We now have Azure AD Password Protection generally available, this will allow us to eliminate easily guessed passwords. By using it we can lower the risk of password spray attacks.
Password spraying is using a large number of usernames and loops them with a single password, this will give a low number of passwords attempted. This method can avoid password lockouts, and is often effective uncovering weak passwords.
So no reason not to implement Azure AD Password Protection, if you have the license.
We can use Azure AD Password Protection if you are using cloud only or On-premises Active Directory.
Let get some facts on the table first:
- Domain controllers never have to communicate directly with the internet.
- No new network ports are opened on domain controllers.
- No Active Directory schema changes are required.
- No minimum Active Directory domain or forest functional level is required.
- The software doesn’t create or require accounts in the Active Directory domains that it protects.
- User clear-text passwords don’t leave the domain controller during password validation operations or at any other time.
- Azure AD Premium is required, when combining with on-premises.
Now let’s test with an On-premises Active Directory and make sure our users aren’t using common passwords or passwords that are known to be included in recent data breaches.
In Azure AD under Security select Authentication methods.
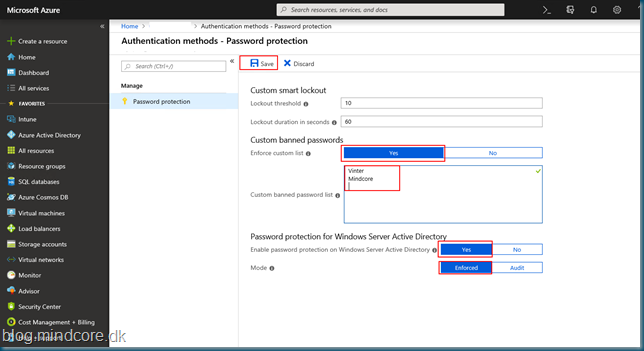
Enable the custom list by selecting Yes at Enforce custom list and enter your own banned passwords.
Then we will enable the on-premises support by selecting Yes at Enable password protection on Windows Server Active Directory.
The recommendation is to start with Audit mode, but for this test we will go for Enforced.
Then Save the setup.
Next step is to install and configure the proxy service for password protection, this should off course be done on at least two servers for redundancy. The proxy server requires Internet connectivity so a DC is not the recommended server for this, but since this is a test we will install both the proxy service and the domain controller agent on the same DC in the domain.
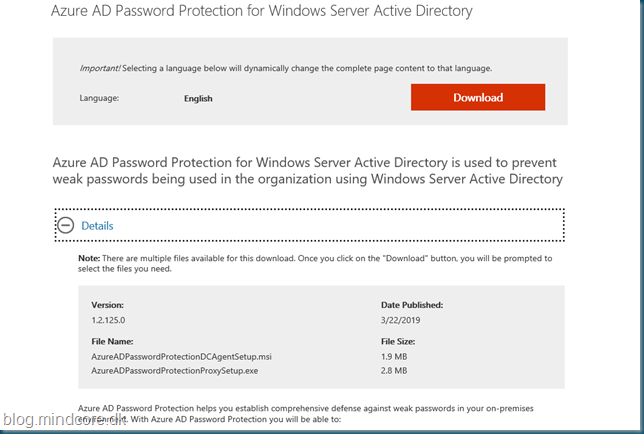
Download the required files from here https://www.microsoft.com/en-us/download/details.aspx?id=57071
First we install the proxy service.
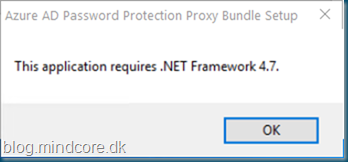
This service requires .Net Framework 4.7, otherwise you will see this information.
So let’s install it from here http://go.microsoft.com/fwlink/?linkid=825298
Start Proxy setup by using the downloaded file AzureADPasswordProtectionProxySetup.exe
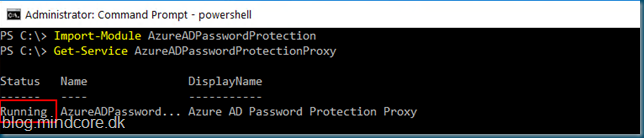
With an elevated powershell command promt (use a domain admin), we will first check the status of the proxy service.
