One of the interesting solutions a lot of us has been waiting for is now in public preview – password-less sign-in with Azure Active Directory (Azure AD).
We have been able to use it with personal Microsoft accounts, but now we also can start testing with Azure AD accounts.
So lets give it at test spin.
I will try with an Yubico security NFC and by using the Microsoft authenticator app on a Windows 10 1903 device.
First lets enable the use of security keys for Windows sign ins.
Go to https://devicemanagement.microsoft.com and select Device enrollment.
Select Windows enrollment and Windows Hello for Business.
Select Properties and under settings enable Use security keys for sign-in, this will enable it for all but you can of course also assign it to specific users, devices, or groups, but for this test everyone is fine.
Registration features for FIDO2 security keys rely on the combined registration preview, so just like when we tested Self-service Password Reset, we will enable this.
Select Azure Active Directory and User Settings.
Select Manage settings for access panel preview features.
And then we enable the preview feature for registering and managing security info – enhanced, again for this test we will enable it for all users.
Still in Azure Active Directory under Security select Authentication methods.
Here lets enable FIDO2 Security key.
And also Microsoft Authenticator passwordless sign-in.
Now login to https://myprofile.microsoft.com with the test user.
Under Security info select Update info.
Select Add method, and notice that this user is already setup for the Microsoft Authenticator app (see http://blog.mindcore.dk/2019/03/azure-active-directory-azure-ad-self.html for more information regarding this setup).
Select the method Security key and Add.
Please note that if you try to do this in Chrome you will see this error, use the built-in Edge browser instead (the new Edge browser build on Chromium is also not working for now).
Select USB device
Now we can inset the security key and select Next.
If the security key is not already inserted you will get this prompt.
Insert the security key and enter new PIN for the key.
If you security key already has a PIN you will be prompted for this PIN.
We then need to perform the required gesture for the key – here touch.
Then give the security a Name so that we can identify it if we have multiple.
And finally we just have to press Done.
And we now have the security method setup, also note that the Authenticator app is setup for phone sign-in as this is required to test the password-less sign-in to Office 365 or Azure (see http://blog.mindcore.dk/2019/04/password-less-phone-sign-in-with_8.html for more information about enabling phone sign-in in the app).
Now lets try to sign-in to Windows 10 with the security key, select FIDO security key as sign-in option and insert the key.
Then we are prompted for the security key PIN.
And last the required gesture for the key – here touch.
And then we have the Windows desktop available
Now lets try to sign-in to the Office 365 portal with the Authenticator app, this is just like the sign-in with the person Microsoft account, you get a number.
And you then need to select that number on you phone.
and confirm with PIN or biometric on your device.
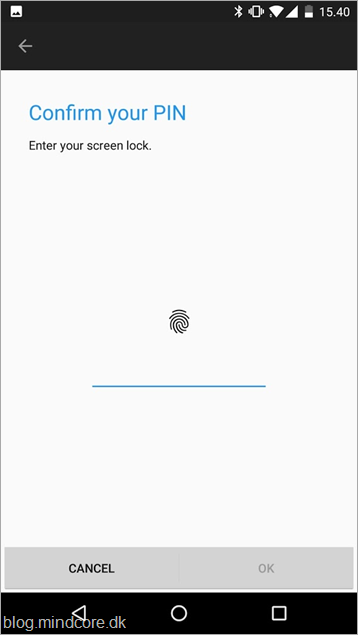
An then we are in the portal.
We should also be able to use the security key for signing in to the Office 365 portal or Azure portal in Edge and Firefox, but at the time of writing I only get the option in Firefox.
And it fails with this error The security key doesn’t look familiar.
After setup we can manage the security key in Windows settings.
But at the time of writing, it fails if I try to reset my Yubico security key with the error Could not complete security key reset.
The Yubikey Manager can reset the key when started as administrator.
We are on the right track, now test in your own environment.













