We often get the question how to we setup Azure AD B2B direct connect with Mindcore.
So why not create a blog post regarding this topic, that also show the required setup.
Why do we want to do this in the first place?
Because we want to use Shared Channels in Microsoft Teams https://learn.microsoft.com/en-us/microsoftteams/shared-channels
In Azure AD we can use External Identities cross-tenant access settings to manage how we can collaborate with other Azure AD tenants through B2B collaboration and B2B direct connect.
Cross-tenant access settings will allow granular control over how external tenants can collaborate with you tenant (inbound access) and how your users can collaborate with external tenants like Mindcore (outbound access). These settings will also let you trust multi-factor authentication (MFA) and device claims.
In this post I will show you how to setup Azure AD B2B direct connect (both ways) with an external organization like Mindcore and how to trust MFA from the external organization (Mindcore).
First step is to go to the Azure AD Portal and select External Identities.
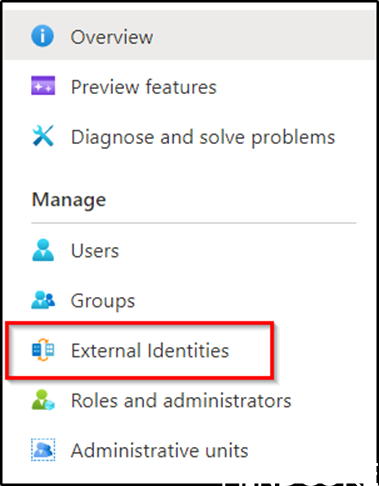
Next, we select Cross-tenant access settings – Organizational settings – + Add organization
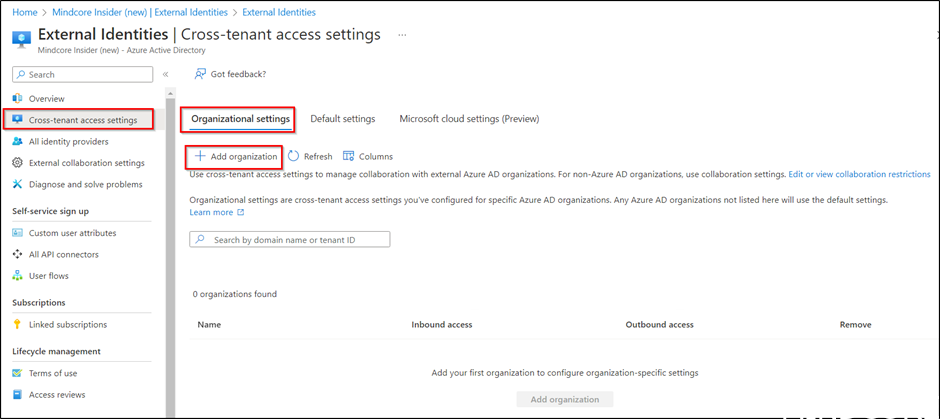
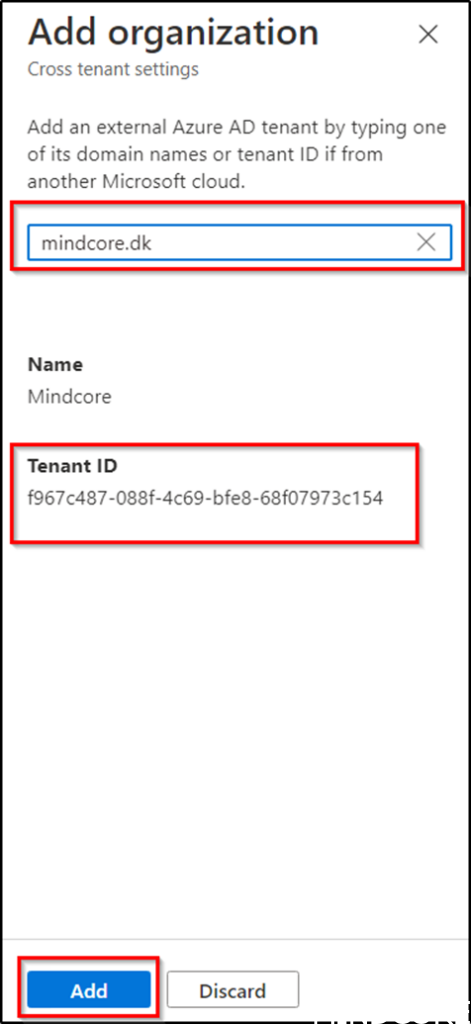
Enter the external domain you want to use Azure AD direct connect with (mindcore.dk) and notice that the tenant ID is automatically resolved. Then click Add.
