Introduction

This blog post is part of a series. If you did not see the first blogpost of the series, you should go through that first.
How I manage my device from Endpoint Manager – taste your own medicine – Part 1 of 4
How I manage my device from Endpoint Manager – taste your own medicine – Part 2 of 4
How I manage my device from Endpoint Manager – taste your own medicine – Part 3 of 4
In this blog post I will go through the security recommendations that MDATP suggested on my own device and will show you how this is implemented in Endpoint manager one by one, as we should know what the recommendations are and how to set them.
I started off with 57 security recommendations and this is my way towards 0 (or close to 0 )
Prerequisites
– Microsoft Defender Advanced Threat Protection license – for more information read here
– Microsoft Endpoint Manager
Table of content
Security Recommendation 31 Enable Network Protection
Security Recommendation 32 Disable Solicited Remote Assistance
Security Recommendation 33 Disable IP source routing
Security Recommendation 34 Set IPv6 source routing to highest protection
Security Recommendation 35 Set default behavior for AutoRun to not execute any autorun commands
Security Recommendation 36 Disable Configure Offer Remote Assistance
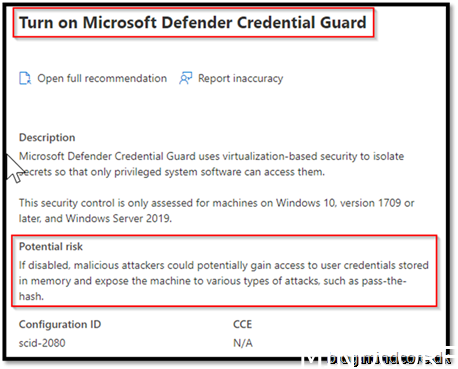
Security Recommendation 37 Turn on Microsoft Defender Credential Guard
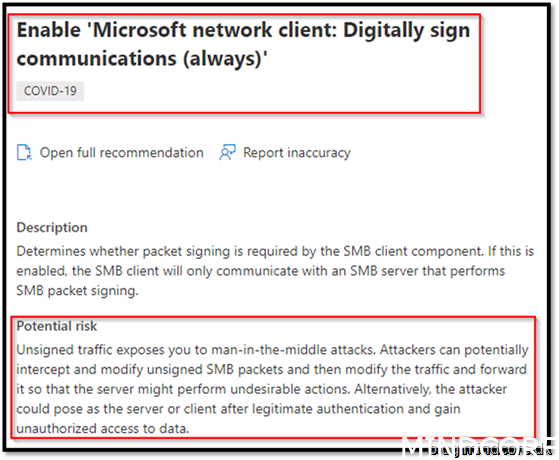
Security Recommendation 38 Enable Microsoft network client: Digitally sign communications (always)
Security Recommendation 39 Disable the local storage of password and credentials
Security Recommendation 40 Disable Anonymous enumeration of shares
Security Recommendation 41 Disable JavaScript on Adobe Reader DC
Security Recommendation 42 Disable Flash on Adobe Reader DC
Security Recommendation 43 Disable Installation and configuration of Network Bridge on your DNS domain network
Security Recommendation 44 Disable Always install with elevated privileges
Security Recommendation 45 Enable Local Admin password
Security Recommendation 46 Set LAN Manager authentication level to Send NTLMv2 response only. Refuse LM & NTLM
Let’s make my device more secure
Fire up your Microsoft edge browser (if you do not have that installed, now is the time)
Go to https://securitycenter.microsoft.com/
Choose Device inventory, select your device and see Security Recommendations for your device.
Security Recommendation 31 Enable Network Protection
Go to https://endpoint.microsoft.com/ -> Endpoint security -> Attack surface reduction
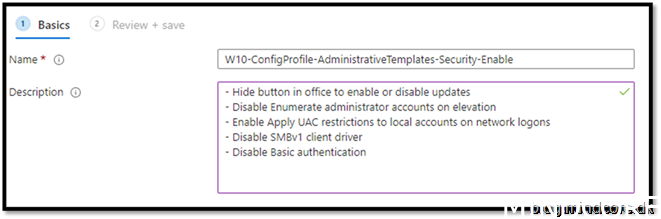
Give it a friendly name
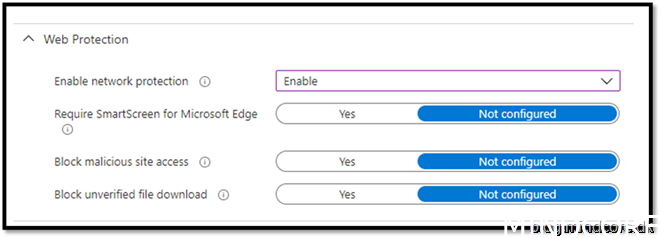
Assign to your device and create the policy.
