Why do we need Role based access controls (RBAC)?
In the dynamic world of modern IT management, the need for fine-tuned control and enhanced efficiency has become more crucial than ever. Microsoft Intune, a powerful cloud-based solution, empowers organizations to streamline their endpoint management and secure their devices, applications, and data. Within Intune’s extensive suite of features lies a game-changing capability known as Custom Role-Based Access Control (RBAC).
Intune Custom RBAC Roles are a versatile and advanced approach to access management, enabling administrators to tailor permissions with surgical precision. Gone are the days of a one-size-fits-all approach to user roles, as organizations can now create bespoke roles to meet the specific needs of their unique workflows and security requirements.
However there is one common thing that I’ve come across while implementing this at customers. The possibility to create support cases are not an option and therefore a must to expand your RBAC scope to Entra ID. In this blog post I will describe how you will enable your custom RBAC roles to also be able to create Microsoft support cases.
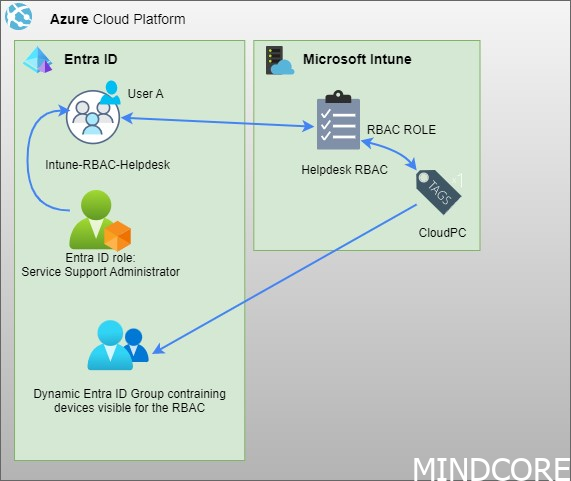
Scenario
You have custom RBAC roles in your Intune environment and you need to grant access to the operations team to create Microsoft tickets. Today there are currently no good solutions for this request (Unless you use the built-in roles), but I will give you tips on how to build a unified RBAC for this scenario in this blog post.
Disclaimer!
This solution will only work for natively created Entra ID groups.
Synced groups from AD can not be enabled for Entra ID role assignments, read more here
You might think, I can create a native Entra ID group and then make my synced group nested. I applaud your thinking, but no sir, this will not work, see screenshot.

Set the scene
Let’s set the scene, shall we?
I have created a custom helpdesk role and given that several permissions. A piece of good advice when creating custom roles is to duplicate one of the existing built-in roles to have a building block not to start from scratch. From there you can peal your onion and slice it as you like your custom role to be like
If we go and have a look under assignments for this particular group you will notice that I have assigned it to an Entra ID Group called MEM-RBAC-Helpdesk
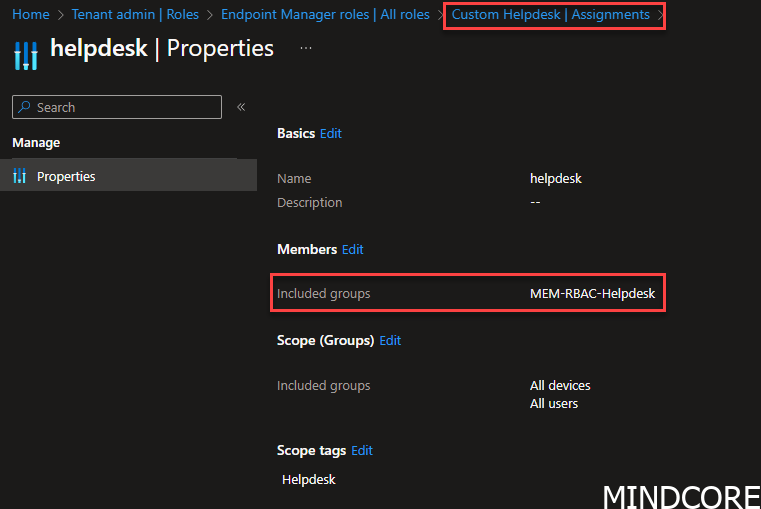
This means if I put a user into the group MEM-RBAC-Helpdesk, my user will be able to access the Intune portal and be able to work with the scope-tagged devices and the UI chosen for this RBAC role.
Least access privileges
Now onto our mission, to make our custom role able to create support tickets with Microsoft.