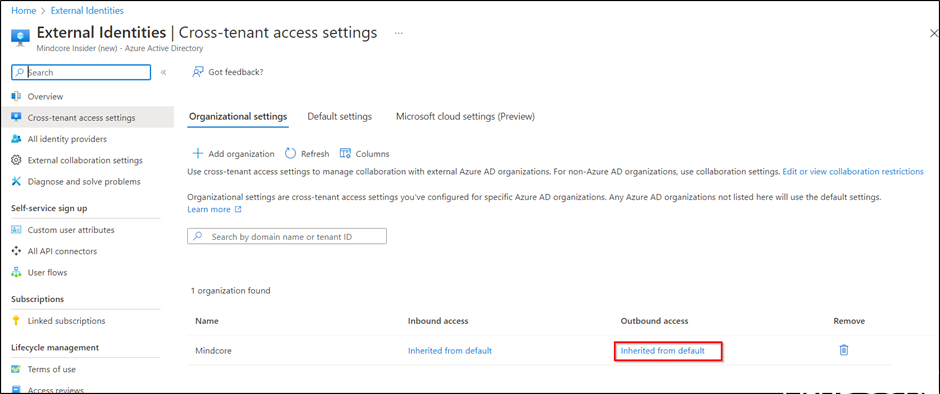
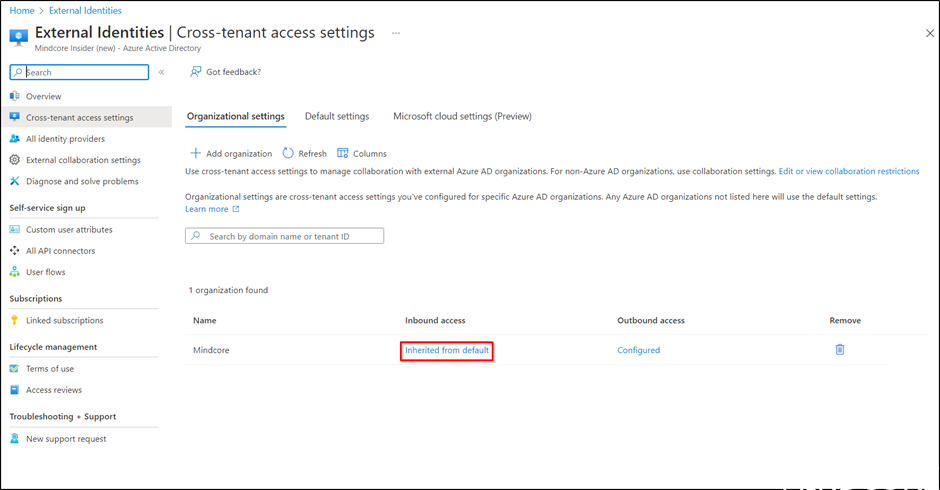
At the organization you wish to connect with and under Outbound access select Inherited from default.
Select B2B direct connect (important because this is used for shared channels)and Customize settings. Under Access status select Allow access, and for this example we will allow All our users (Mindcore insider is in this example your tenant).
Save the settings.