Security Recommendation 32 Disable Solicited Remote Assistance
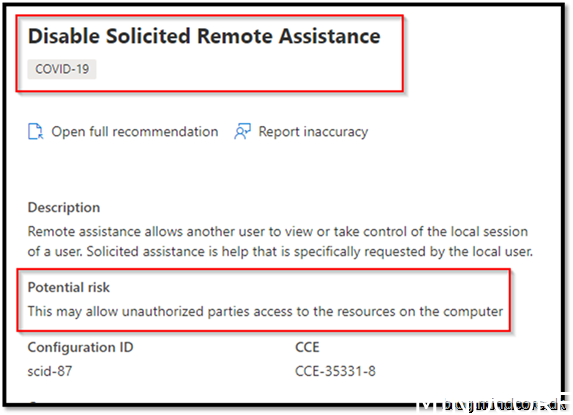
Covid 19 has sneaked into this one! If you disable this one you will not be able to use remote assistance, so if that is the current used solution, this option should not be added to your security baseline.
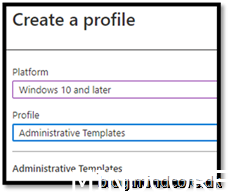
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> Configuration Profiles
Create Profile
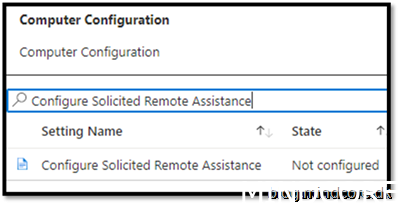
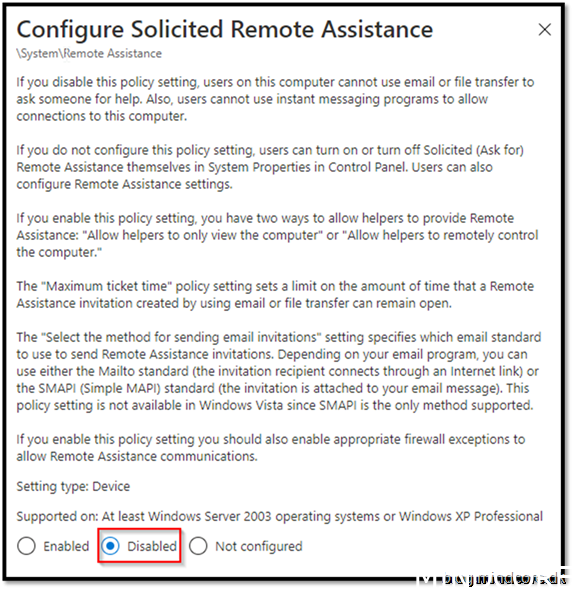
Disabled
Assign it to your device and save it.
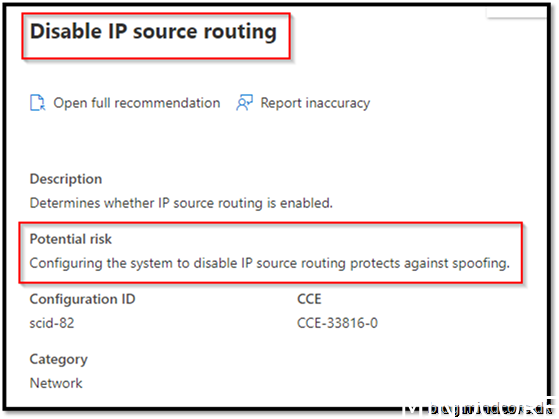
Security Recommendation 33 Disable IP source routing
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> Configuration Profiles
Create Profile
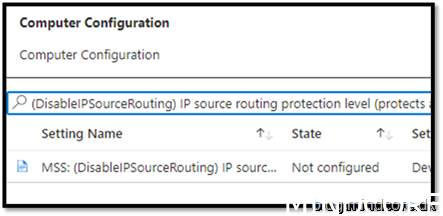
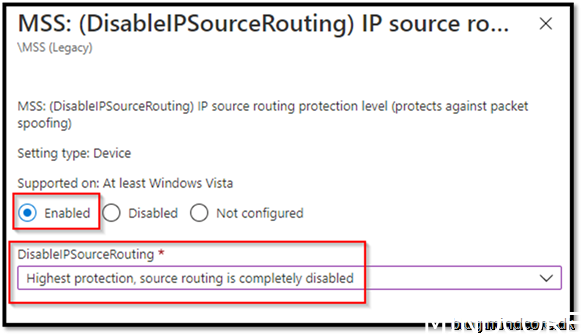
Enabled
Assign it to your device and save it.
