Microsoft Remote Help is a powerful tool that allows users to get technical support and assistance from your company’s IT Pros without leaving the comfort of their own homes or offices. With Microsoft Remote Help, users can connect remotely to a support technician who can troubleshoot, diagnose, and solve technical issues with their Microsoft products and services. It exists as a standalone add-on license or as part of the new Intune Suite. The tool just got an upgrade on security as it now has collaboration with Azure Active Directory feature Condition Access. In this blog post, I will demonstrate how you easily can upgrade your security by only allowing compliant devices to launch and use Remote Help.
Prerequisites
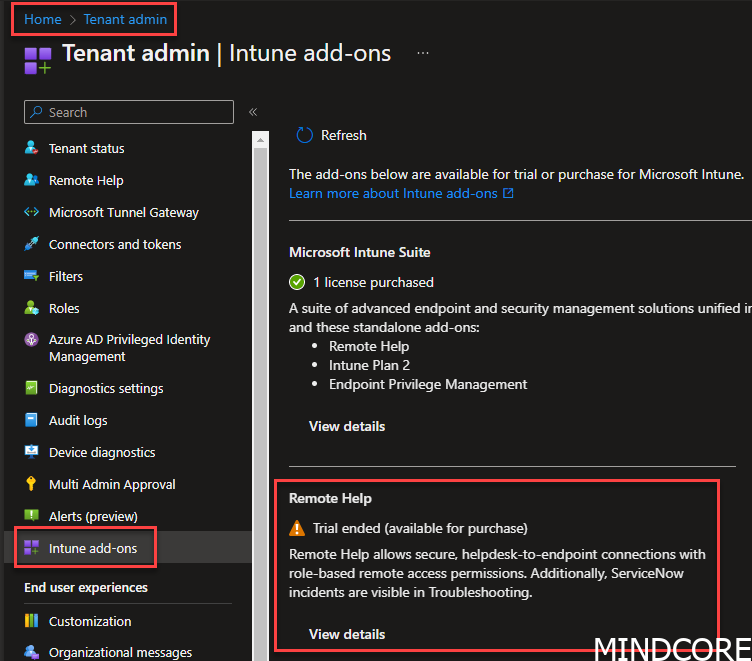
Before you can start utilizing Remote Help there is some prerequisites that you need to be aware of.
But on the other hand you could purchase a trial license. That’ll get you started (Remember to assign the licenses afterwards 🫡)