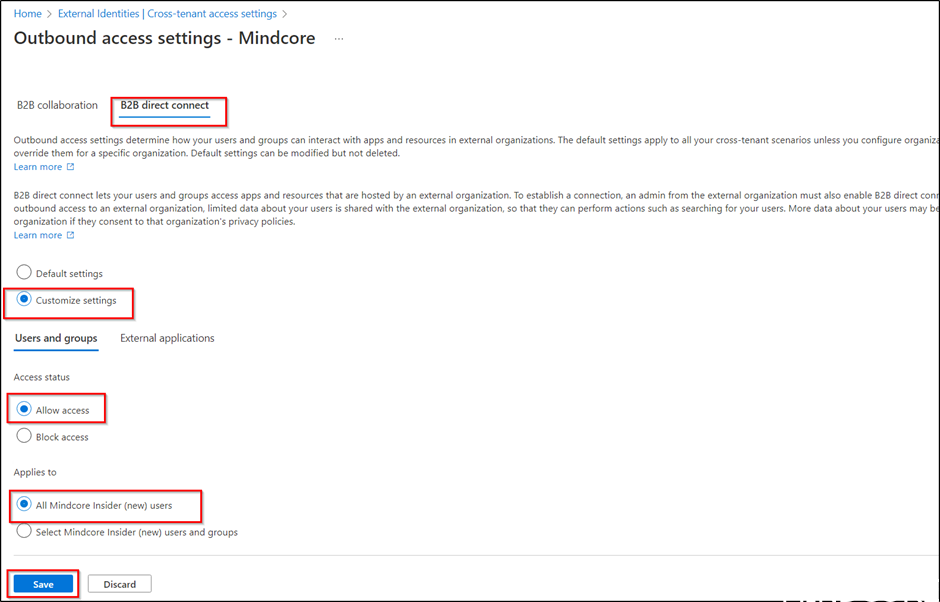
This is the only thing you need to do if you wish to access a shared channel in Mindcore’s tenant (the external tenant), Mindcore – the External tenant must allow inbound access in their tenant, and if you plan to allow Azure AD B2B direct connect both ways you must also configure inbound access as shown here.
At the organization you wish to connect with and under Inbound access select Inherited from default.
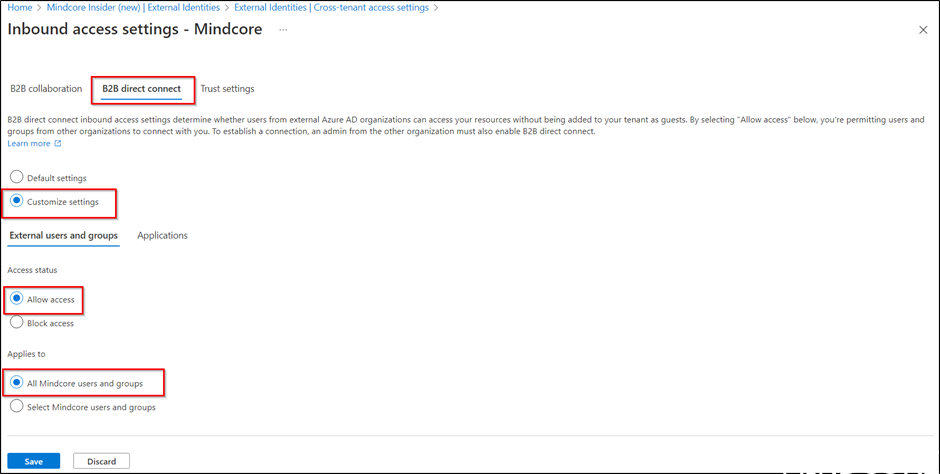
Select B2B direct connect and Customize settings. Under Access status select Allow access, and for this example we will allow All Mindcore users and groups.
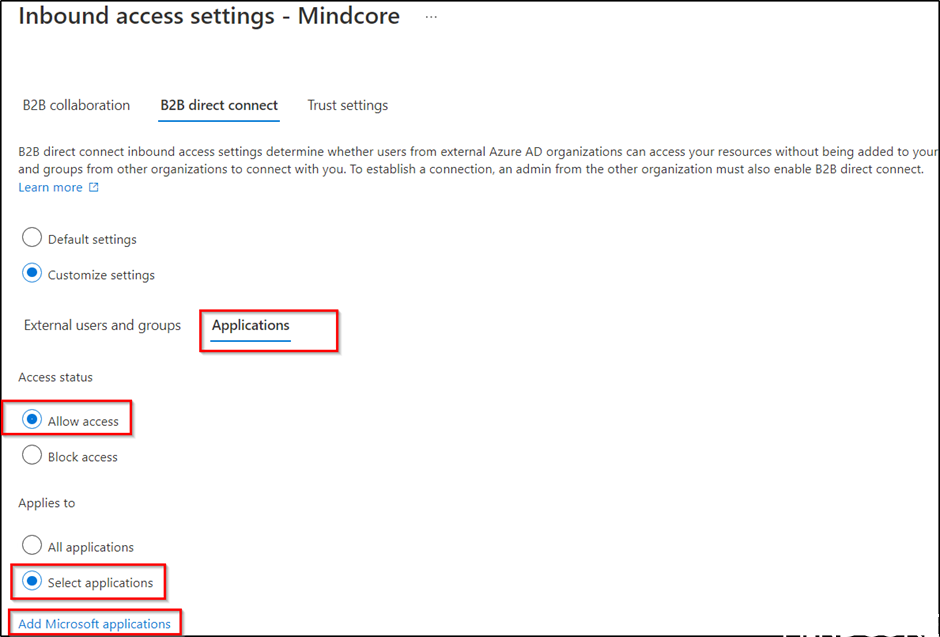
Select Applications and under Access status Allow access. We will also only allow this for Office 365 access, click on Select Applications.