Security Recommendation 34 Set IPv6 source routing to highest protection
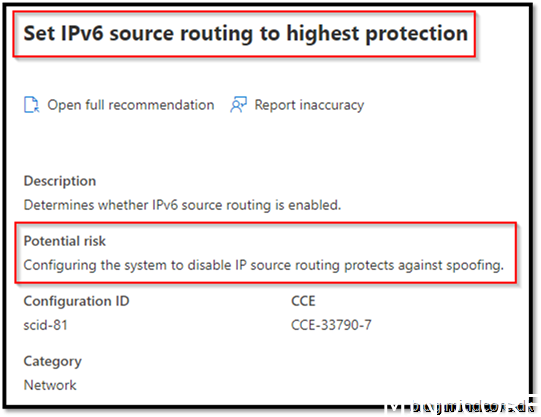
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> Configuration Profiles
Create Profile
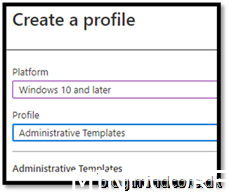
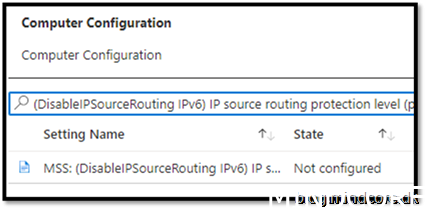
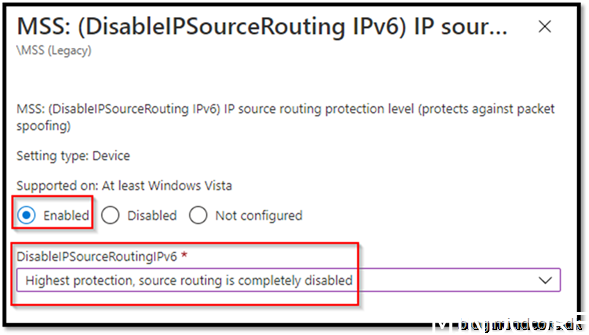
Enabled
Assign it to your device and save it.
Security Recommendation 35 Set default behavior for AutoRun to not execute any autorun commands
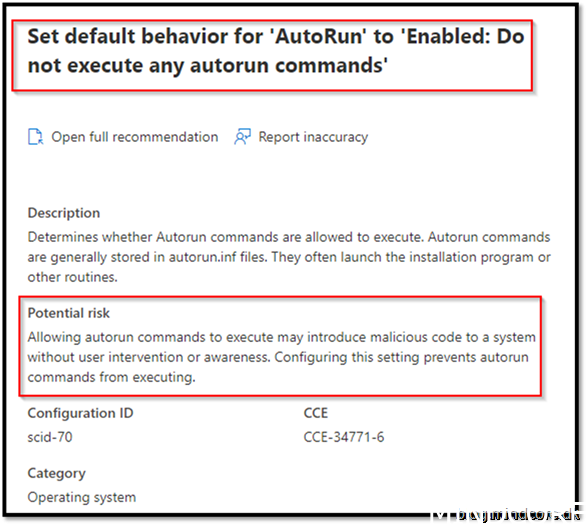
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> Configuration Profiles
Create Profile
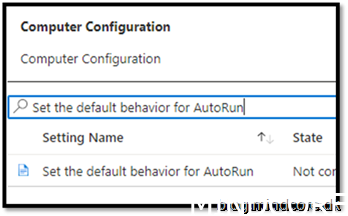
Enabled
Assign it to your device and save it.
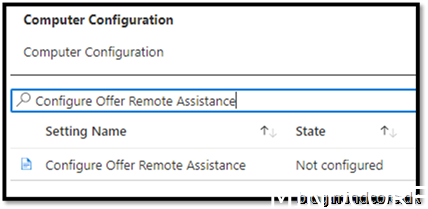
Security Recommendation 36 Disable Configure Offer Remote Assistance
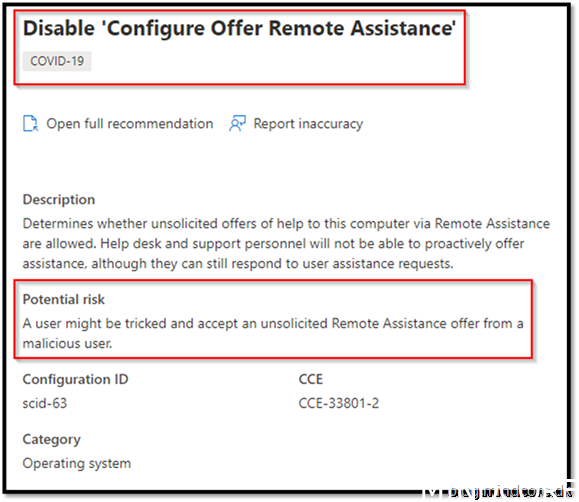
If you use Remote assistance as your solution to take over devices, this policy should not be applied!