Configuring Azure backend
The first step in the process is to configure the Remote Assistance Service which is the backend service for Remote Help.
Open PowerShell with admin rights
Install-Module -name AzureADPreview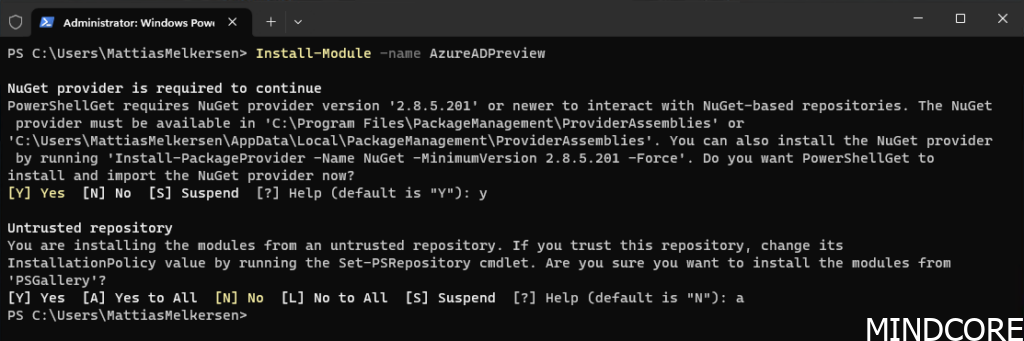
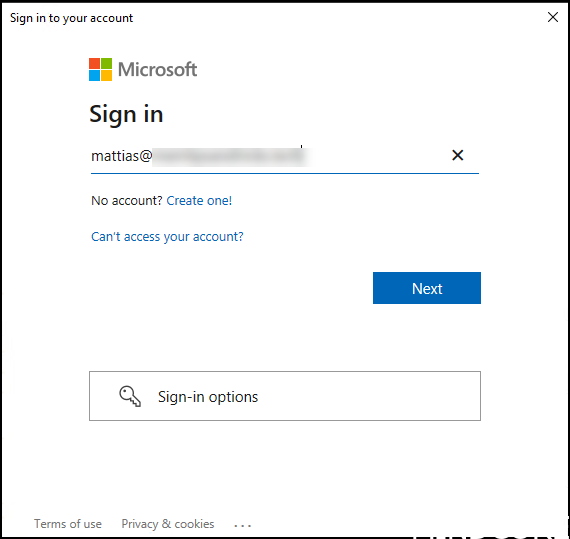
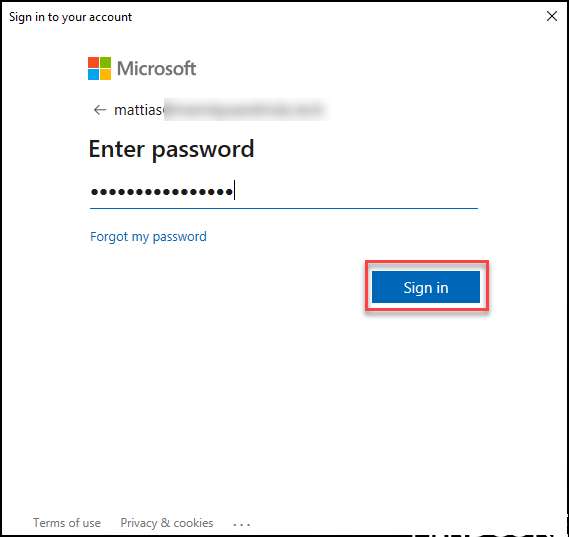
Connect-AzureAD
Authenticate with your azure admin account
Write PowerShell command
New-AzureADServicePrincipal -AppId 1dee7b72-b80d-4e56-933d-8b6b04f9a3e2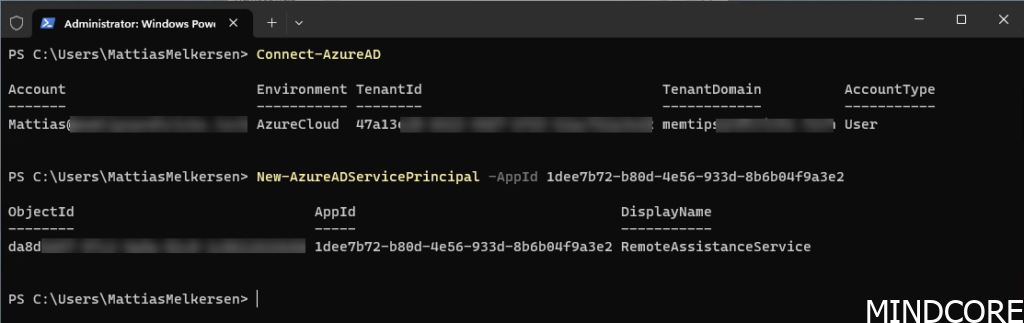
We successfully created a new enterprise application in our tenant associated with Remote Help. Time to verify that it was indeed created.
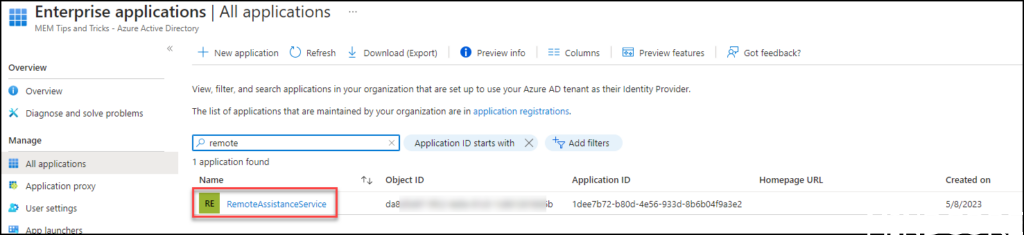
Go to the Azure portal.
In the portal click Azure Active Directory then Enterprise Applications on the filter Remove the “Application type==” and then search for RemoteAssistanceService you should be presented with below picture.
