This time we will try to extend our Azure AD directory with a new attribute, we will in a later post use this attribute for dynamic groups and team access.
But let’s get started, we will in this test attach the extension attribute to users, but it can be assigned to other objects as well.
We will create and set the attribute with PowerShell, in order to do that you will need the AzureAD module.
You can always see latest version of both the General Availability version (AzureAD module) and the preview version (AzureADPreview module) here https://docs.microsoft.com/en-us/powershell/azure/active-directory/ad-pshell-v2-version-history?view=azureadps-2.0
To see your current version use the commands:
Import-Module -Name AzureAD or Import-Module AzureADPreview (depending on which module you want to use)
Get-Module -Name AzureAD or Import-Module AzureADPreview (depending on which module you want to use)
You can always just uninstall and reinstall the module to be sure you got the latest version. (elevated)
Uninstall-Module -Name AzureADPreview
Install-Module -Name AzureADPreview
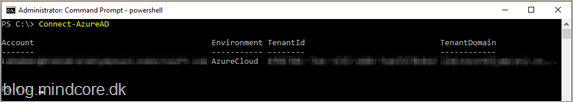
Now login to the Azure AD tenant with the command.
Connect-AzureAD
And enter credentials.
Now we can create the new extension property, this must be done for a specific application, in this case we will just create a placeholder application.
$App = New-AzureADApplication -DisplayName "Mindcore Azure AD Properties" -IdentifierUris https://dummy
Before we can create a a new extension property, we need to create a service principal for the application.
New-AzureADServicePrincipal -AppId $App.AppId
Now we are able to create the new attribute.
New-AzureADApplicationExtensionProperty -ObjectId $App.ObjectId -Name "MyAttribute" -DataType "String" -TargetObjects "User"
The following data types are supported:
- Binary
- Boolean
- DateTime
- Integer
- LargeInteger
- String
Notice that the Name of the new attribute use the AppID (without hyphens) from our application, the exact value of the name will therefore be different for each applications we create.
We can get the exact Appid used without the hyphens with the command:
(get-AzureADApplication -SearchString "Mindcore Azure AD Properties").Appid.replace("-","")
Using this appid we can now assign a value to the attribute:
$Appid = (get-AzureADApplication -SearchString "Mindcore Azure AD Properties").Appid.replace("-","")
Set-AzureADUserExtension -objectid mytest@lohmann10.blemmail.dk -ExtensionName "extension_$($Appid)_MyAttribute"
-ExtensionValue "MyValue"
The above commands will give the same result as if we just copied the extension name like here:
Let’s see the extension properties on the same user mytest@lohmann10.blemmail.dk with the command.
Get-AzureADUser -ObjectId mytest@lohmann10.blemmail.dk | Select -ExpandProperty ExtensionProperty
As we can see the user mytest@lohmann10.blemmail.dk now has an attribute called extension_c37cb740676d4d5c992f8c55374abe81_MyAttribute with the value MyValue.
Stay tuned, in the next blogpost we will use this attribute to control access to a team inside Microsoft Teams.