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> Configuration Profiles
Create Profile
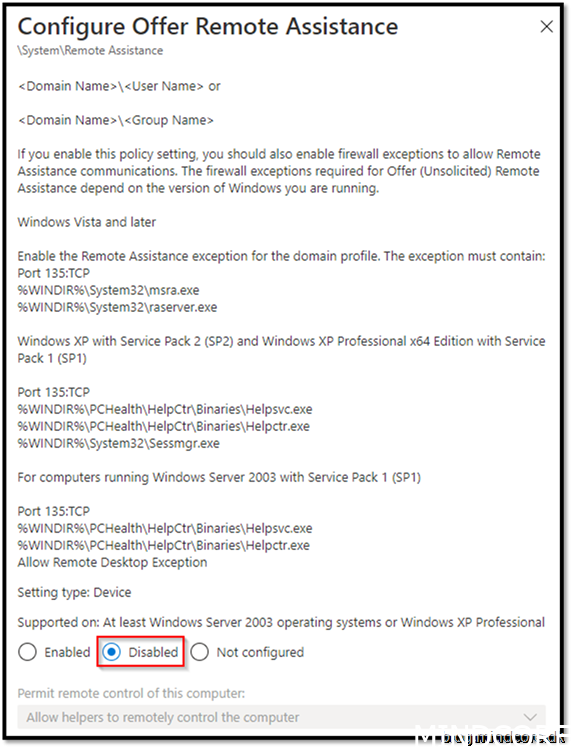
Disabled
Assign it to your device and save it.
Security Recommendation 37 Turn on Microsoft Defender Credential Guard
If you use Remote assistance as your solution to take over devices, this policy should not be applied!
Go to https://endpoint.microsoft.com/ -> Endpoint security -> Account protection
Create Policy
Give it a friendly name
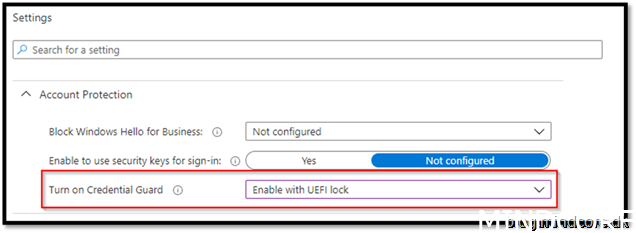
Assign it to your device and save it.
Security Recommendation 38 Enable Microsoft network client: Digitally sign communications (always)
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> Configuration Profiles
Create Profile
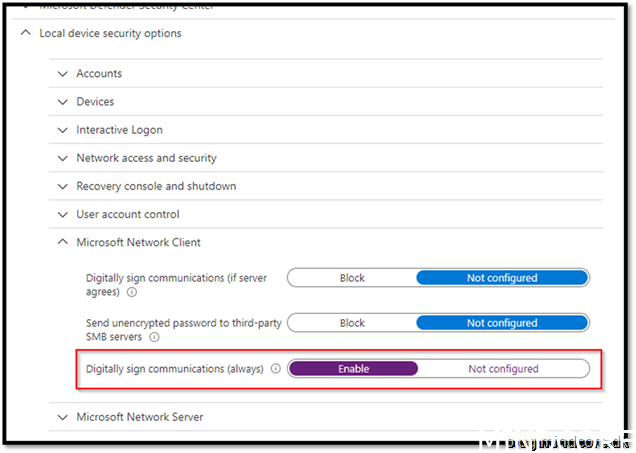
Enabled
Assign it to your device and save it.
Security Recommendation 39 Disable the local storage of password and credentials
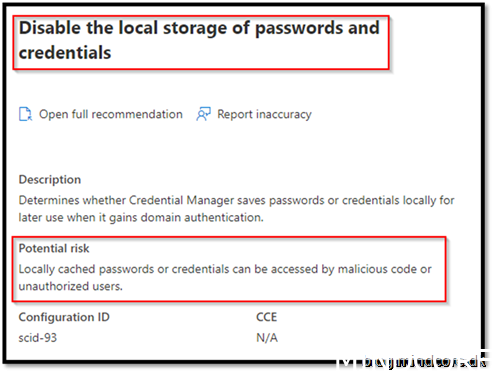
This setting has currently (to my knowledge) no UI yet.
Therefore, we are forced to create a PowerShell script to add the registry key mentioned.
