Yes, you read it right. Assign ASR rules with Intune on servers. This does not mean we can enroll servers to Intune, so how is this then possible?
If you remember my post back in 2022 where I wrote about MDE managed devices and the way to apply policies to your servers and clients not enrolled in Intune you can continue reading this post.
If not, I strongly suggest you start by reading this blog before going any further, and understand high-level how this works.
Following What’s new in Intune, or this What’s new in Intune YouTube series you would know about this announcement from Microsoft already.
I am going to show how to start testing this new available feature and how it looks like.
First we need to go and visit the new setting we have in the MDE portal: (it changed since last time I blogged about this setting)
Settings -> Endpoints -> Enforcement scope
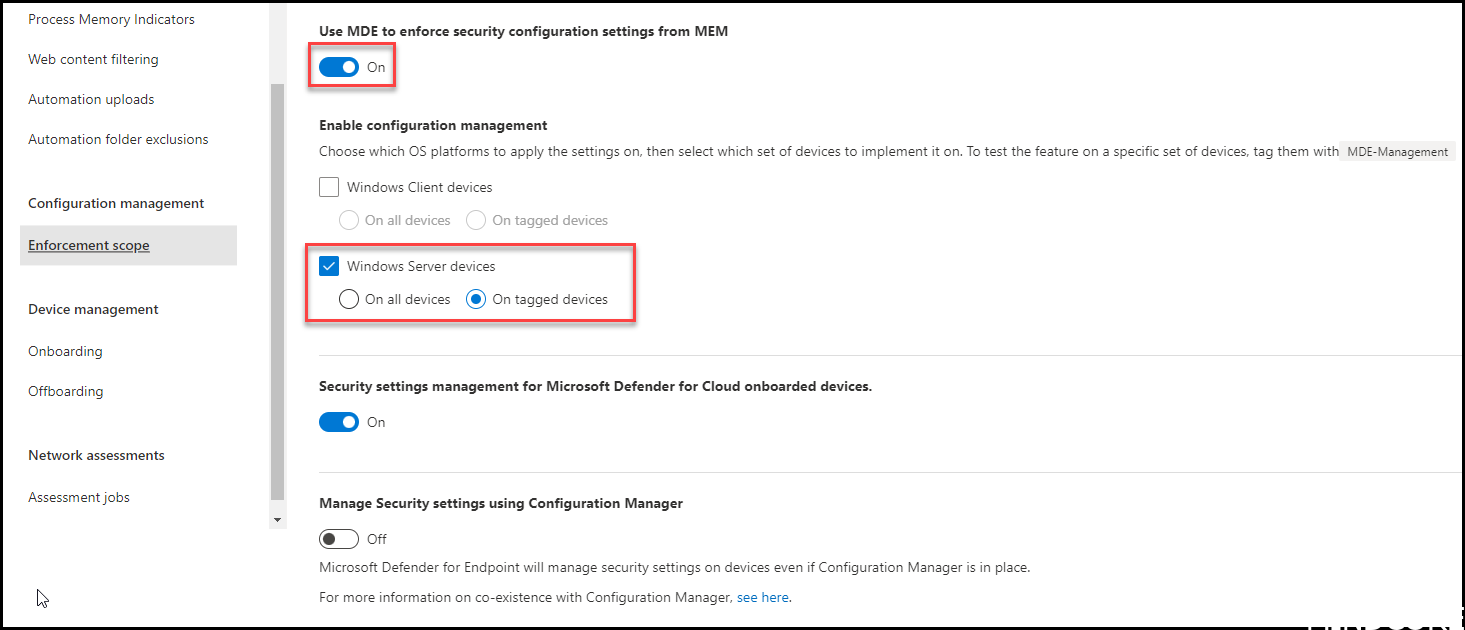
I have enabled the portal to let Intune be able to enforce security configurations to my MDE managed devices. In this case only Windows Servers and on “tagged” devices where they have the tag “MDE-Management”.
