This time we will take a closer look at the new group writeback functionality in Azure AD.
I really think this will open a lot of possibilities also on-premises.
Prerequisites
- Azure AD Premium license
- Azure AD Connect version 2021 December release or later.
- Enable Azure AD Connect group writeback
But let us get started, first thing we will do is to create an OU to hold the groups written back from Azure AD. You can call the OU any name you want.
Also be aware that groups written back from Azure AD will have a source of authority in the cloud. Meaning that any changes made on-premises to groups that are written back will be overwritten on the next Azure AD connect sync cycle.
For this test, we will create three test users.
And to test dynamic groups we will set a postal code on User2.
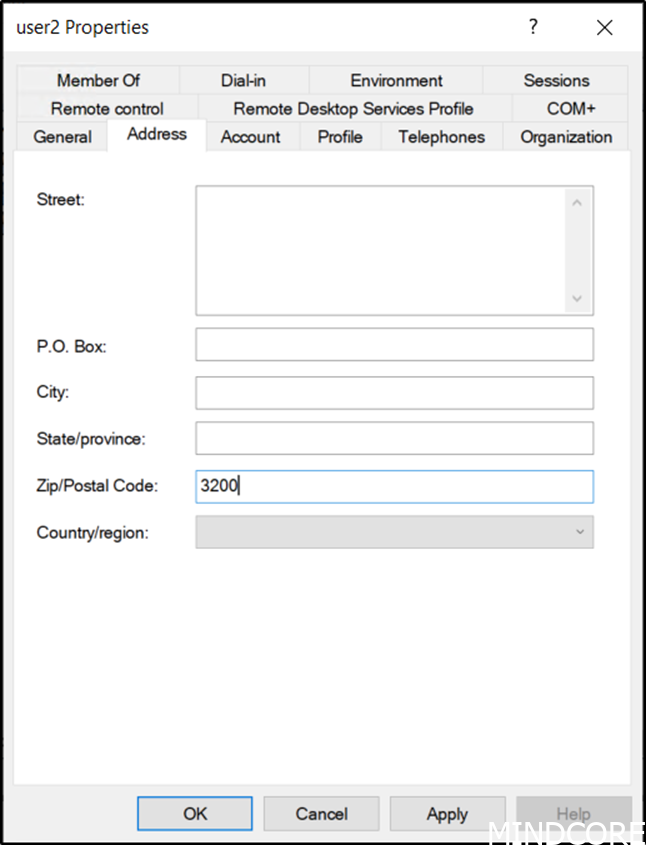
Enabling this new feature requires two steps, first step is done via Azure AD Connect and enables the original group writeback feature.
In Azure AD connect select Customize synchronization options.
In OU filtering make sure to select the Write Back OU we created earlier.

In Optional feature enable Group writeback.

The yellow exclamation mark is because our on-premises directory has not been extended with Exchange schema changes. For this test it is not required.

Select the OU we created earlier and select the option Writeback Group Distinguished Name with cloud Display Name.
This will make it easier to find groups in because the group name will be included.
Default format will be:
CN=Group_3a5c3221-c465-48c0-95b8-e9305786a271, OU=WritebackContainer, DC=domain, DC=com
If Writeback Group Distinguished Name with cloud Display Name is selected the name will be added:
CN=Administrators_e9305786a271, OU=WritebackContainer, DC=domain, DC=com

Next, we need an Enterprise admin to set required permissions.
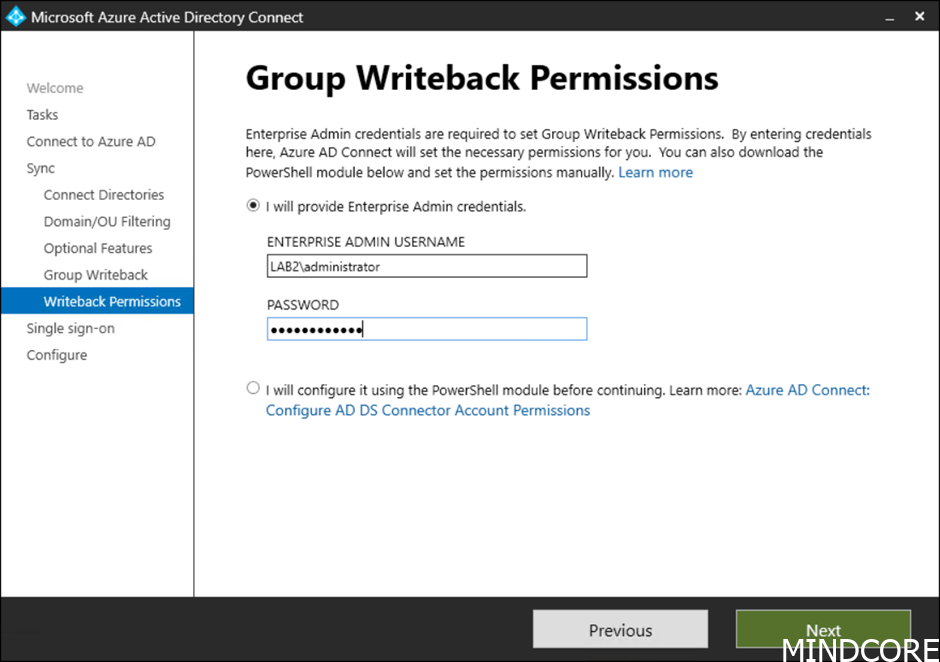
With the Azure AD connect step in place, we can do step 2 which will enabling group writeback (V2) using PowerShell.
Check if synchronization is running with the PowerShell command Get-ADSyncConnectorRunStatus, this command should return nothing as shown here