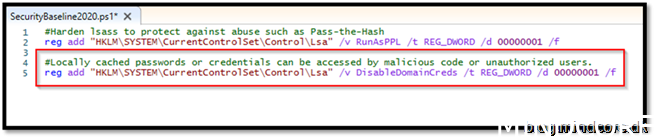
Save the script
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> PowerShell scripts
Add
Give it a friendly name
Add to a security group
Add –> done
Security Recommendation 40 Disable Anonymous enumeration of shares
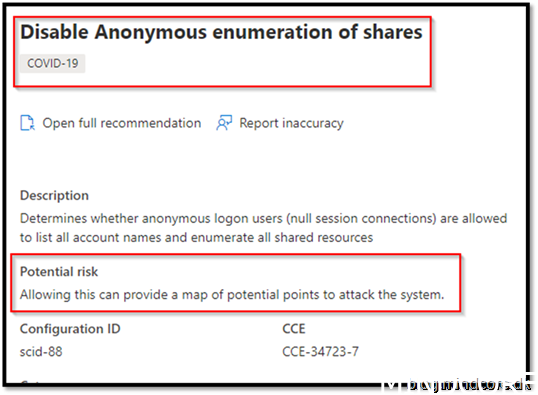
This setting has currently (to my knowledge) no UI yet.
Therefore, we are forced to create a PowerShell script to add the registry key mentioned.
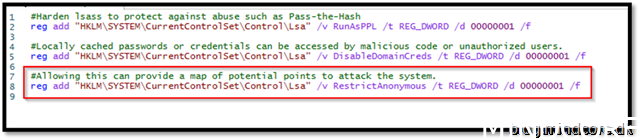
Save the script
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> PowerShell scripts
Add
Give it a friendly name
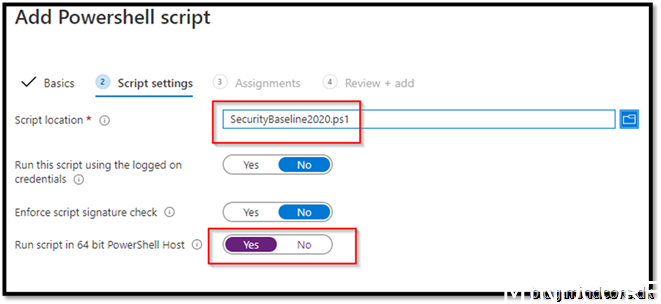
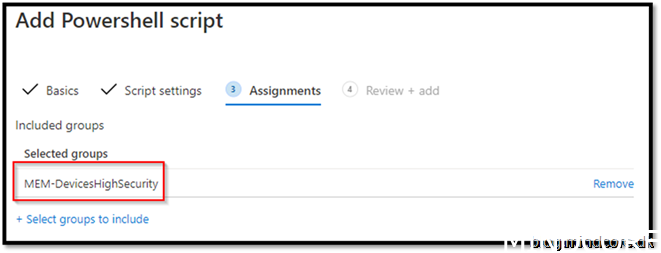
Add to a security group
Add –> done
Security Recommendation 41 Disable JavaScript on Adobe Reader DC
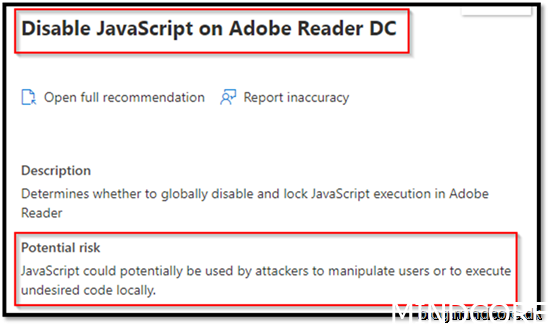
This setting should go into the Acrobat Reader package deployment. But in this example, we will just add it to our baseline security script.
