In two of the latest we tested Azure Self-service password reset and integrated the feature with Windows 10:
http://blog.mindcore.dk/2019/03/azure-active-directory-azure-ad-self.html
http://blog.mindcore.dk/2019/03/azure-ad-password-reset-on-login-screen.html
This time let’s use the same user, and enable it to use Password-less phone sign-in with the Microsoft Authenticator app.
This feature is in public preview and you need to be aware of a couple of known issues :
AD FS Integration
When a user has enabled the Microsoft Authenticator password-less credential, authentication for that user will always default to sending a notification for approval. This logic prevents users in a hybrid tenant from being directed to ADFS for sign-in verification without the user taking an additional step to click “Use your password instead.” This process will also bypass any on-premises Conditional Access policies, and Pass-through authentication flows. The exception to this process is if a login_hint is specified, a user will be auto forwarded to AD FS, and bypass the option to use the password-less credential.
Azure MFA server
End users who are enabled for MFA through an organization’s on-premises Azure MFA server can still create and use a single password-less phone sign-in credential. If the user attempts to upgrade multiple installations (5+) of the Microsoft Authenticator with the credential, this change may result in an error.
Device Registration
One of the prerequisites to create this new, strong credential, is that the device where it resides is registered within the Azure AD tenant, to an individual user. Due to device registration restrictions, a device can only be registered in a single tenant. This limit means that only one work or school account in the Microsoft Authenticator app can be enabled for phone sign-in.
The last thing regarding Device Registration is regarding the mobile phone with the authenticator app installed.
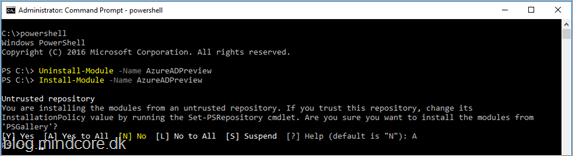
For the public preview, we must first add a policy via PowerShell to allow use of the credential in the tenant (Global administrator or security administrator needed).
We also need to ensure that we have the latest version of the Public Preview release of the Azure Active Directory V2 PowerShell Module.
So lets uninstall and reinstall by executing the following commands in an elevated PowerShell prompt.
Uninstall-Module -Name AzureADPreview
Install-Module -Name AzureADPreview
Now login to the Azure AD tenant with the command.
Connect-AzureAD
And enter credentials (Global administrator or security administrator needed).
Now we can create the Authenticator Sign In policy with the command.
New-AzureADPolicy -Type AuthenticatorAppSignInPolicy -Definition ‘{“AuthenticatorAppSignInPolicy”:{“Enabled”:true}}’ -isOrganizationDefault $true -DisplayName AuthenticatorAppSignIn
Since we are already enrolled in Azure Multi-Factor Authentication (MFA) and have the authenticator app installed with push notifications enabled we can enable phone sign-in in the app.
Find the account and use the down arrow (here marked in red).
Select Enable phone sign-in on the account.
Now enter the password for the user selected and sign-in.
We will get a notification on the same phone so approve the sign-in.
Select Register to register your phone device.
When device is registered use Continue.
Notice that the user now has an icon with a key, meaning that the account is setup for phone sign-in.
Let’s sign-in to the work account at office.com
We will the be prompted to send the notification to the phone, click Send notification.
After typing your username and clicking Send notification, an Approve sign in screen appears showing you a two-digit number and asking you to sign-in through the Microsoft Authenticator app. If you don’t want to use this sign in method, you can select Use your password instead, and sign in using your password.
On the Phone select the number requested and approve.
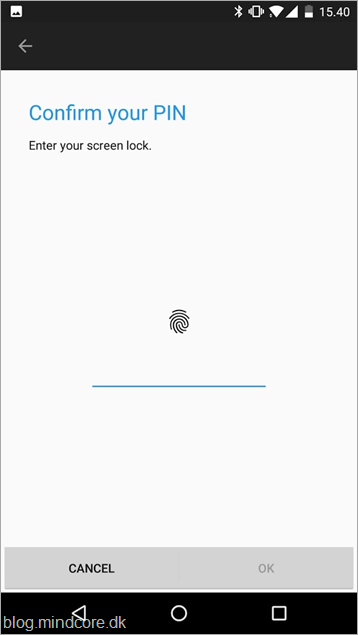
Use your phone’s PIN or your biometric key to complete the authentication.
To help protect your account, the Microsoft Authenticator app requires a PIN or biometric lock on your device.
And we are signed-in without the use of password.