Select Office 365 and click on Select.
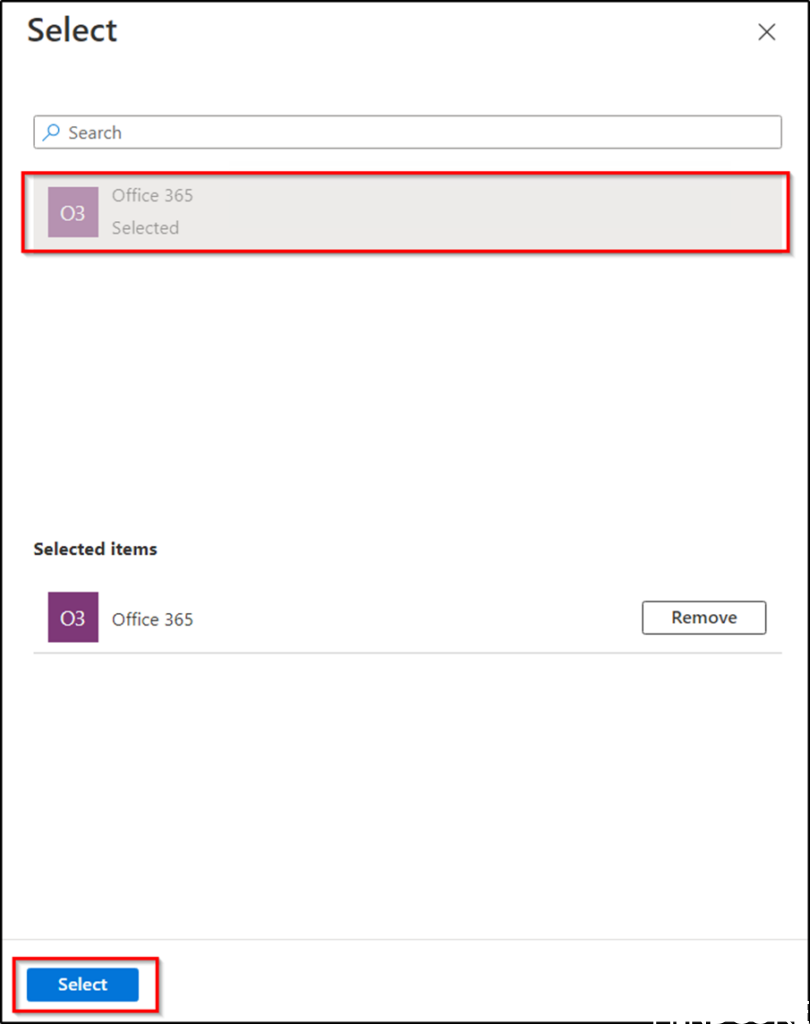
Save your changes.