And not a busy connector as shown here:
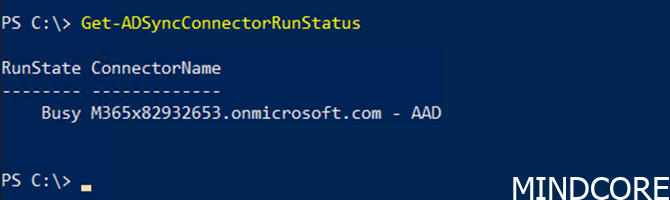
When we are sure that no synchronization is running, we run the following PowerShell commands.
Set-ADSyncScheduler -SyncCycleEnabled $falseImport-Module 'C:\Program Files\Microsoft Azure AD Sync\Bin\ADSync\ADSync.psd1'Set-ADSyncAADCompanyFeature -GroupWritebackV2 $trueSet-ADSyncScheduler -SyncCycleEnabled $true
Now let us create a dynamic security group in Azure AD.
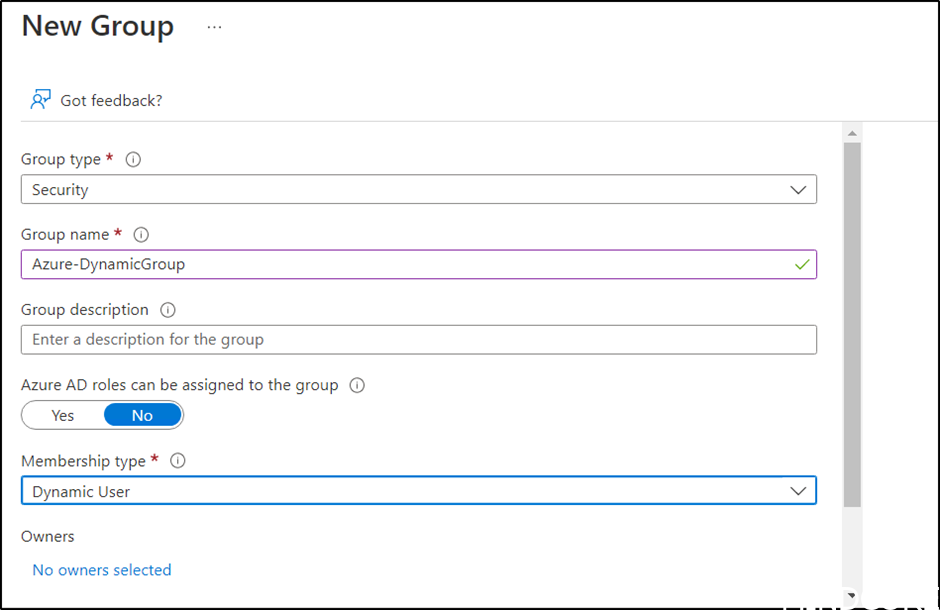
And include objects with postal Code set to 3200 as we did on the test user.

In properties on the group set Group writeback state to security.