The permission we are interested in is named: Microsoft.office365.supportTickets/allEntities/allTasks
This will enable a user to be able to create tickets in the Intune portal.
The above permission is something we only will find in Entra ID. Therefore what we need is to assign permission from Entra ID, easy enough?
Currently, when trying to assign custom RBAC roles from Entra ID you cannot specify only microsoft.office365.supportTickets/allEntities/allTasks so we need to look at the current built-in admin roles and see what fits our needs with the least access privileges.
To find the least access privileges, we can ask MS Graph for permissions on the different roles by going to Graph Explorer | Try Microsoft Graph APIs – Microsoft Graph and run this query:
GET v1.0 https://graph.microsoft.com/v1.0/roleManagement/directory/roleDefinitions
Copy the response preview into a notepad document and start searching for Microsoft.office365.supportTickets
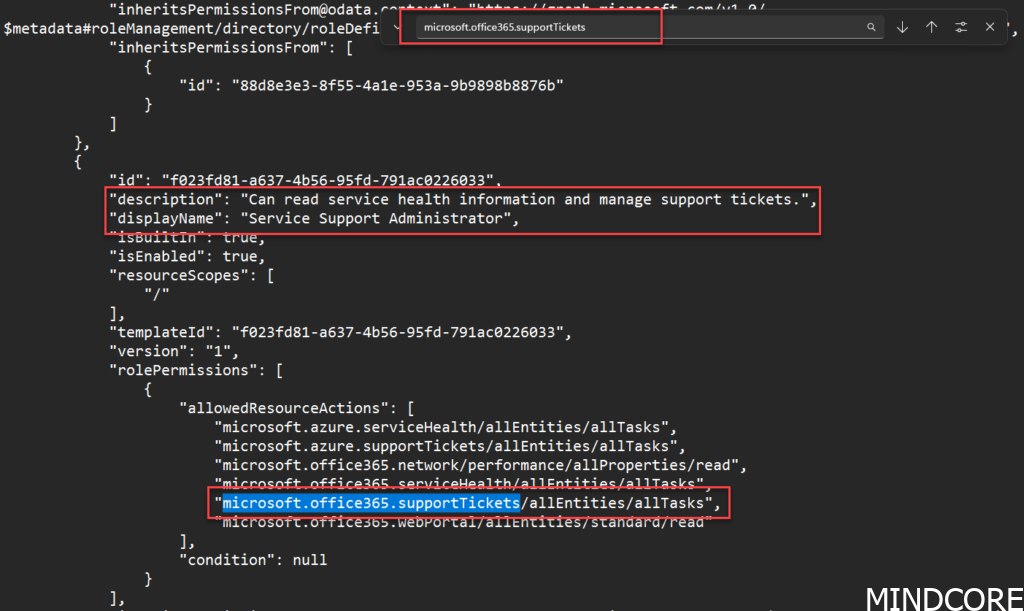
You will quickly find out that the least access privilege model for allowing ticket creation will be the: Service Support Administrator.
Update the RBAC role
Now we know that we need to assign this role in Entra ID to our group.
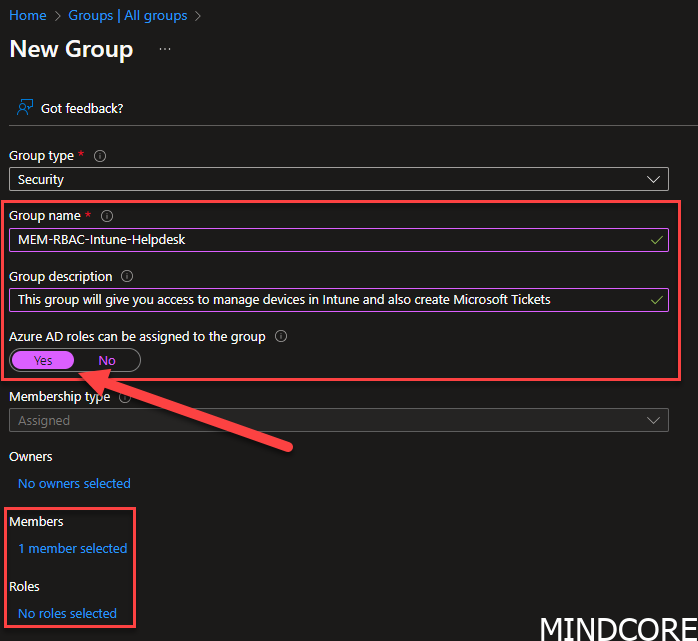
Start by creating a new Entra ID group. Give it a good name, and description and remember to tick the Azure AD roles that can be assigned to the group, otherwise, this will never work.