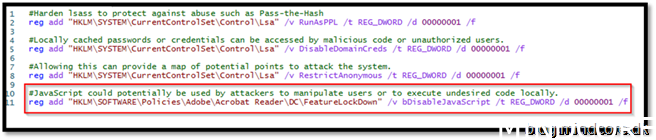
Save the script
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> PowerShell scripts
Add
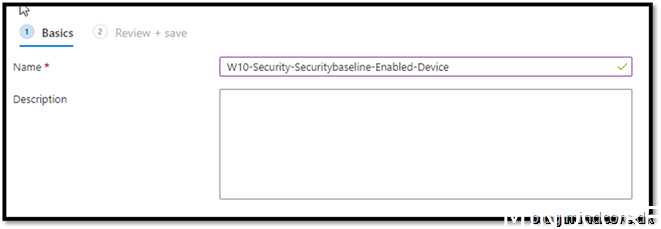
Give it a friendly name
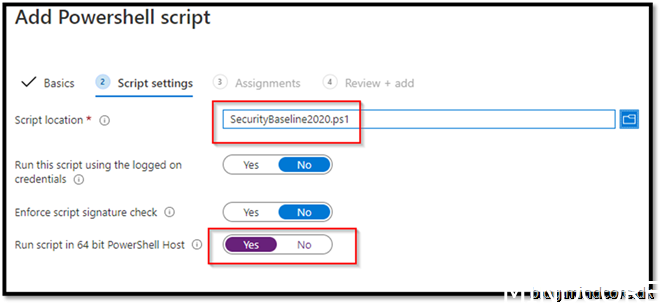
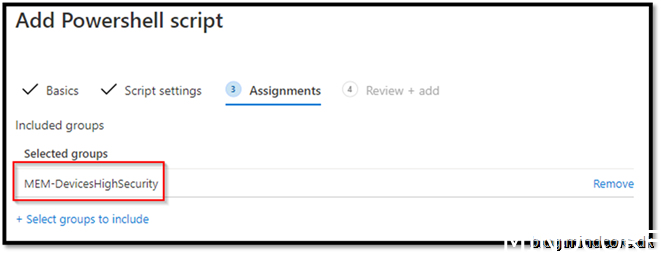
Add to a security group
Add –> done
Security Recommendation 42 Disable Flash on Adobe Reader DC
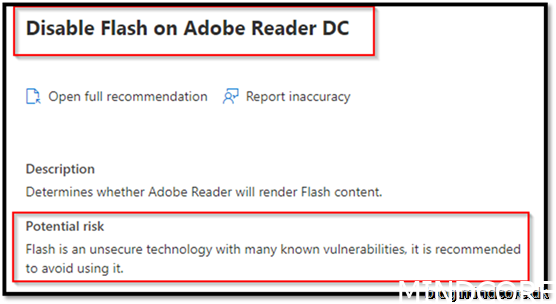
This setting should go into the Acrobat Reader package deployment. But in this example, we will just add it to our baseline security script.
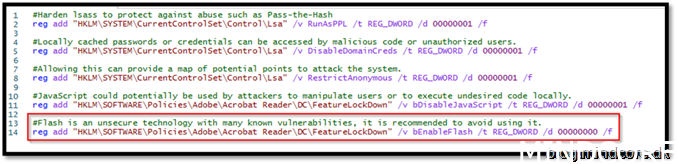
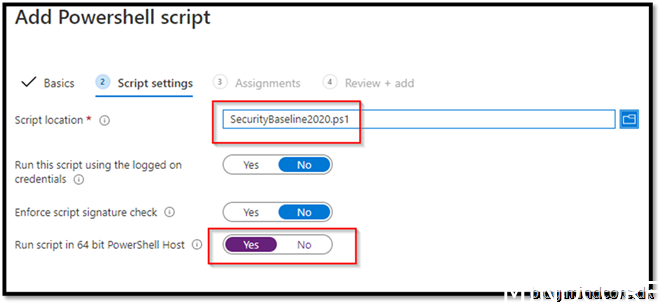
Save the script
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> PowerShell scripts
Add
Give it a friendly name
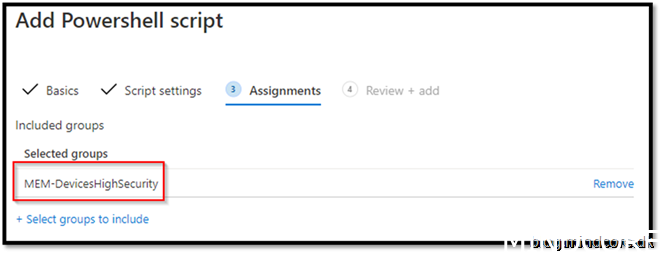
Add to a security group
Add –> done
Security Recommendation 43 Disable Installation and configuration of Network Bridge on your DNS domain network
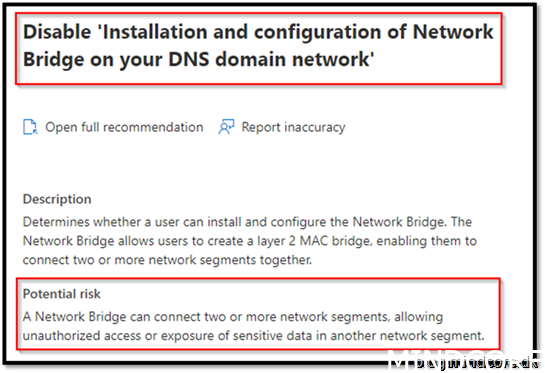
If you use Remote assistance as your solution to take over devices, this policy should not be applied!