This means that not all my servers will be “added” to the Intune portal, but only the tagged ones. Really good starting point to see if this is something you like to use in your organisation!
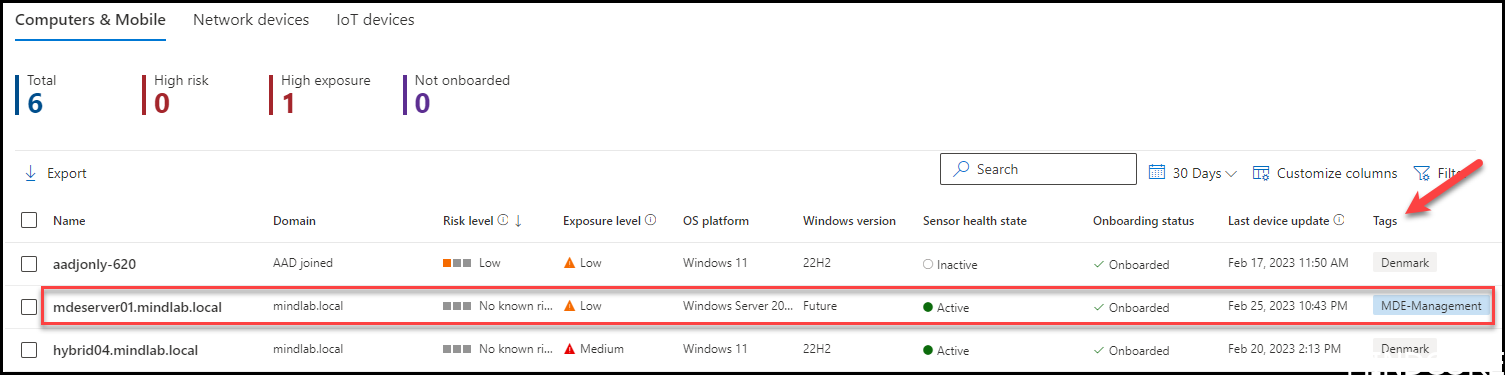
After a while you will be able to see your server onboarded to Microsoft Intune Admin Center.
