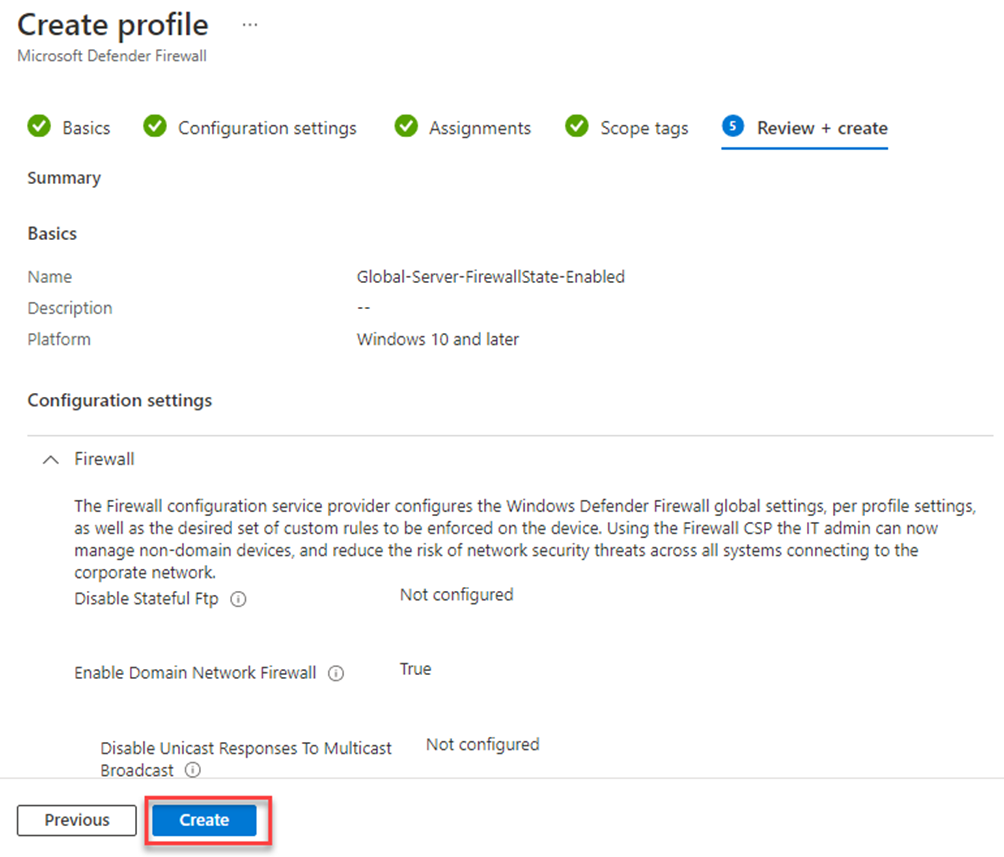
Now it is time to be patient. There is no sync button to push to have your policy coming down to the device. By default, MDE has an interval of syncing which I have not been able to find in the MS docs. Therefore, I cannot comment on that part.
You could restart the server to speed up things but mark my words. BE PATIENT.
If we go back to Intune and look at the policy we created for firewall, you will see that the policy apply to your MDE managed device.
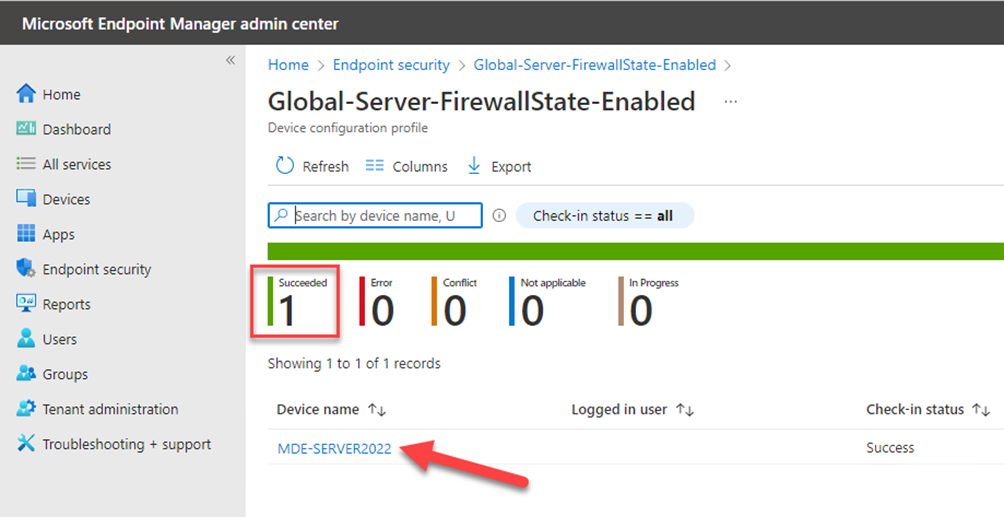
We can verify that setting has been enabled on the onboarded server
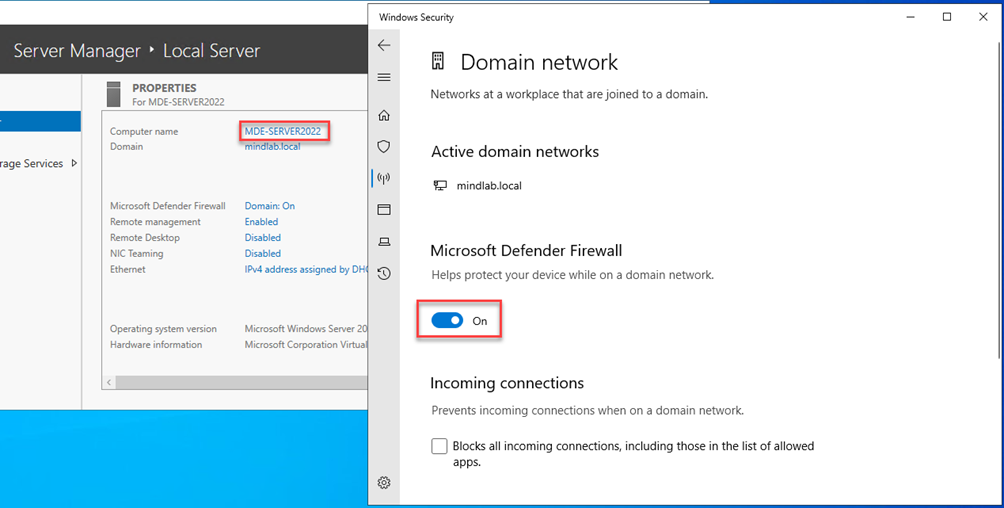
All good here. We’ve gone through how to setup all connectors in order to target devices with policies that is not enrolled in MDM (Intune) but only in MDE.