Configure Conditional Access
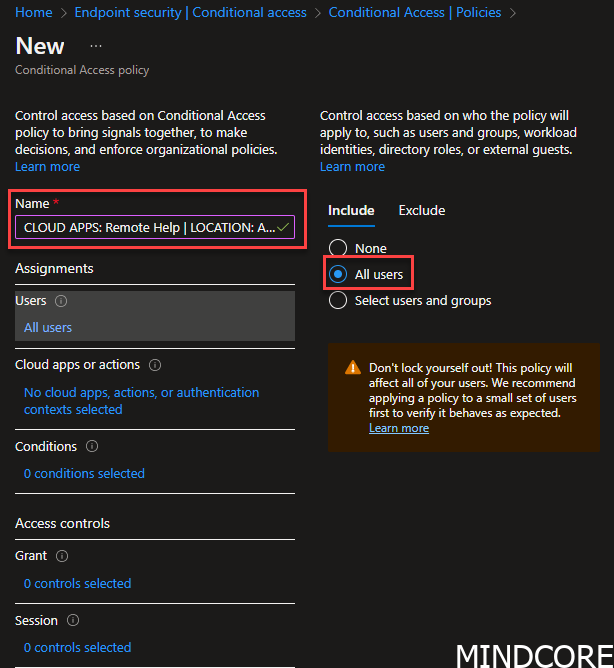
Head over to the Conditional Access portal
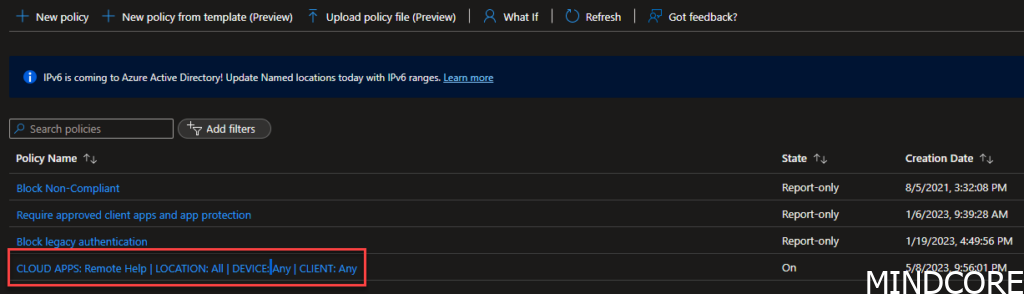
Hit that new button and give your Conditional Access policy a good name. A good name could be: CLOUD APPS: Remote Help | LOCATION: All | DEVICE: Any | CLIENT: Any
Add cloud apps RemoteAssistanceService
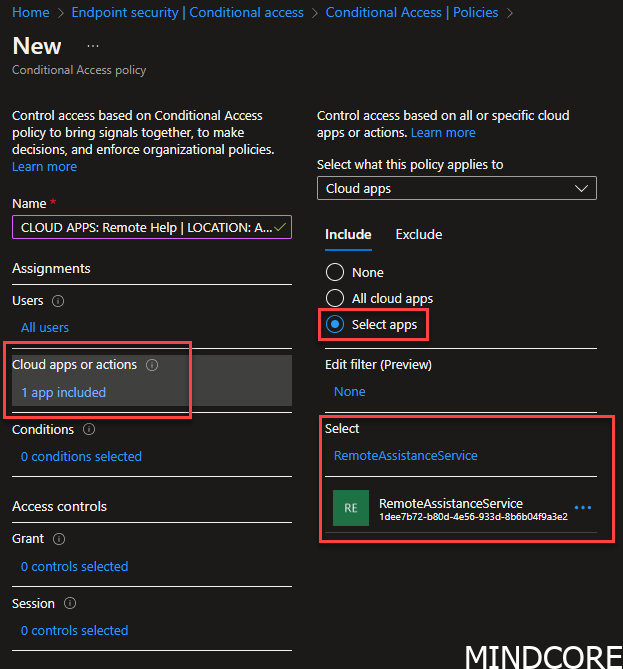
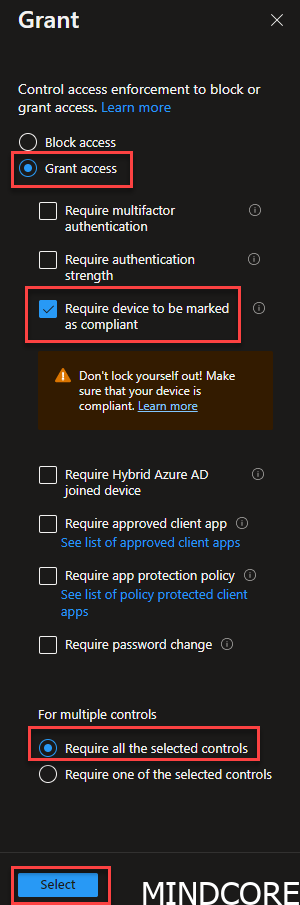
Go to Grant
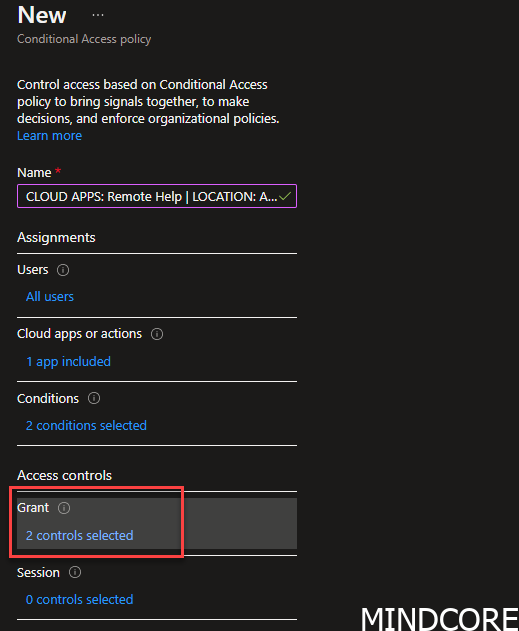
Add condition