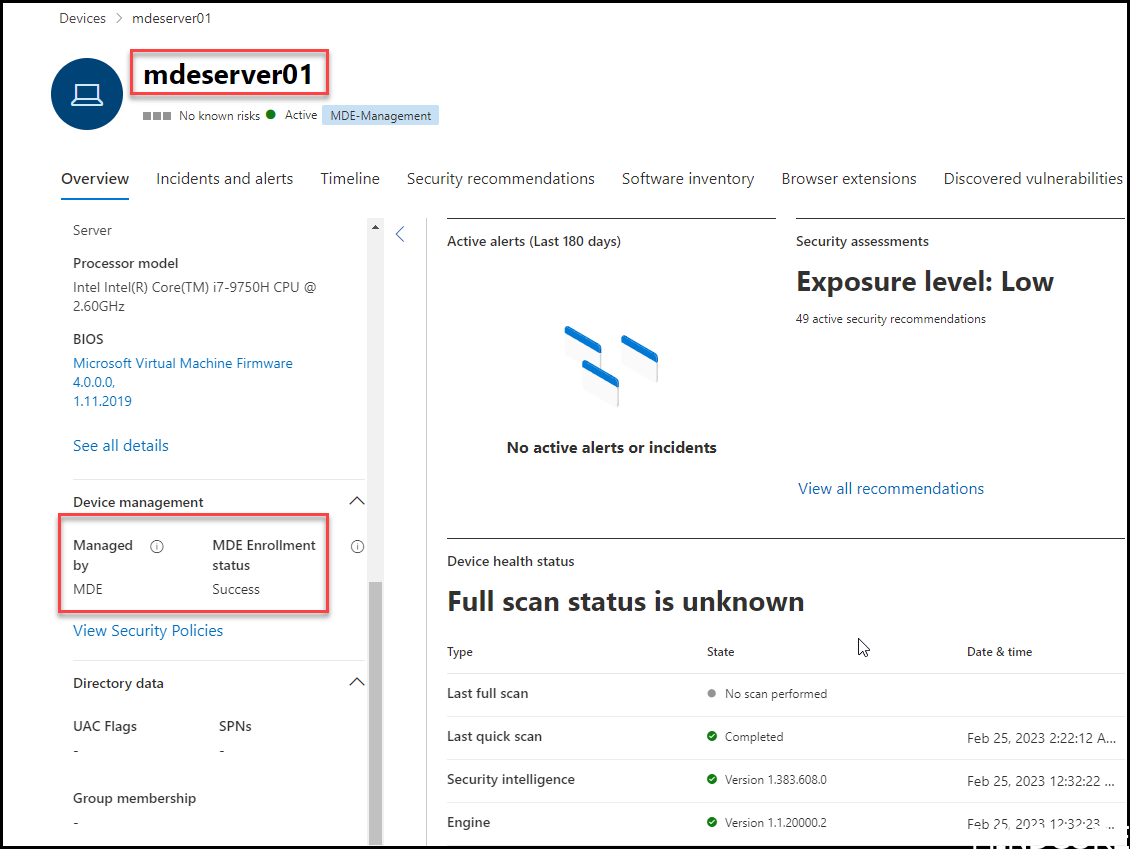
And in Intune we see the MDE managed server which is NOT enrolled within Intune with the “Managed by” MDE
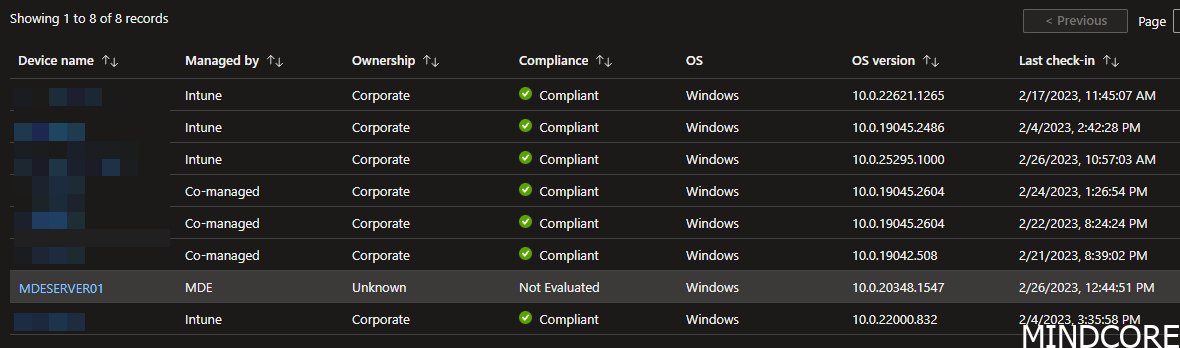
Time to verify ASR on the server just to make sure there are no ASR rules defined on the server prior to doing it with policies through Intune and the MDE channel.