Import-Module AzureADPasswordProtection
Get-Service AzureADPasswordProtectionProxy
Status must be running.
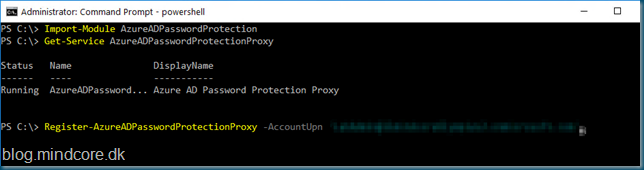
We then need to Register with Azure AD.
Register-AzureADPasswordProtectionProxy –AccountUpn ‘GlobalAdmin@mydomain.ext’
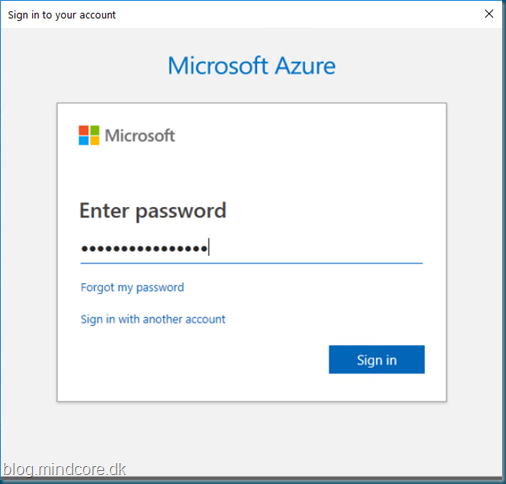
Sign in with your global administrator password, and expect it to take some time before it completes.
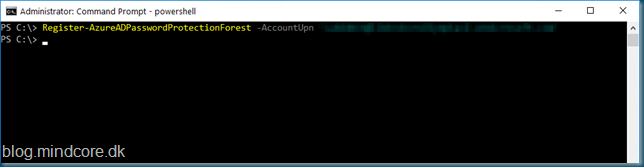
Then the forest with the command:
Register-AzureADPasswordProtectionForest –AccountUpn ‘GlobalAdmin@mydomain.ext’
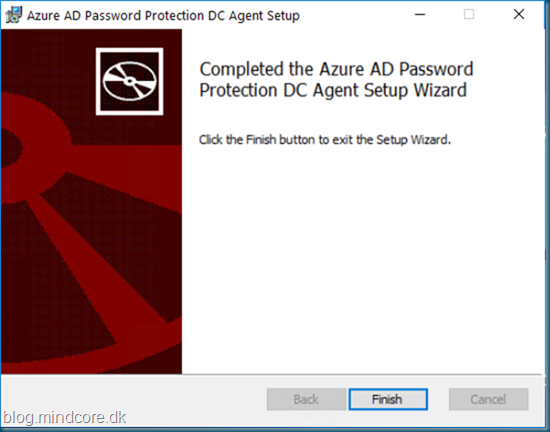
Start the DC agent setup by using the downloaded file AzureADPasswordProtectionDCAgentSetup.msi
A restart of the DC is required.
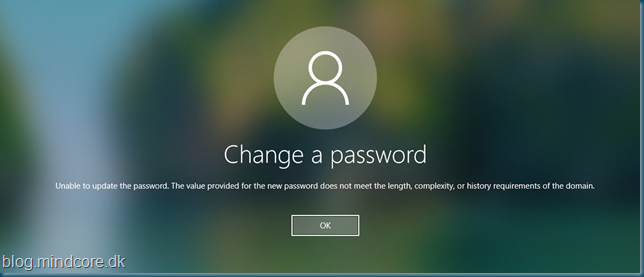
When a password is rejected by the Azure AD Password Protection DC Agent, the user will see a standard password change message, so you will not know why the password has been rejected:
Now test in your own environment.