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> Configuration Profiles
Create Profile
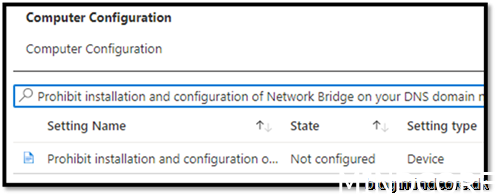
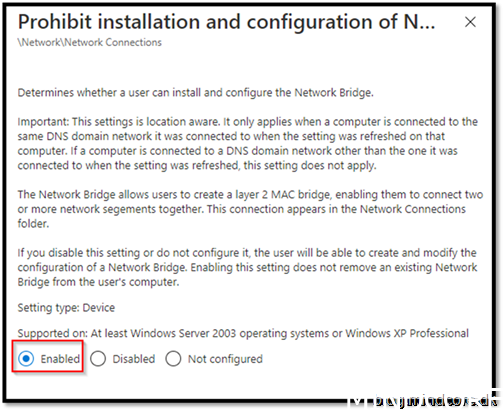
Enabled
Assign it to your device and save it.
Security Recommendation 44 Disable Always install with elevated privileges
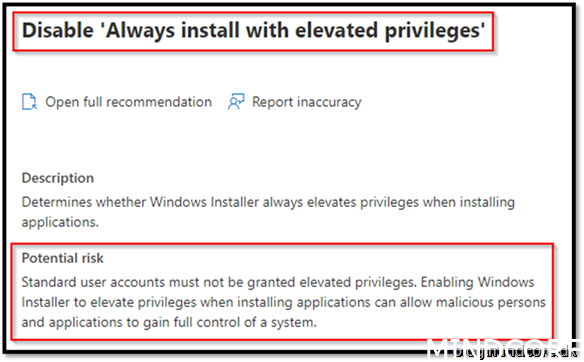
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> Configuration Profiles
Create Profile
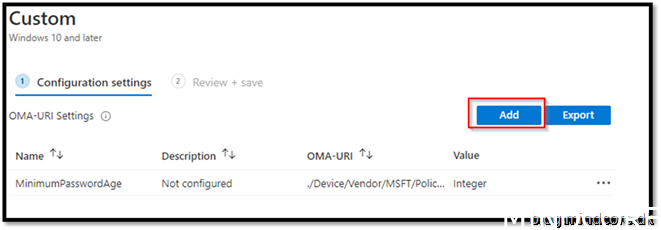
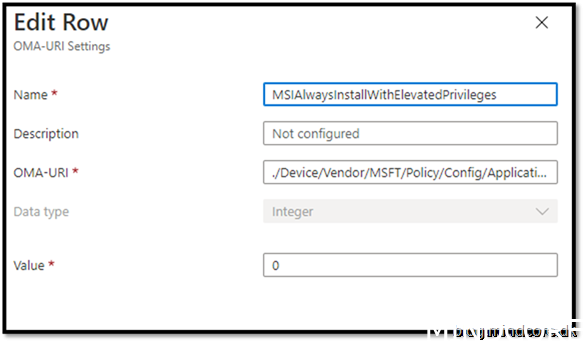
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/ApplicationManagement/MSIAlwaysInstallWithElevatedPrivileges
Security Recommendation 45 Enable Local Admin password
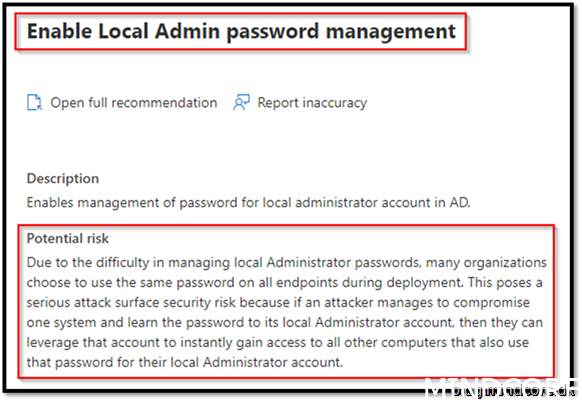
My device does not have a local admin enabled, so this recommendation does not apply to my device
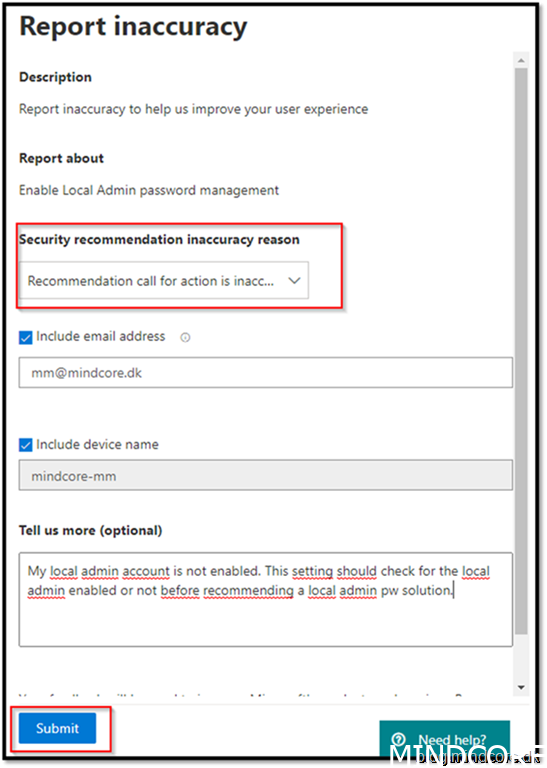
I reported inaccuracy as I believe the recommendation should be cleverer.