Jumping into the Intune portal which just got rebranded from Microsoft Endpoint admin center to Microsoft Intune admin center. Go to Endpoint security
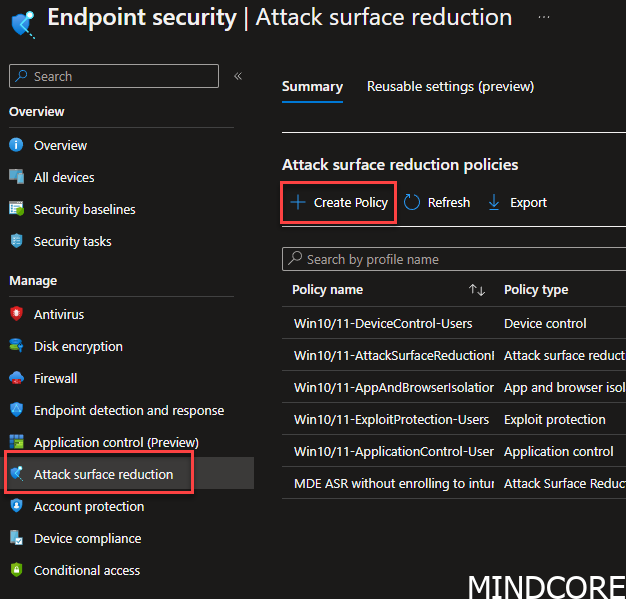
Go to Attack surface reduction and press Create Policy
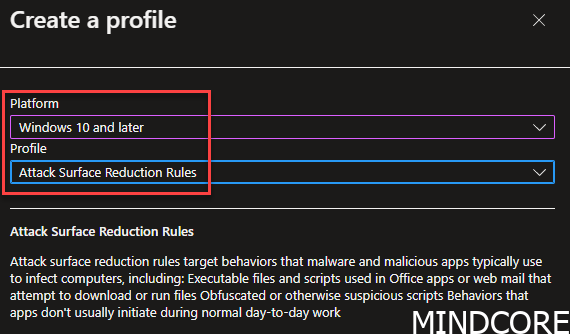
Choose Windows 10 and later and Attack Surface Reduction Rules
INFO: This policy is normally called “Windows 10, Windows 11, and Windows Server.
I think a bug has sneaked in with the new 2302 UI upgrade.
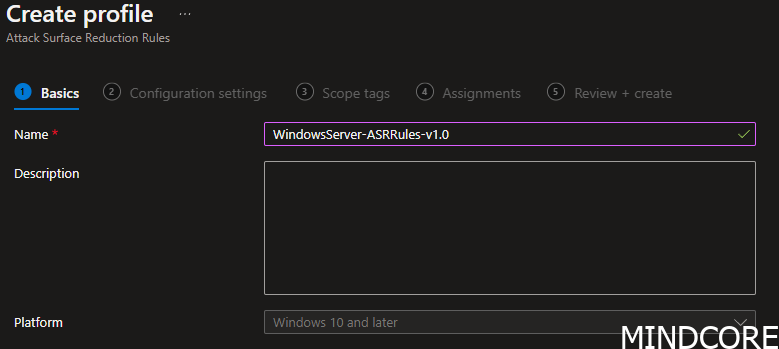
Always, use some good naming standards. It will help you better determine what you applied to your devices when you need to review it.
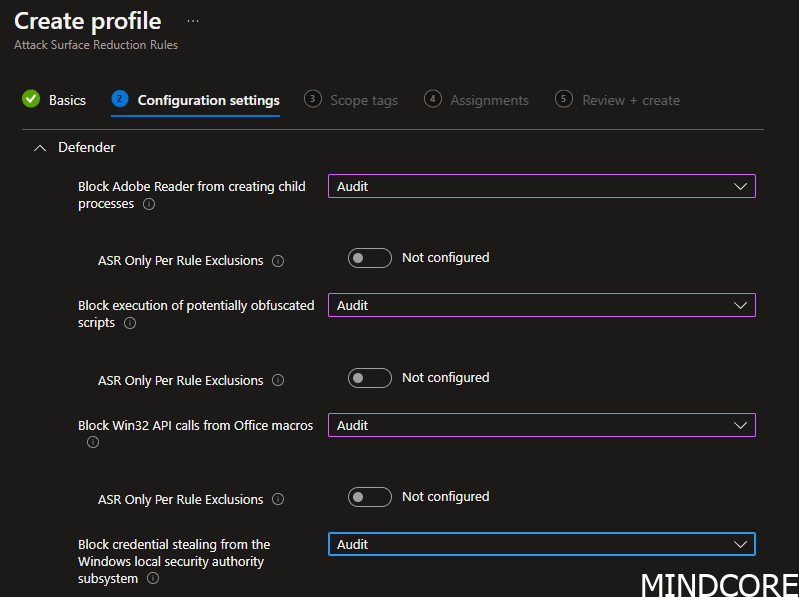
Start out by using Audit to start getting data to your defender report.