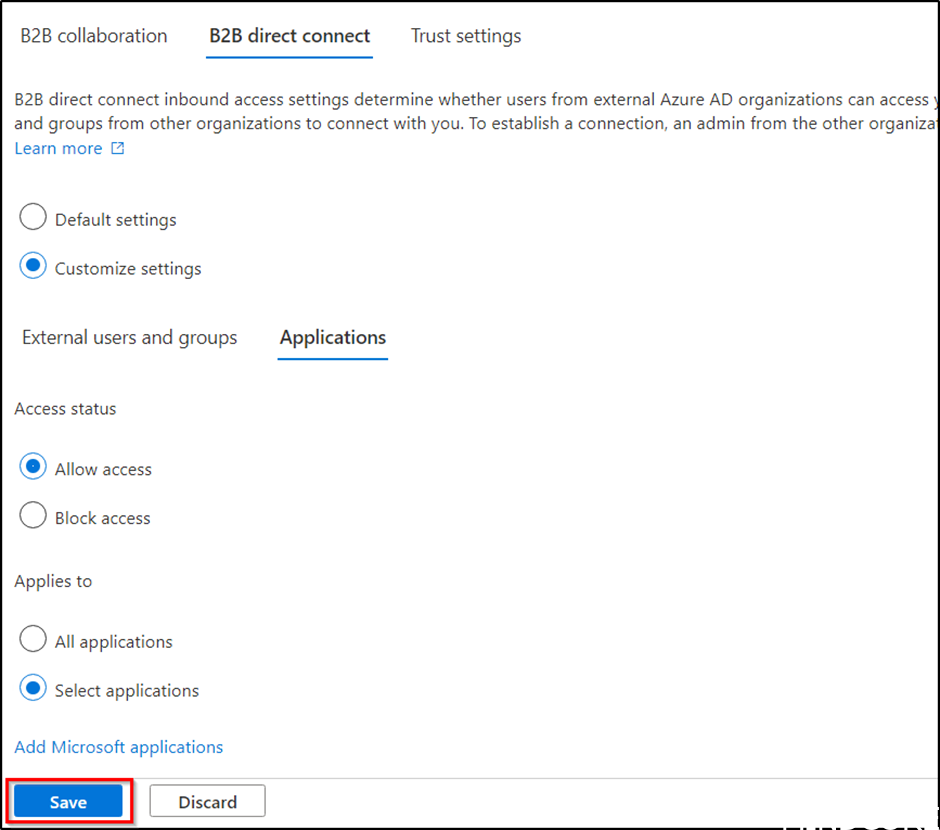
In this example we will also allow MFA from the external organization (Mindcore), so that we access MFA from the Mindcore tenant (the external tenant).
Select Trust settings and Customize settings and select Trust multifactor authentication from Azure AD tenants.
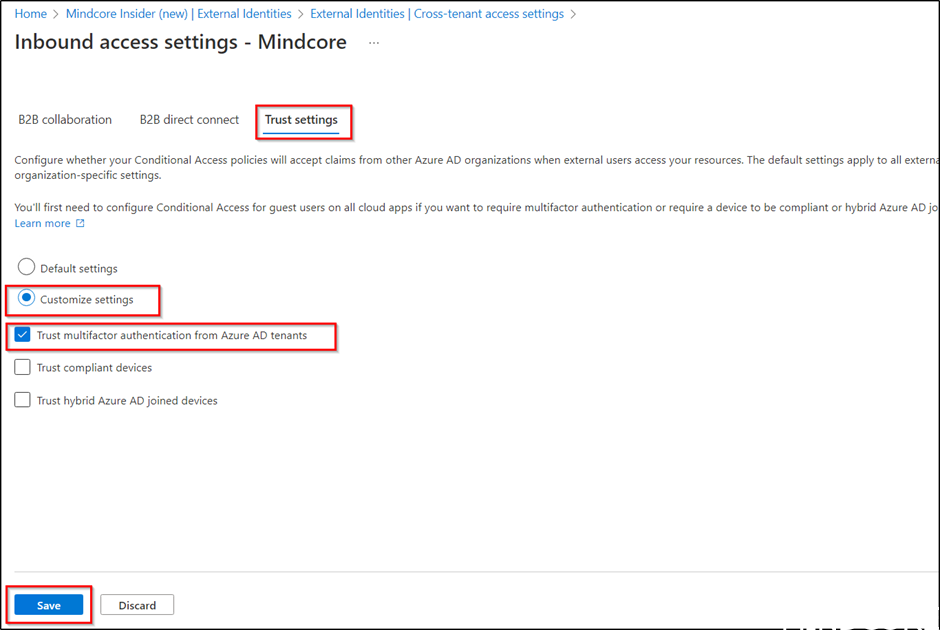
For more information please read this documentation from Microsoft https://learn.microsoft.com/en-us/azure/active-directory/external-identities/cross-tenant-access-overview