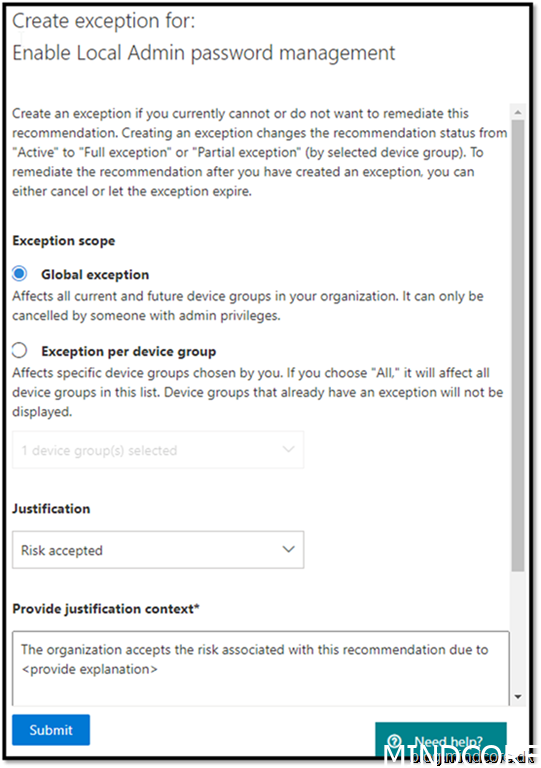
I accept the risk as we do not use local administrators here. That are most likely not the case in a larger corporate company, and you should always make sure your local admin is safe.
Security Recommendation 46 Set LAN Manager authentication level to Send NTLMv2 response only. Refuse LM & NTLM
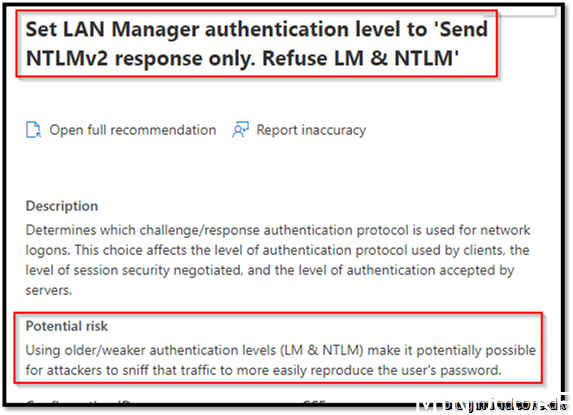
To my knowledge there are currently no setting for this.
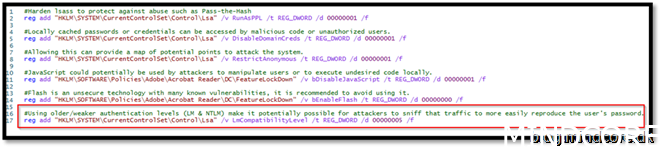
Save the script
Go to https://endpoint.microsoft.com/ -> Devices -> Windows -> PowerShell scripts
Add
Give it a friendly name
Add to a security group
Add -> done
Summary
MDATP is highly recommended to gain more insight of how your security score
And with these settings put onto my device I only have 9 security recommendation left out of 57.
Happy implementation!
Mattias Melkersen is a community driven and passionate modern workplace consultant with 20 years’ experience in automating software, driving adoption and technology change within the Enterprise. He lives in Denmark and works at Mindcore.
He is an Enterprise Mobility Intune MVP, Official Contributor in a LinkedIn group with 41.000 members and Microsoft 365 Enterprise Administrator Expert.
Mattias blogs, gives interview and creates a YouTube content on the channel "MSEndpointMgr" where he creates helpful content in the MEM area and interview MVP’s who showcase certain technology or topic.
Official Contributor here "Modern Endpoint Management":
https://www.linkedin.com/groups/8761296/