We enable 4 rules just for the example. You should consider all 16.
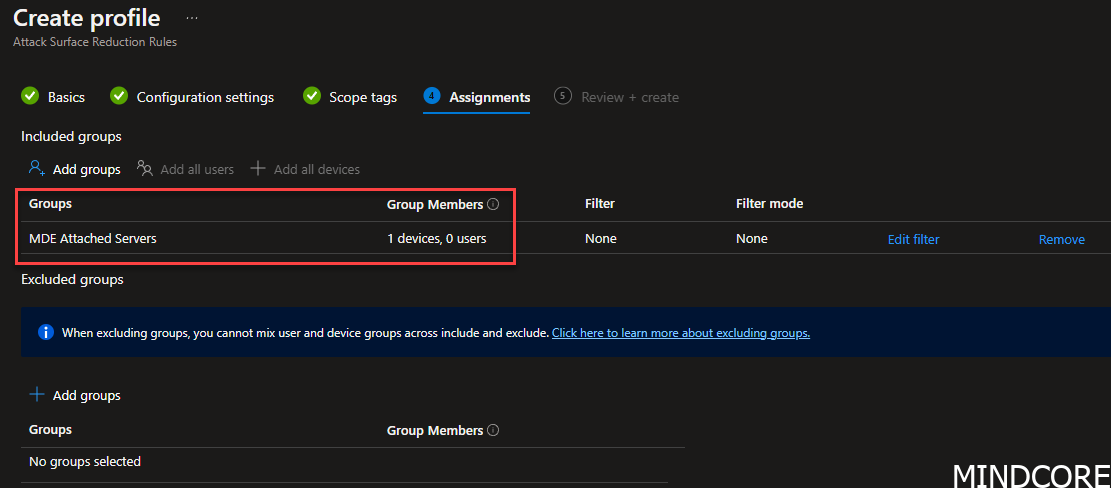
Choose the AAD group containing your server(s). Very cool feature we got within Intune that tells us exactly how many devices we are targeting.
Click Create
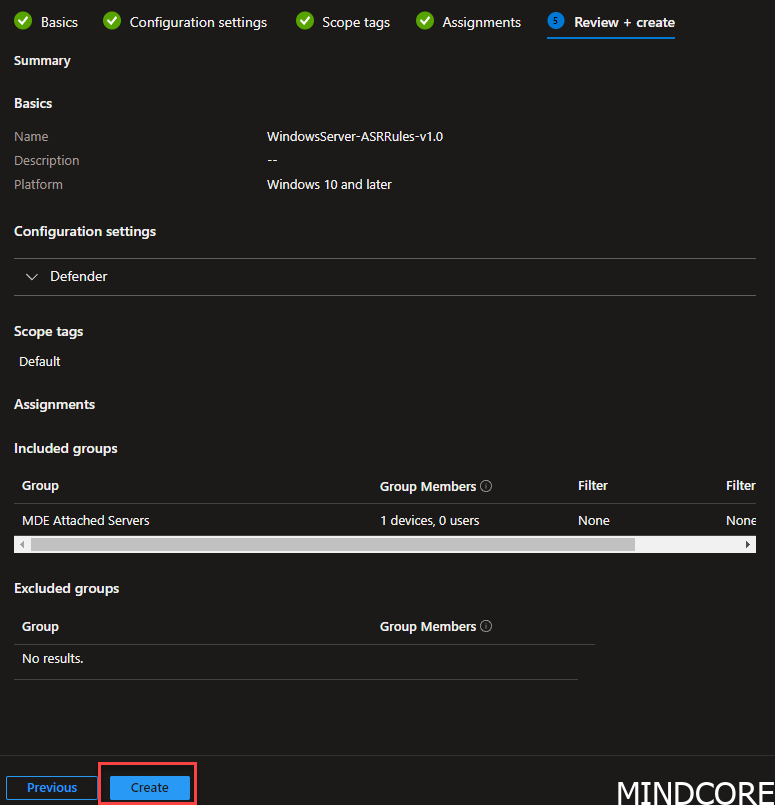
We can see the difference on the target model here. MicrosoftSense is what will help deliver this policy to the windows server without the need to enroll!