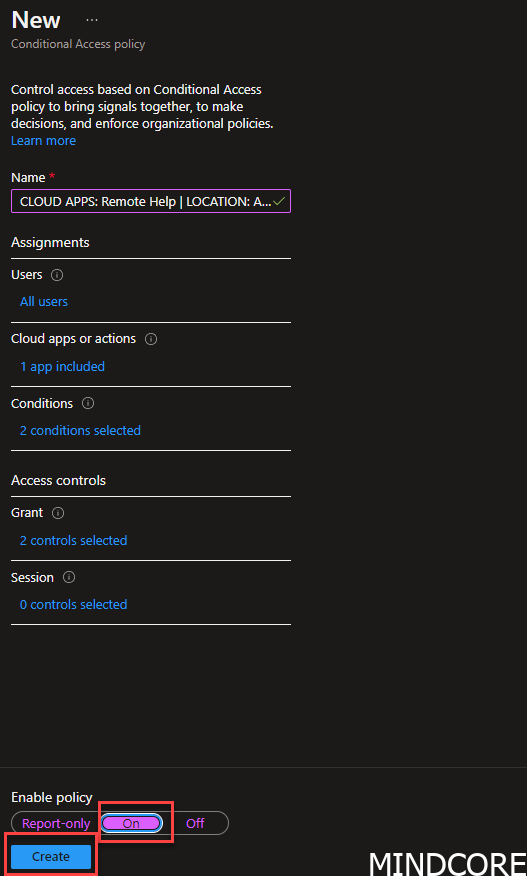
Set the policy to ON and press Create.
INFO:
Be careful to not lock yourself out. You should always put your CA policy in report-only mode before enforcing it!
And the result should look like this
End-user Experience
When a user works on a non-compliant device they will not be able to authenticate to remote help without using MFA
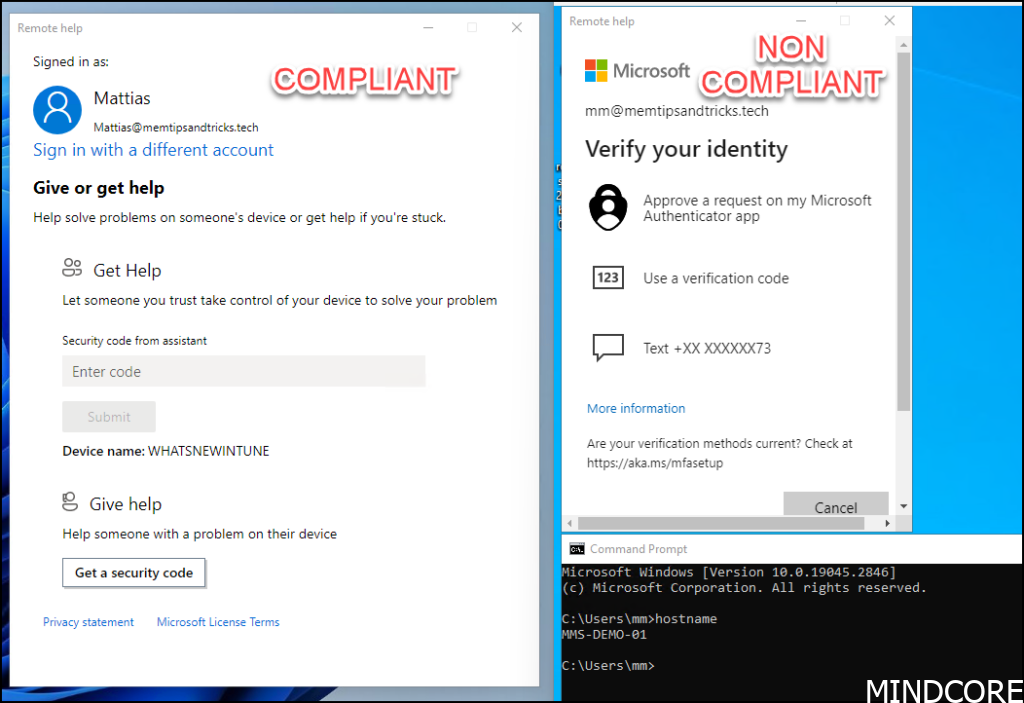
And since we required the device to be compliant we will actually be denied access.