As some extra bonus I did create antivirus policies as well (not covered by this blogpost) and see the results of that:
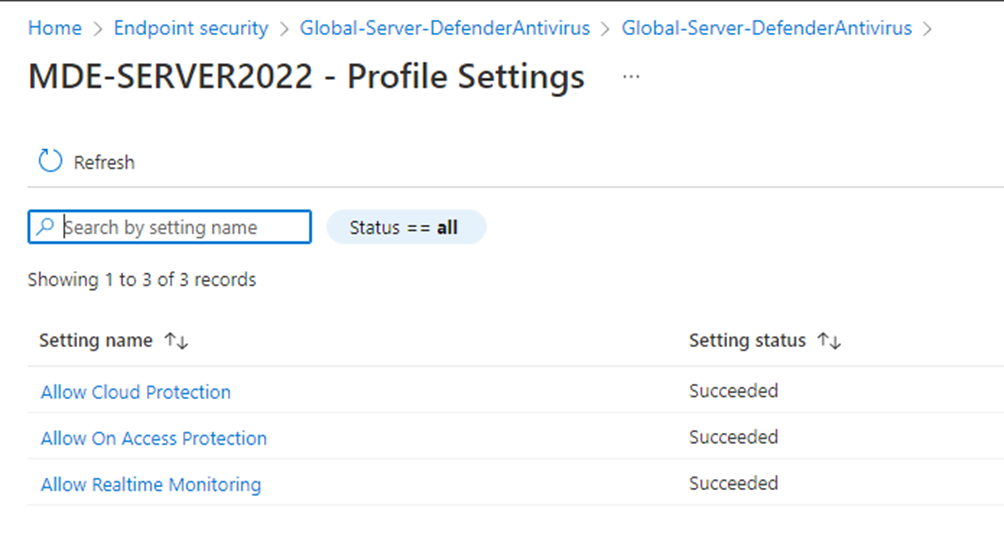
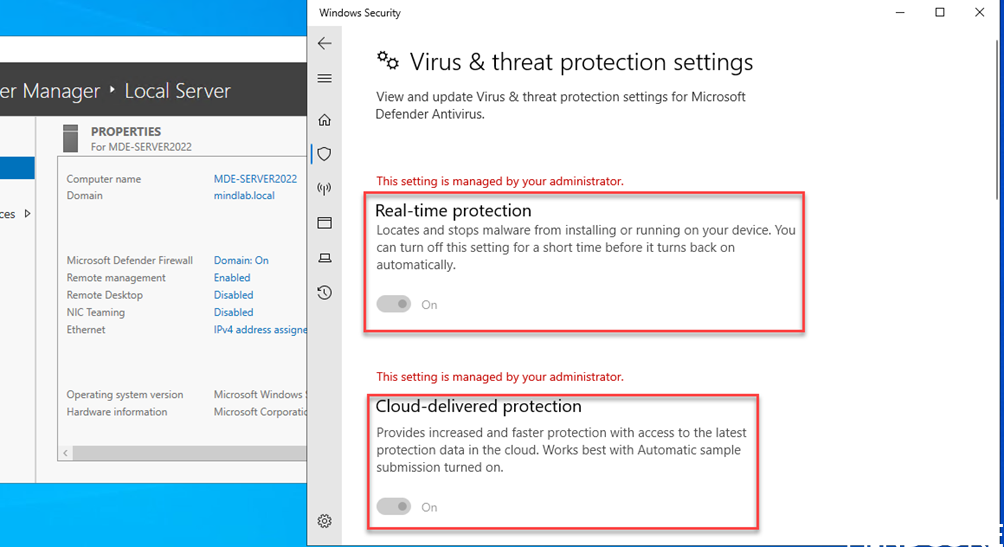
Just beautiful right?
Summary
In this blog post I have shown you have to create all the connectors needed in Intune + MDE in order to manage devices. We can manage devices through the MDM channel. We can manage devices through the MDE channel and we can even manage devices through Configuration Manager using Tenant Attach.
This Endpoint Security feature within Intune is so feature rich and will become more and more attractive to use.
Happy onboarding of your servers into Microsoft Defender for Endpoint!
Mattias Melkersen is a community driven and passionate modern workplace consultant with 20 years’ experience in automating software, driving adoption and technology change within the Enterprise. He lives in Denmark and works at Mindcore.
He is an Enterprise Mobility Intune MVP, Official Contributor in a LinkedIn group with 41.000 members and Microsoft 365 Enterprise Administrator Expert.
Mattias blogs, gives interview and creates a YouTube content on the channel "MSEndpointMgr" where he creates helpful content in the MEM area and interview MVP’s who showcase certain technology or topic.
Official Contributor here "Modern Endpoint Management":
https://www.linkedin.com/groups/8761296/