Add members you like to be able to access the RBAC role and click Roles
in Roles you will add the Service Support Administrator
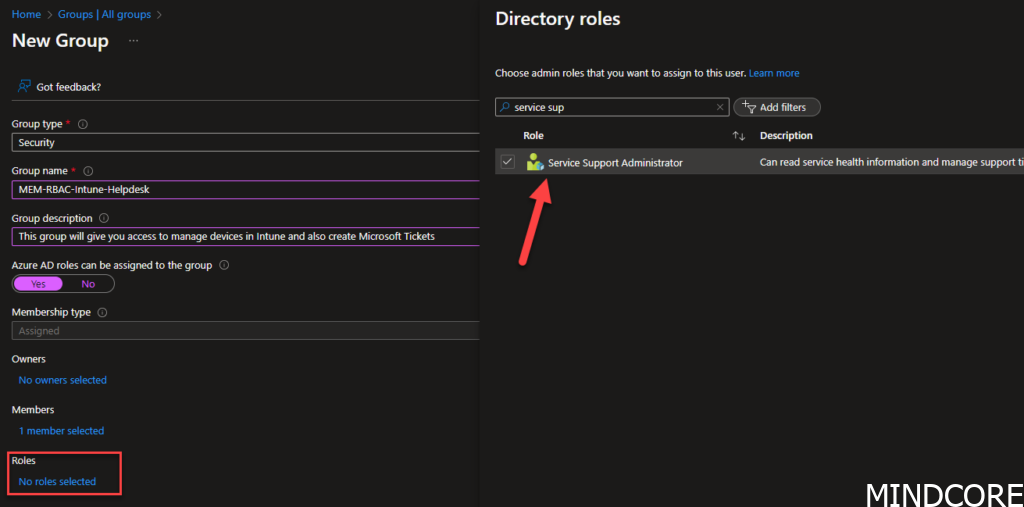
Click yes
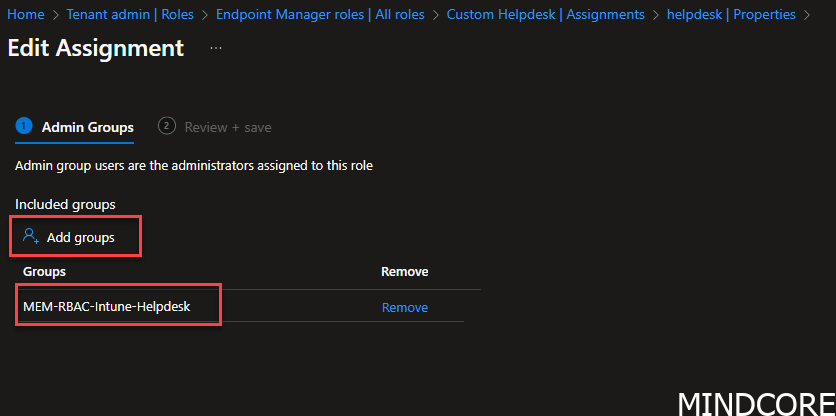
Go to your Intune RBAC role -> Tenant administration -> Roles -> “Your custom role” -> Assignments -> edit members -> review and save it
Now your users of that RBAC role can start creating Microsoft Tickets without giving them full Intune permissions.
In the next post I’ll take you through another scenario, if you have third party identity/access management system and cannot use the native cloud Microsoft Entra ID groups with the assign role possibility. Stay tuned!
Happy management!
Mattias Melkersen is a community driven and passionate modern workplace consultant with 20 years’ experience in automating software, driving adoption and technology change within the Enterprise. He lives in Denmark and works at Mindcore.
He is an Enterprise Mobility Intune MVP, Official Contributor in a LinkedIn group with 41.000 members and Microsoft 365 Enterprise Administrator Expert.
Mattias blogs, gives interview and creates a YouTube content on the channel "MSEndpointMgr" where he creates helpful content in the MEM area and interview MVP’s who showcase certain technology or topic.
Official Contributor here "Modern Endpoint Management":
https://www.linkedin.com/groups/8761296/