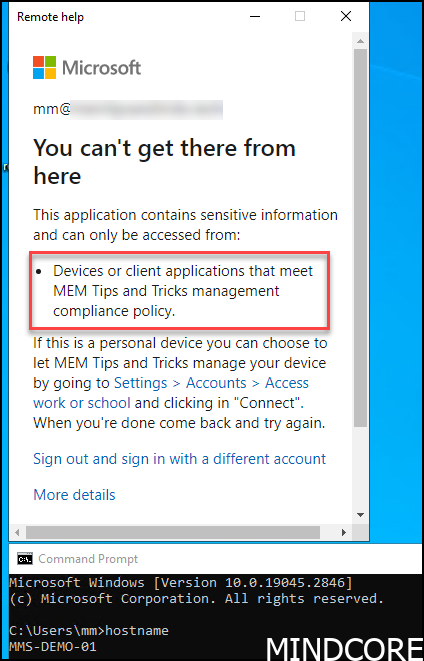
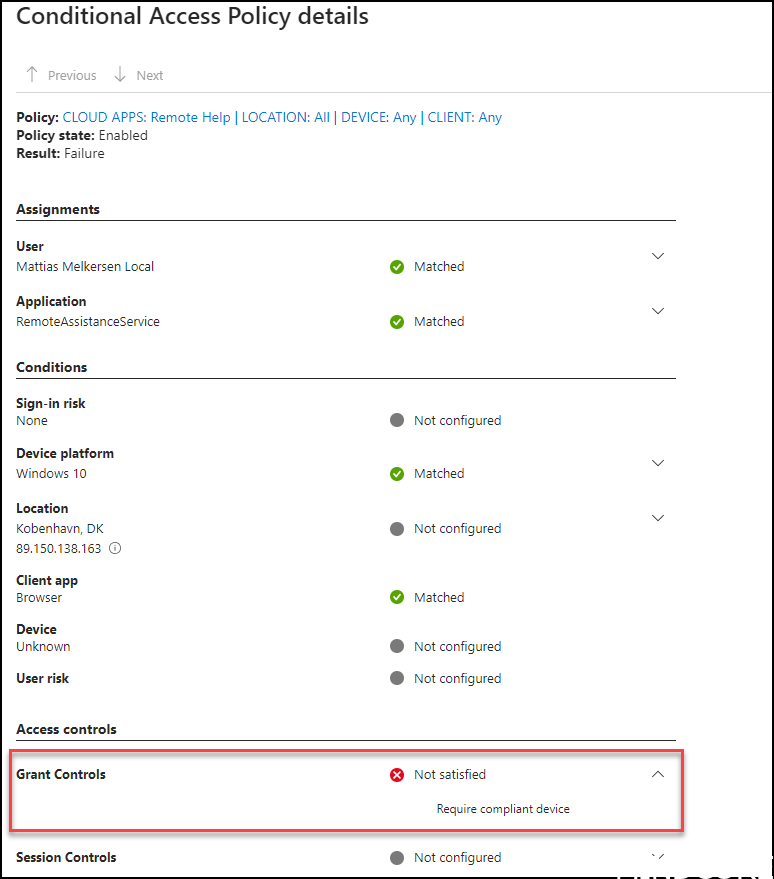
Blocking the device might be too harsh and you should always consider letting your end-user start remote help if they enter strong authentication. This should get you started to raise security around your remote help applications.
As a suggestion, you could add 2 controls to your CA. One requiring “authentication strength” and one requiring a “compliant” device and then “requires one of the selected controls” then you will be able to make sure users on non-compliant devices will always be prompted for strong authentication, which proves they are who they say they are.
Happy remoting!
Ressources:
Remotely assist users that are authenticated by your organization. | Microsoft Learn
Mattias Melkersen is a community driven and passionate modern workplace consultant with 20 years’ experience in automating software, driving adoption and technology change within the Enterprise. He lives in Denmark and works at Mindcore.
He is an Enterprise Mobility Intune MVP, Official Contributor in a LinkedIn group with 41.000 members and Microsoft 365 Enterprise Administrator Expert.
Mattias blogs, gives interview and creates a YouTube content on the channel "MSEndpointMgr" where he creates helpful content in the MEM area and interview MVP’s who showcase certain technology or topic.
Official Contributor here "Modern Endpoint Management":
https://www.linkedin.com/groups/8761296/