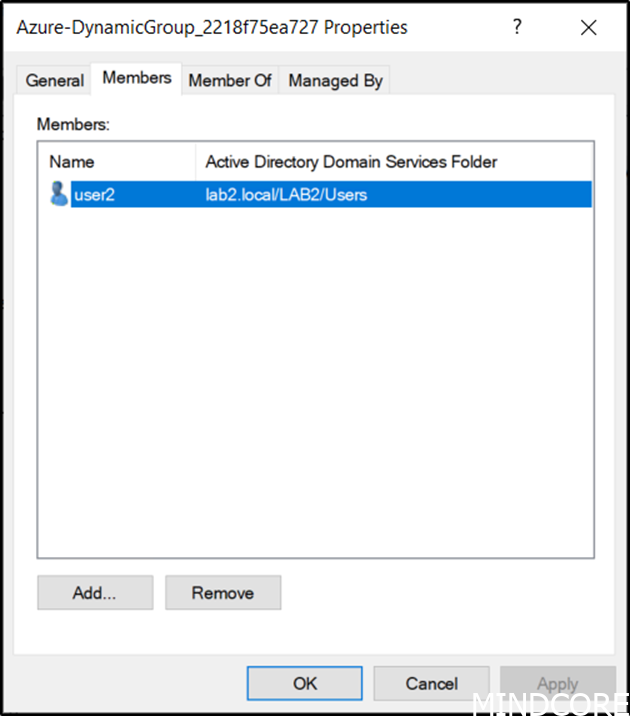
Then wait for the dynamic group to update and as show here the user is added to the group.

And after next Azure AD connect sync cycle, we also see the group in AD with user2 as a member.
Azure AD dynamic groups in on-premises AD, this will give us a lot of possibilities 😊
Now let us try the same with a Privileged Access Group, because this could have an even bigger impact.
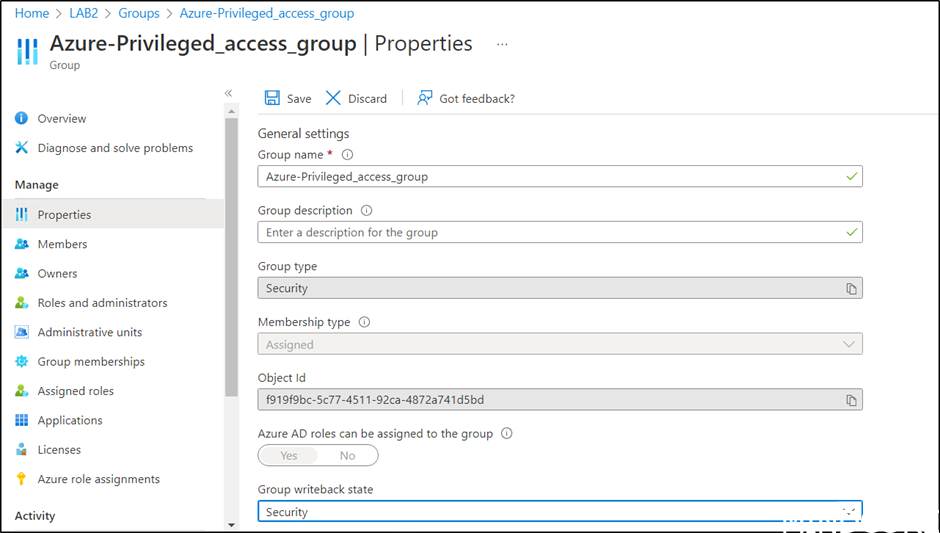
Remember to enable privileged access.

For the test we will grant an eligible assignment for test user1.

In order to test it we will login with user1 and Activate our assignment.