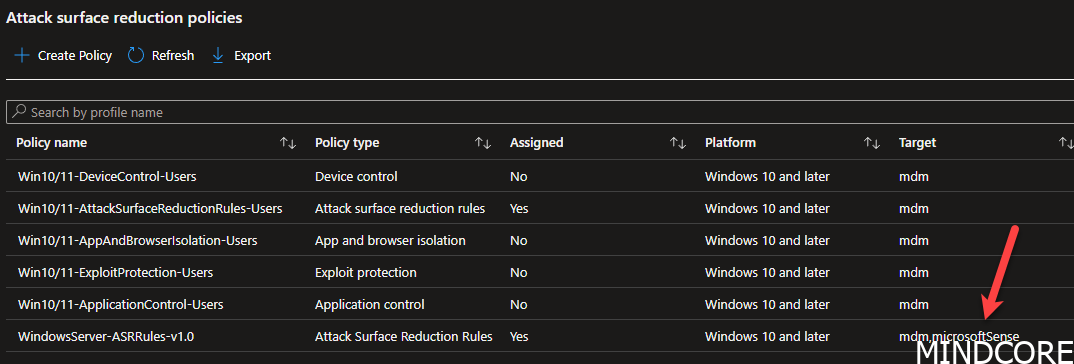
To get faster result, I reboot my server as it will then sync straight away. If you are in no hurry, just wait. It will get synced automatically. You have no real way to force it.
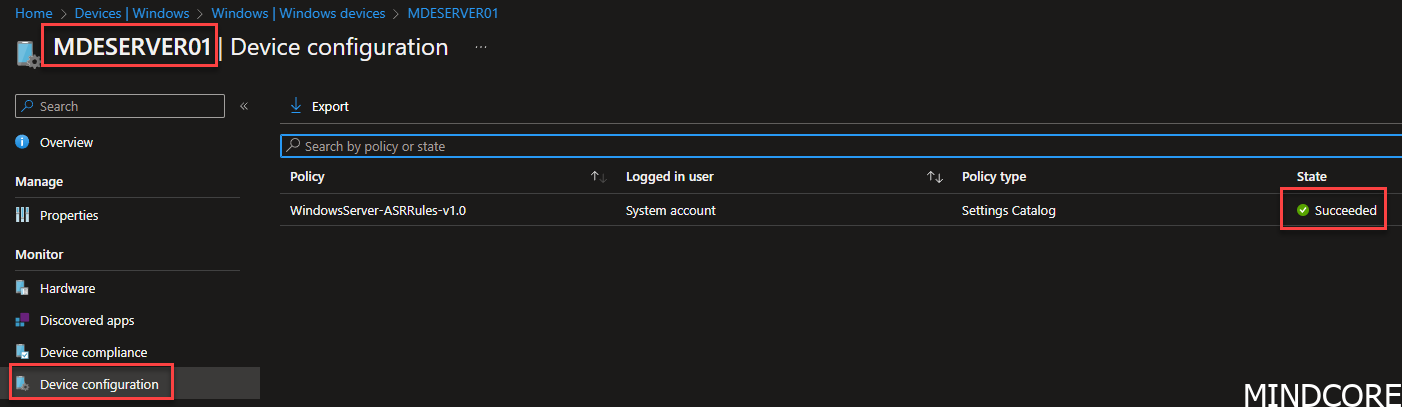
After the reboot we can see that my server got ASR rules applied.