Enter why we need to activate our assignment – no good reason here 😊
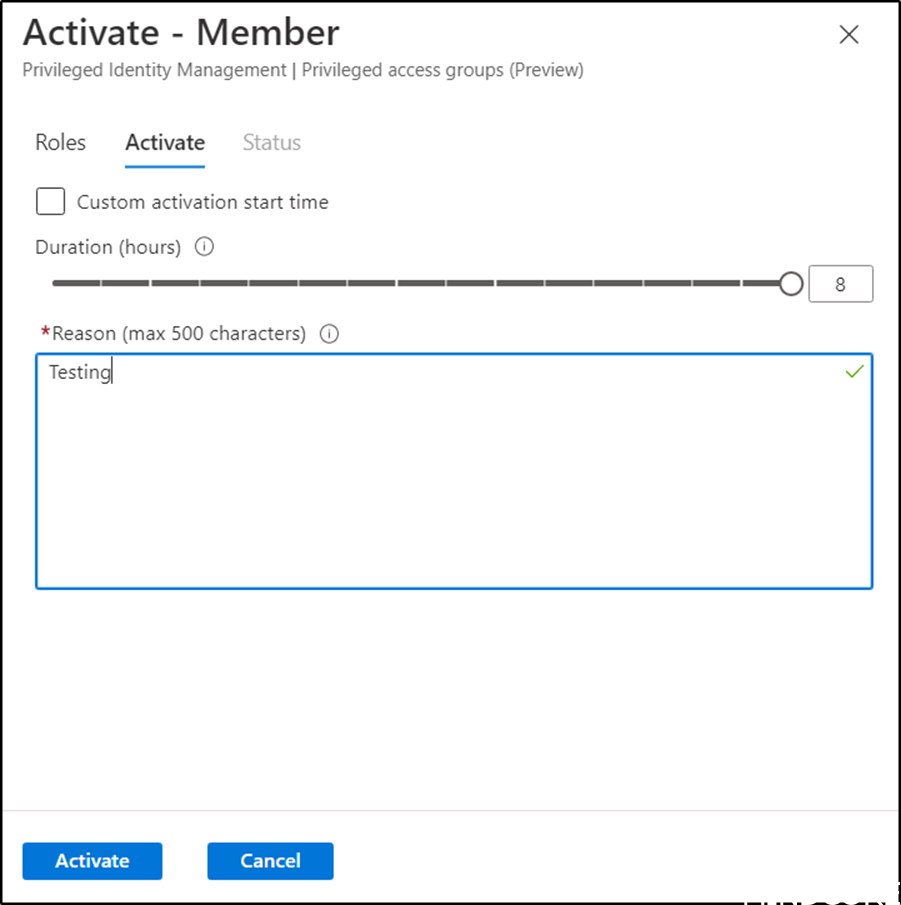
Wait for activation.
And then User1 is added to the group.
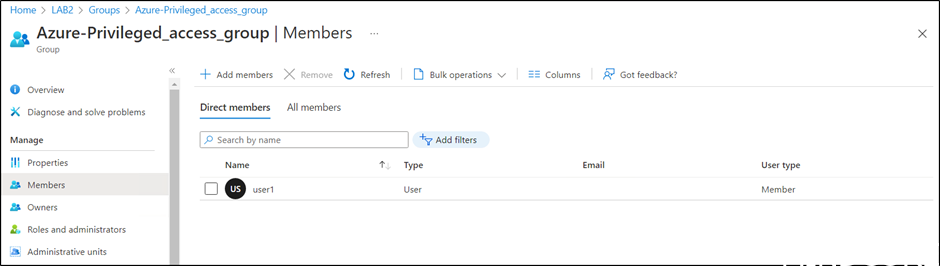
After next Azure AD connect sync cycle, the group is in AD with user1 as a member.

Next step is to deactivate the active assignment.

Wait for deactivation.
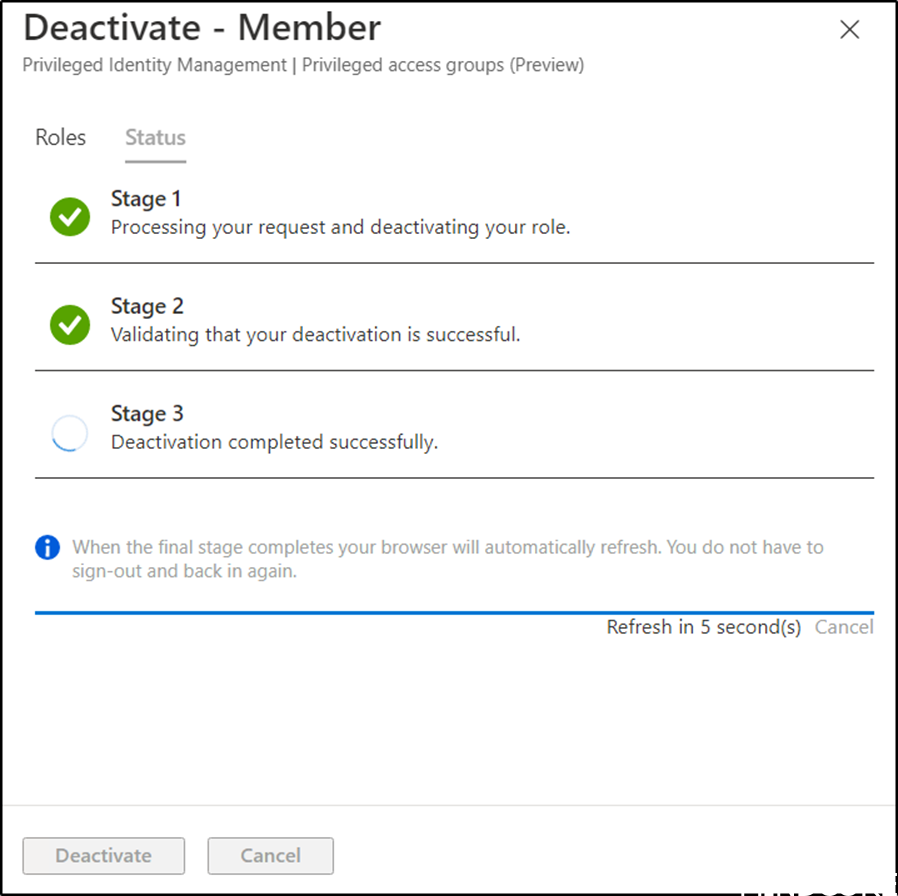
User1 is no longer in the Azure AD group.
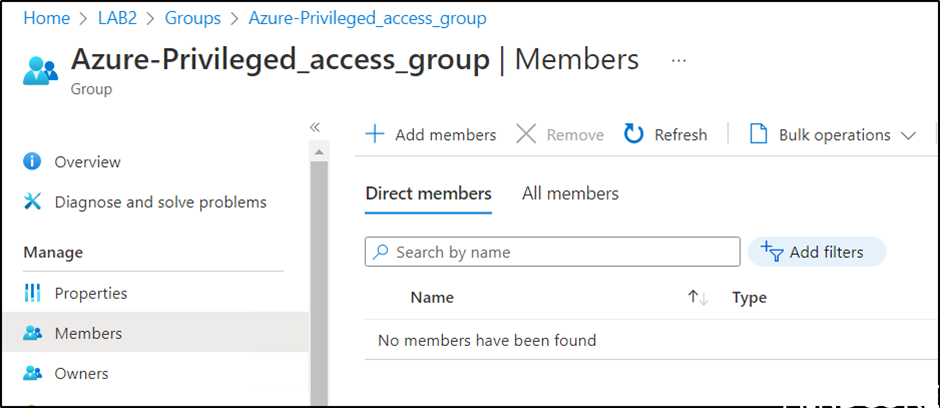
After next Azure AD connect sync cycle, user1 is no longer member of the group.

Please also note that we now have to new Columns we can select in the admin center.
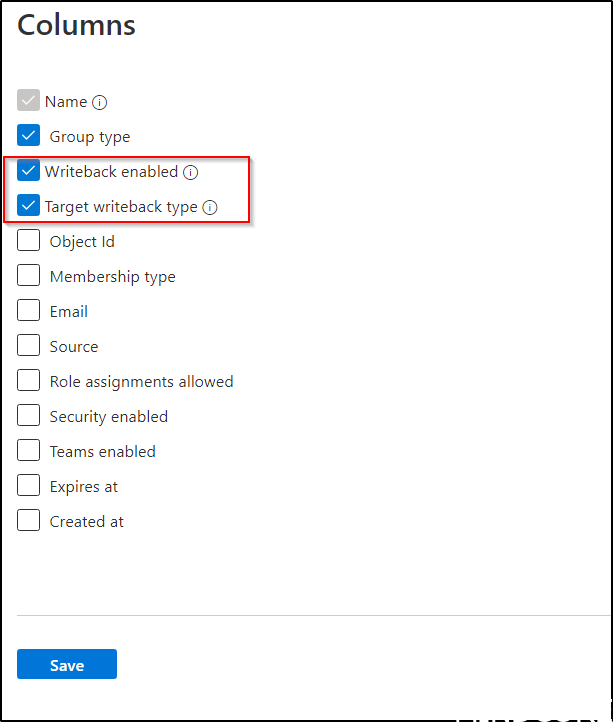
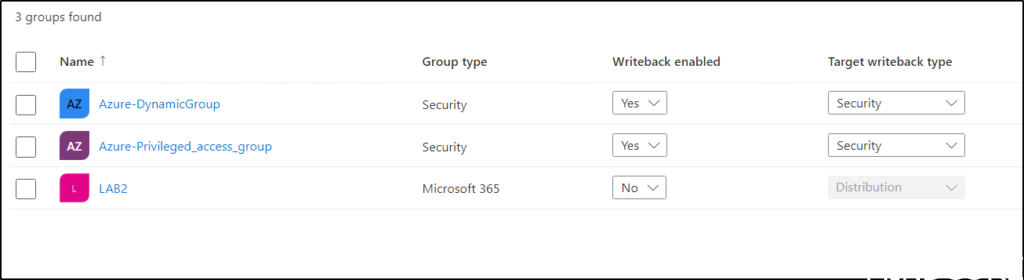
This will allow us to control writeback type and if writeback is enabled directly in the group view.
The new group writeback feature has huge possibilities, so until next time – happy testing 😊
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-group-writeback-v2