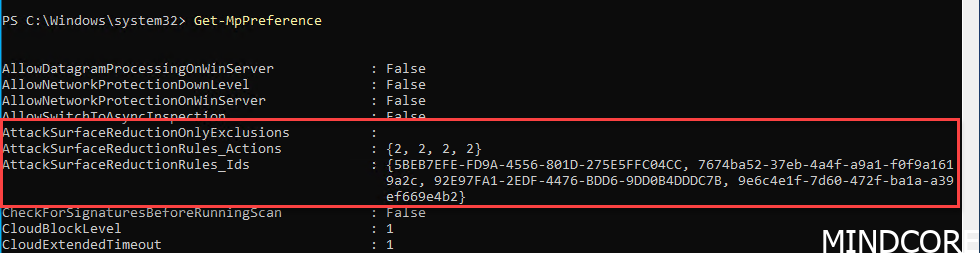
And as you can see, we added 4 rules in audit mode, and we got 4 rules applied
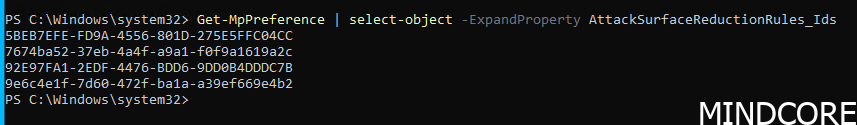
And if we look into the Intune portal, we see the same result, that the policy applied. VERY Cool indeed.
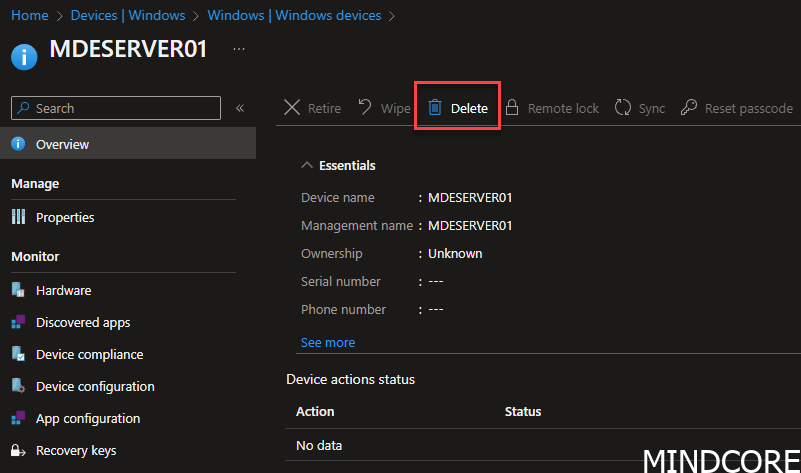
And just as a closing note. Before the Intune built 2302 it was not possible to delete the device manually from the portal. You had to off board it from the MDE portal and just wait for it to automatically remove it. Now we can delete it 👏
Summary
In this case you have devices that are not enrolled to Intune e.g. servers and you want to apply policies for those, there are pretty good alternatives, as we just saw here in this blogpost. In other words, assigning policies comes in many flavors.
Being able to send out policies like, Antivirus, Firewall settings, Firewall rules and attack surface reduction rules, is a huge win. Happy deployment 😁
Mattias Melkersen is a community driven and passionate modern workplace consultant with 20 years’ experience in automating software, driving adoption and technology change within the Enterprise. He lives in Denmark and works at Mindcore.
He is an Enterprise Mobility Intune MVP, Official Contributor in a LinkedIn group with 41.000 members and Microsoft 365 Enterprise Administrator Expert.
Mattias blogs, gives interview and creates a YouTube content on the channel "MSEndpointMgr" where he creates helpful content in the MEM area and interview MVP’s who showcase certain technology or topic.
Official Contributor here "Modern Endpoint Management":
https://www.linkedin.com/groups/8761296/














